Asset Management
Asset management allows events to be correlated with assets so that the location and priority of the asset can be determined.
What does asset management do?
Asset management provides additional information about the source and targets of events. This information can be used to correlate multiple events to a single host, identify the location of the host, determine whether the host is subject to regulatory compliance, and so on. Specifically, asset management provides the following:
- Prioritization
The same type of events on two different systems may not deserve the same level of attention; a medium severity event against a desktop machine is less urgent than the same issue against an externally facing web-server that processes credit card information. Asset management allows an urgency to be computed based on the priority of hosts and assign higher urgency to high priority assets.
- Categorization
Asset management allows information about the assets to be added to events. For example, asset management can look up the source of an event and find the location of the asset, indicate whether the source is subject to PCI compliance or identify the owner.
- Normalization
Asset management allows hosts to be normalized and determine whether two events relate to the same host. For example, two events may use different information to refer to the host; one event may use an IP address and another event may use a DNS name. Asset management can determine that both of the events are for the same host by recognizing that the IP address and DNS name are for the same host.
The asset table and PCI compliance scoping
The relationship between the pci_domain field and the category field is the single most important factor in determining asset management and PCI compliance in a cardholder data environment. The PCI compliance user needs a list of all assets that reside in a trusted zone, to monitor and report on these assets as a group and tell them apart from any assets that are not in a trusted zone.
The asset table fields category and pci_domain can be used to determine your PCI compliance scoping for asset management. The Asset Center dashboard (Resources > Asset Center) uses the category filter to display only PCI-relevant assets. If an asset is relevant to your PCI compliance, you can then use the pci_domain field to determine what domain that asset resides in, as part of your cardholder data environment.
You can create a list of assets that are applicable to PCI compliance with the category filter. You can distinguish these assets from non-PCI assets, and monitor and report on these assets as a discrete group.
For category the valid options are:
pci cardholder pci|cardholder
- The "
cardholder" category is used to define the "cardholder data environment" for PCI compliance (CDE). The cardholder data environment is comprised of people, processes, and technology that store, process, or transmit cardholder data or sensitive authentication data.
- The "
pci" category is used to define a PCI "system component". For PCI DSS, system components are defined as any network component, server, or application that is included in or connected to the cardholder data environment.
- The "
pci|cardholder" category (selecting bothpciandcardholder) filters assets within the asset center so that only PCI-relevant assets are displayed; assets in the CDE that are PCI system components.
The pci_domain filter can be used to search for assets by their PCI domain.
For pci_domain the valid options are:
trust trust|wireless trust|cardholder trust|dmz untrust
Note: untrust is not a required specification for the pci_domain field. If the field is left empty, "untrust" (untrustworthy) will be inferred.
How assets work
Asset management provides fields in events to designate the asset involved. This feature can identify events for assets, and identify assets for an event.
What is an asset?
An asset represents a host or a range of hosts (such as a subnet). An asset may have multiple identification fields such as a DNS name, an IP address, and a MAC address. Asset management will consider each of these fields in order to match the asset with the respective events.
Additionally, assets include information that describes the location and business unit of the asset. Assets can also be put into categories that define the purpose of the asset or the functional area it is contained within.
How asset fields are used
The Asset Search option allows you to search for assets from anywhere that an asset is found in a field context menu. These searches look for any match in an asset-related field.
Asset field matrix
| Asset table columns | ip | mac | nt_host | dns | owner | priority | lat | long | city | country | bunit | category | pci_domain | is_expected | should_timesync | should_update | requires_av |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Subject fields | |||||||||||||||||
| host/orig_host | host_ip | host_mac | host_nt_host | host_dns | host_owner | host_priority | host_lat | host_long | host_city | host_country | host_bunit | host_category | host_pci_domain | host_is_expected | host_should_timesync | host_should_update | host_requires_av |
| src | src_ip | src_mac | src_nt_host | src_dns | src_owner | src_priority | src_lat | src_long | src_city | src_country | src_bunit | src_category | src_pci_domain | src_is_expected | src_should_timesync | src_should_update | src_requires_av |
| dest | dest_ip | dest_mac | dest_nt_host | dest_dns | dest_owner | dest_priority | dest_lat | dest_long | dest_city | dest_country | dest_bunit | dest_category | dest_pci_domain | dest_is_expected | dest_should_timesync | dest_should_update | dest_requires_av |
| dvc | dvc_ip | dvc_mac | dvc_nt_host | dvc_dns | dvc_owner | dvc_priority | dvc_lat | dvc_long | dvc_city | dvc_country | dvc_bunit | dvc_category | dvc_pci_domain | dvc_is_expected | dvc_should_timesync | dvc_should_update | dvc_requires_av |
In this table:
- Fields along the vertical axis are subject fields, provided by event field extractions.
- Columns along the horizontal axis are the columns available in the asset table.
- The asset lookup takes one of
ip,mac,nt_host,dnsto perform its matching. - The asset lookup provides all fields for a given subject when a match is made.
- Since events can have multiple subjects, fields are output using the
<subject>_<asset_column>notation. - The
categoryandpci_domaincolumns accept multiple values, represented as a pipe delimited string (for example,category1|category2|category3).
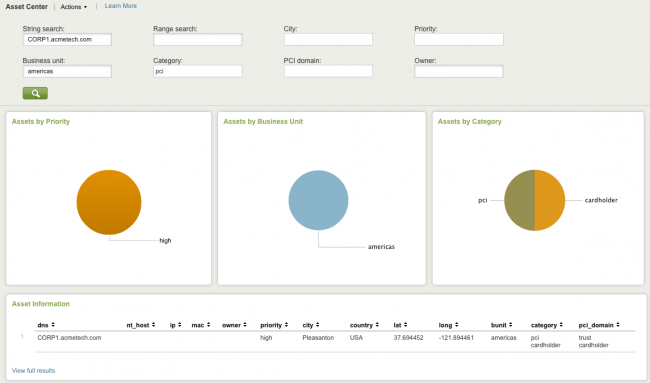
For example, suppose there is an entry in the asset list with CORP1.acmetech.com in the DNS column. The asset list columns would look like this:
A sample asset might look like:
For any event where the nt_host field has the value CORP1.acmetech.com, the Splunk App for PCI Compliance looks for CORP1.acmetech.com in the asset list at search time. When it finds a match, the app generates additional fields from the information in the asset list, including the following:
host_owner dmaradona@acme.com host_priority high host_lat 41.040855 host_long 28.986183 host_bunit americas host_category pci|cardholder
These fields are used in the following ways:
- If a notable event is created based on this host, for example, if the host has a high number of infections, then the following fields are used:
- The
priorityfield (high) is combined with the severity of the search to create the urgency for the notable event.
- The
bunitandcategoryfields are used for the filters on the domain and supporting dashboards. For example, our event would be included in a restricted view with this filter:
Note: Categories also rely on the category list. See Category list for more information.
- For example, if there is a problem with the host and you want to notify the asset owner, find the owner by looking at the asset list in Splunk App for PCI Compliance (Resources > Asset Center) or using the Interactive Field Extractor.
How assets are identified
The Splunk App for PCI Compliance automatically performs an asset lookup whenever there is a value in the host, orig_host, src, dest, or dvc field. For each one of these fields, the app creates new fields that contain the asset information. Because an event can have values for more than one of these fields, the name of the generated field is prepended with the name of the field that contains the asset; for example, the generated priority field for a src is called src_priority. This disambiguation does not affect menus, but can be useful to know in searches. When a search is run and an event includes data in one or more of the asset fields (host, orig_host, src, dest, dvc), the Splunk App for PCI Compliance looks up the asset in the asset list. The asset list includes four columns that can contain identifying information for the asset. The Splunk App for PCI Compliance attempts to identify the asset based on following order of precedence:
- ip: An IP address (e.g., 1.2.3.4) or a range of IP addresses (e.g., 192.168.15.9-192.169.15.27 or 2.0.0.0/8).
- mac: A Media Access Control (MAC) Address (e.g., 00:25:bc:42:f4:60) or range of MAC Addresses (e.g., 00:25:bc:42:f4:60-00:25:bc:42:f4:6F)
- dns: DNS name
- nt_host: Windows Machine Name (also known as the NetBIOS machine name)
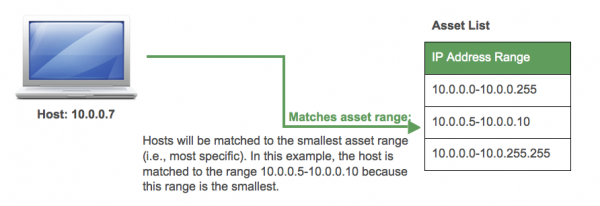
The asset lookup attempt stops as soon as it gets a match. For example, if the asset matches an IP, then asset lookup won't try matching on MAC addresses, DNS names, or machine names. Asset lookup only matches a single asset and does not combine data from all potential matching assets. For IP addresses and MAC addresses, asset lookups attempt to find the most specific address if multiple ranges match. For example, if two IP ranges match a given host, asset lookup uses the smaller (most specific) of the ranges (see below for an example). When a single IP address or MAC address is available, it is used, since it is an address range of one.
How the urgency of an event is assigned
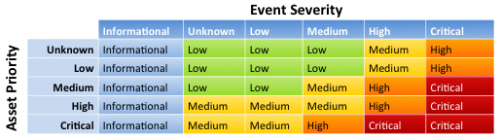
The severity of the event and the priority of the host are combined to generate the urgency of an event. The urgency allows events to be weighed according to the asset, thus causing events against higher priority assets to be treated with higher urgency. The urgency is calculated per the table below:
- If Event Severity is Informational, the Event Urgency is Informational, regardless of Asset Priority
- If Asset Priority is Unknown or Low and Event Severity is Unknown, Low, or Medium, the Event Urgency is Low
- If Asset Priority is Unknown or Low and Event Severity is High, the Event Urgency is Medium
- If Asset Priority is Unknown or Low and Event Severity is Critical, the Event Urgency is High
- If Asset Priority is Unknown or Low and Event Severity is Critical, the Event Urgency is High
- If Asset Priority is Medium and Event Severity is Unknown or Low, the Event Urgency is Low
- If Asset Priority is Medium and Event Severity is Medium, the Event Urgency is Medium
- If Asset Priority is Medium and Event Severity is High, the Event Urgency is High
- If Asset Priority is Medium and Event Severity is Critical, the Event Urgency is Critical
- If Asset Priority is High and Event Severity is Unknown, Low, or Medium, the Event Urgency is Medium
- If Asset Priority is Medium and Event Severity is High, the Event Urgency is High
- If Asset Priority is Medium and Event Severity is Critical, the Event Urgency is Critical
- If Asset Priority is Critical and Event Severity is Unknown or Low, the Event Urgency is Medium
- If Asset Priority is Critical and Event Severity is Medium, the Event Urgency is High
- If Asset Priority is Critical and Event Severity is High or Critical, the Event Urgency is Critical
Asset management allows events to be correlated with assets, so that the location and priority of the asset can be determined.
Correlation searches and severity
Correlation searches will not use the severity defined in the search, if the events being searched contain a severity value (that is, a field named severity). Rename the severity field in the search to something like vendor_severity, and the severity specified in the correlation search definition will be used.
Add the following to the correlation search:
{code}
eval vendor_severity | fields –severity
{code}
To do this go to Configure > Correlation Searches and click on the search to open the Correlation Search editor.
Make this change to the Search field of the selected correlation search:
{code}
`authentication`| eval vendor_severity | fields –severity
{code}
Click Save.
The "authentication" search now ignores the severity field and uses the vendor_severity field.
Customizing assets
To establish a new asset list or make immediate modifications to an existing list, go to Configure > Assets > Edit and paste in the new asset information.
Note: The editor does not validate input.
Alternatively, the CSV file may be installed to the following path: $SPLUNK_HOME/etc/apps/SA-IdentityManagement/lookups/assets.csv.
Note: The CSV file must use UNIX line endings. The popular dos2unix utility may be used to correct line endings in a file produced on Windows or OS/X.
It is recommended that you update the list periodically in order to ensure that the Splunk App for PCI Compliance has reasonably up-to-date information. Generally, it is recommended that the list be updated at least every quarter.
It is possible to configure a scripted input to automatically populate the list if it is contained within a database. Automatic asset updates can be done using a combination of scripted inputs and custom search commands (written in Python). The implementation details depend on the technology that contains the asset information and is beyond the scope of this document.
Since Splunk automatically loads the asset list at search time, it does not need to be restarted.
This table describes the necessary fields for an asset list.
| Field | Description | Example |
|---|---|---|
| ip | IP address (can be a range) | Example: 2.0.0.0/8, 1.2.3.4, 192.168.15.9-192.169.15.27 |
| mac | The MAC address of the host (can be a range) | Example: 00:25:bc:42:f4:60, 00:25:bc:42:f4:60-00:25:bc:42:f4:6F |
| nt_host | The Windows machine name of the host | Example: ACMEapp |
| dns | The DNS name of the host | Example: corp1.acmetech.com |
| owner | The name of the user who owns or uses the host | Example: john.doe |
| priority | The priority of the host; must be either unknown, informational, low, medium, high, or critical | Example: Must be one of: unknown, informational, low, medium, high, or critical |
| lat | The latitude of the asset | Example: 41.040855 |
| long | The longitude of the asset | Example: 28.986183 |
| city | The city in which the asset is located | Example: Chicago |
| country | The country in which the asset is located | Example: USA |
| bunit | The business unit of the asset | Example: EMEA |
| category | One or more categories for the asset. To specify multiple categories for an asset, use a vertical bar. To use this field, set up the category list. | Example: pci, cardholder, pci [pipe] cardholder |
| pci_domain | The domain of the host as it pertains to PCI; the domain is used to in order to identify instances where cardholder data may pass to Internet-facing devices (reference PCI requirement 1.3.3) | wireless, trust|cardholder, trust|dmz, untrust (untrust is not a required specification; it will be inferred if pci_domain is left empty) |
| is_expected | Indicates whether events from this asset should always be expected; if set to true, then an alert will be triggered when this asset quits reporting events | Example: true (leave blank to indicate "false") |
| should_timesync | Indicates whether this asset must be monitored for time-syncing events; if true, then an alert will be triggered if the host has not performed a time-sync event (such as a NTP request) | Example: true (leave blank to indicate "false") |
| should_update | Indicates whether this asset must be monitored for system update events; if true, then an alert will be triggered if the host does not seem to be performing system updates | Example: true (leave blank to indicate "false") |
| requires_av | Indicates whether the asset requires anti-virus software to be installed. | Example: true or false |
Category list
The category list specifies a list of categories that can be used for the category field in the asset list. The category list can be any set of categories you choose. Common examples are compliance and security standards (such as PCI) governing the asset, or functional categories (such as pci, cardholder, and pci|cardholder.).
| Asset and Identity Correlation | Identity Correlation |
This documentation applies to the following versions of Splunk® App for PCI Compliance: 2.1.1
 Download manual
Download manual
Feedback submitted, thanks!