 Download topic as PDF
Download topic as PDF
Configure the Splunk Add-on for VMware to collect data
Configure the Splunk Add-on for VMWare to collect Data Collection Node and Virtual Center data. Identify the data types that you want to collect, such as performance, inventory, or hierarchy data, from the following list.
- vCenter logs (Intermediate Forwarder/Syslog Forwarder)
- ESXi logs (Intermediate Forwarder/Syslog Forwarder)
- Performance Metrics, Inventory, Tasks (vCenter API collected by Data Collection Node)
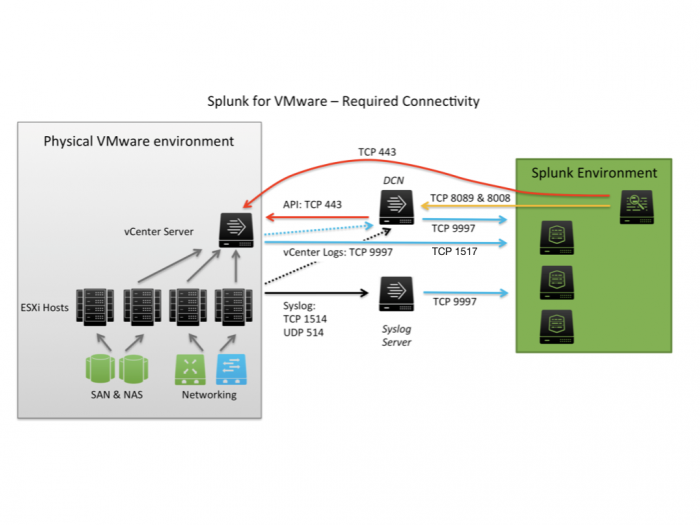
This table lists the components that communicate with each other and the ports they use to communicate.
Configure collection of Performance, configuration, and event data
Validate time synchronization
Verify time synchronization throughout your environment to improve visibility into application and operating system health. Check the time synchronization for the following components in your environment.
- Hosts
- Splunk Enterprise search head and indexers
Consider using NTP or VMware host/guest time synchronization.
|
PREVIOUS Install the Splunk Add-on for VMware in an on-premises environment |
NEXT Configure the Splunk Add-on for VMware to collect data from vCenter logs |
This documentation applies to the following versions of Splunk® Supported Add-ons: released
Feedback submitted, thanks!