 Download topic as PDF
Download topic as PDF
Insecure Authentication Attempts
This reports looks at attempts to access cardholder systems using insecure protocols and services. Use this report to identify the source of the insecure authentication attempts so they can be evaluated and eliminated if they pose a risk to the cardholder system.
If remote administration is not done with secure authentication and encrypted communications, sensitive administrative or operational level information (like administrator passwords) can be revealed to an eavesdropper. PCI DSS requires that you use only secure technologies to log into cardholder systems.
Relevant data sources
Relevant data sources for this report include any device that produces clear text or other insecure authentication activity (for example, Windows Security, telnet, rsh, and so on).
How to configure this report
1. Index authentication data from a device, application, or system in Splunk software.
2. Map the data to the following Common Information Model fields:
host, action, app, src, src_user, dest, user
3. Tag authentication messages that pass credentials in the clear or are considered insecure with either “cleartext” or “insecure”.
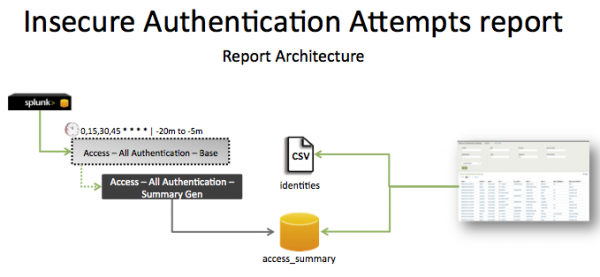
Report description
The data in the Insecure Authentication Attempts report is populated by a search that runs against the access_summary summary index. This index is created by the Access - All Authentication - Summary Gen saved search, which is a post-process task of the Access - All Authentication - Base saved search. Information in the access_summary summary index is combined with data in the identities table to create the report.
The search runs on an offset 15 minute cycle and looks at 15 minutes of data.
| Schedule | 0,15,30,45 * * * * | Runs on a 15 minute offset window. |
| Report window | -20m@m to -5m@m | Looks at 15 minutes of data. |
Note: The report window stops at 5 minutes ago, because some data sources may not have provided complete data in a more recent time frame.
Useful searches/Troubleshooting
| Troubleshooting Task | Search/Action | Expected Result |
|---|---|---|
| Verify that authentication data is returned. | tag=authentication or `authentication` |
Returns all insecure authentication activity data from your network device(s). |
| Verify that clear text authentication attempts are returned. | tag=cleartext tag=insecure | Returns all clear text authentication data. |
| Verify that insecure authentication attempts are returned. | tag=authentication tag=insecure | Returns all insecure authentication attempts. |
| Verify that all insecure and clear text authentication data is normalized to the Common Information Model properly. | `authentication` | tags outputfield=tag | table _time,host,action,app,src,src_user,dest,user,tag | Returns a table of the authentication fields. |
| Verify that the summary index was populated from the saved search correctly. | `get_summary(access_summary,Access - All Authentication - Summary Gen)` | search (tag=insecure OR tag=cleartext) | Returns data in the access_summary index. |
Additional information
Windows login events with LoginType=8 are often seen in this report. These login events are clear text log-in attempts. Other examples include telnet login events, rsh, rexec, and so on.
- The
Access – All Authentication – Summary Genis a post-process task. You can find the details of this search in the$SPLUNK_HOME/etc/apps/SA-AccessProtection/default/postprocess.conffile.
- The
Network – Communication – Summary Genis a post-process task. You can find the details of this search in the$SPLUNK_HOME/etc/apps/SA-NetworkProtection/default/postprocess.conffile.
|
PREVIOUS Default Account Access |
NEXT PCI System Inventory |
This documentation applies to the following versions of Splunk® App for PCI Compliance: 2.1.1
Feedback submitted, thanks!