How devices authenticate to your Splunk platform with SAML authentication
Security Assertion Markup Language (SAML) authentication uses JSON Web Token (JWT) to securely authenticate mobile devices to your Splunk platform. To learn more about how JWT works and how to set up JWT, see Set up authentication with tokens.
The following diagrams illustrate how mobile client devices authenticate to the Splunk Platform through a supported identity provider (IdP). Splunk Cloud Gateway performs validation and encryption. Spacebridge, a secure intermediary component, routes the credentials bundle back to the client device.
To learn about supported IdPs and how to set up SAML authentication for your Connected Experiences mobile app deployment, see Set up SAML authentication for Splunk Cloud Gateway.
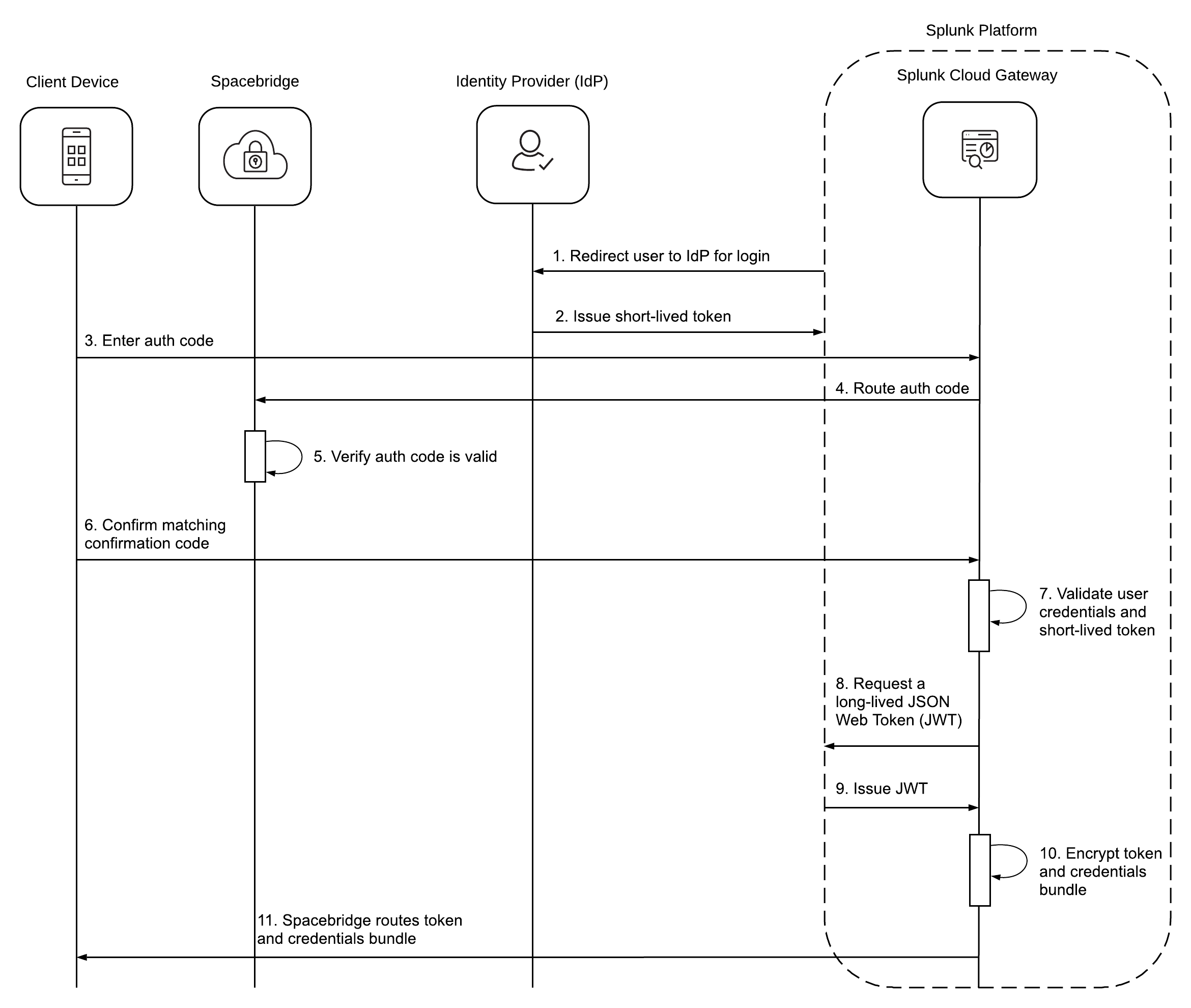
SAML authentication with provided authentication code
This is how a mobile client device authenticates to the Splunk platform with an IdP and the authentication code provided in a Connected Experiences mobile app.
- When a user launches the Splunk platform web view, they're redirected to their IdP to log in with their user credentials.
- The IdP issues a short-lived session token and the user has access to the Splunk platform.
- The user enters the authentication code provided in the Connected Experiences mobile app into Splunk Cloud Gateway.
- Splunk Cloud Gateway routes the authentication code to Spacebridge.
- Spacebridge receives and validates the authentication code.
- The user confirms that the conformation code on their device matches the one in Splunk Cloud Gateway.
- Splunk Cloud Gateway validates the user credentials and short-lived session token.
- Splunk Cloud Gateway requests a long-lived JWT from the Splunk platform.
- The Splunk platform issues a JWT to Splunk Cloud Gateway.
- Splunk Cloud Gateway encrypts the JWT, JWT expiry date, username, encryption keys, and Cloud Gateway ID.
- Spacebridge routes the JWT, JWT expiry date, username, encryption keys, and Cloud Gateway ID back to the client device.
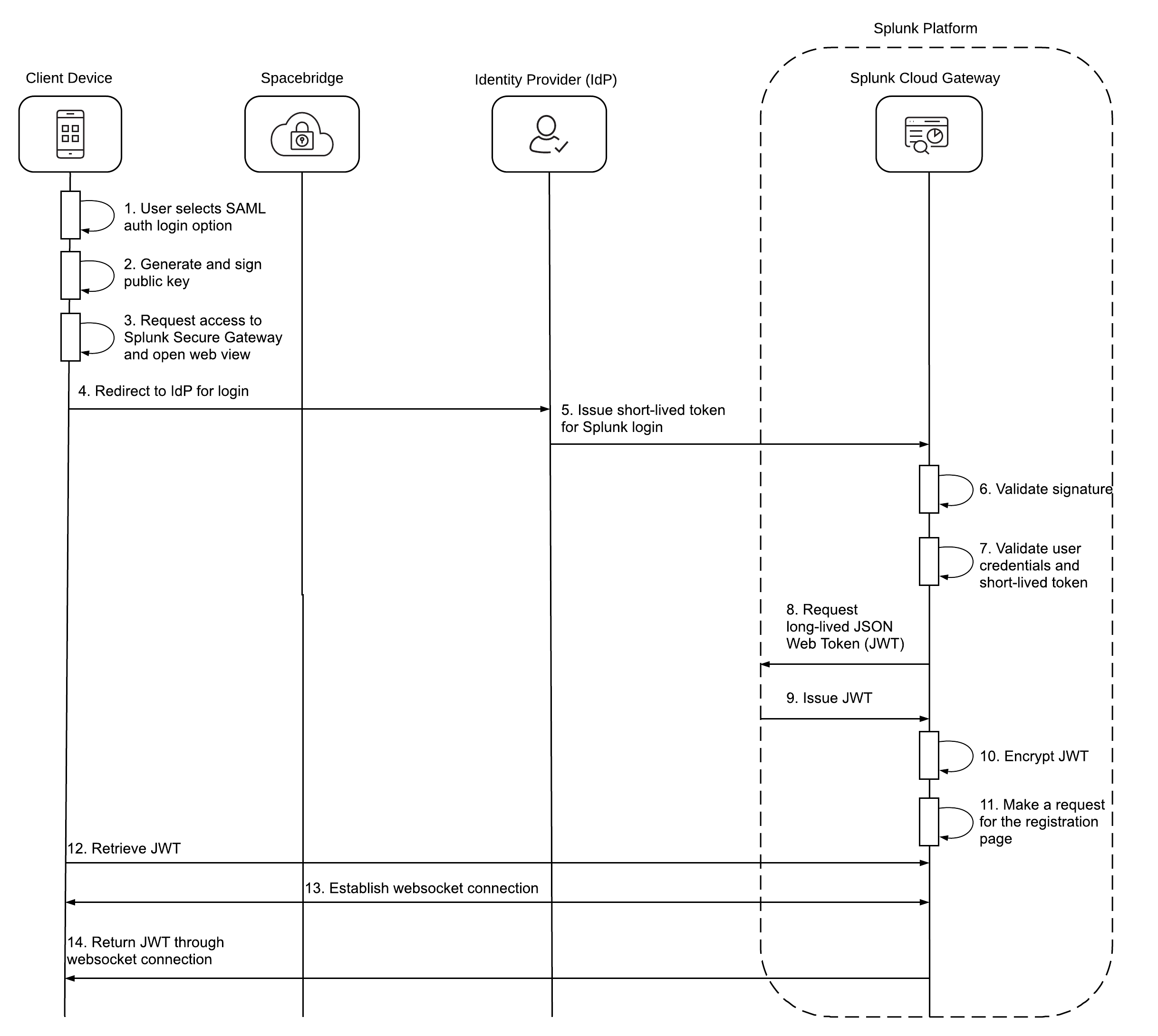
SAML authentication with MDM
This is how a mobile client device authenticates to the Splunk platform with an IdP and Mobile Device Management (MDM) provider. When an admin sets up MDM, they generate an instance ID file that supports SAML authentication. To learn more about MDM, see About Mobile Device Management (MDM) and In-app registration.
- When a user launches a Connected Experiences app that supports SAML authentication, they select the SAML authentication login option.
- The client device generates and signs a public key with the MDM private key from the instance ID file.
- The client device requests access to Splunk Cloud Gateway and opens a web view.
- The user is redirected to their IdP to log in with their user credentials.
- The IdP issues a short-lived session token to Splunk Cloud Gateway.
- Splunk Cloud Gateway validates the signature from the MDM private key.
- Splunk Cloud Gateway validates the user credentials and short-lived session token.
- Splunk Cloud Gateway requests a long-lived JWT from the Splunk platform.
- The Splunk platform issues a JWT to Splunk Cloud Gateway.
- Splunk Cloud Gateway encrypts the JWT with its own encryption key and the client device public key.
- Splunk Cloud Gateway makes a request for the registration page with the JWT as its query parameter.
- The client device recognizes the request for the registration page, retrieves the JWT, and closes the web view.
- Spacebridge establishes a websocket connection between the client device and Splunk Cloud Gateway.
- The client device returns the JWT through websocket connection to Splunk Cloud Gateway.
| Configure cloudgateway.conf | Set up SAML authentication for Splunk Cloud Gateway |
This documentation applies to the following versions of Splunk® Cloud Gateway (Legacy): 1.9.0, 1.9.1, 1.11.0, 1.12.0, 1.12.1, 1.12.2, 1.12.4, 1.13.0, 1.13.2, 1.13.3
 Download manual
Download manual
Feedback submitted, thanks!