Set host values based on event data
You can configure the Splunk platform to assign host names to your events based on the data in those events. You can use event data to override the default assignment that the Splunk platform makes by supplying a regular expression for the event data and configuring two configuration files to determine when the platform is to override the host name for an event.
On Splunk Cloud Platform, you must configure a heavy forwarder to perform host name assignment, and then forward that data to your Splunk Cloud Platform instance. You have to take this extra step because you can't edit configuration files on a Splunk Cloud Platform instance directly.
If you have access to the Edge Processor solution, you can also perform host name assignment using an Edge Processor. See About the Edge Processor solution in the Use Edge Processors manual.
On Splunk Enterprise, you can edit configuration files, either on an indexer or a heavy forwarder. In any case, you can't use a universal forwarder because universal forwarders can't transform data except in certain limited cases.
For a primer on regular expression syntax and usage, see the website http://www.regular-expressions.info/reference.html. You can test regular expressions by using them in searches with the rex search command.
Using configuration files to override the host name default field in events
The Splunk platform tags event data with default fields while the data is being ingested. Creating host name overrides for events that the Splunk platform indexes requires you to edit two configuration files on the Splunk platform instance that collects the data, based on some of those default fields.
About updating the transforms.conf file
The first file, transforms.conf, configures the host name override by using a regular expression to determine when the instance is to overwrite, or transform, the host name default field. You supply the regular expression by determining what exactly in your event data is to trigger the transformation, and then providing that regular expression to the transforms.conf file. You provide this regular expression as a stanza within the file, and the Splunk platform triggers the override when incoming event data matches the regular expression that you specify.
About updating the props.conf file
The second file, props.conf, determines the default fields to which the host name override can apply. These fields appear as a stanza within the file which specifies the default fields where the Splunk platform can potentially modify the host name field for incoming events.
You can apply host name overrides to the following default fields:
- The source, using the
source::<source>keyword - The source type, using the
sourcetype=<sourcetype>keyword - The host name, using the
host::<host>keyword
Host name overrides occur when you specify one of these default fields in the props.conf file. The following events must occur before the Splunk platform can override the host name:
- The host, source, or sourcetype in the incoming event data must match what you specify in the props.conf file to activate the host name override transform configuration in the transforms.conf file.
- The event data must match the regular expression you set for the host name override transform to trigger.
Create a host name override
- Review your event data to determine a string that represents when you want the Splunk platform to perform the host name override. This string becomes the regular expression you supply later in the procedure. See the example later in this topic.
- Review the Configure a transforms.conf stanza with a host name override transform and Configure a props.conf stanza to reference a host name override transform sections in this section to understand how stanza syntax for host name overrides works.
- On a heavy forwarder where you want to do the host name overrides, open a text editor.
- With that editor, open the $SPLUNK_HOME/etc/system/local/transforms.conf file for editing.
- Add a stanza to this file that represents when the Splunk platform is to do the host name override.
- Save the transforms.conf file and close it.
- Open the $SPLUNK_HOME/etc/system/local/props.conf file for editing.
- Add a stanza to this file that represents the default fields for which the host name override is to apply.
- Save the props.conf file and close it.
- Restart the heavy forwarder.
On Splunk Enterprise, you can perform this procedure on either the instance that ingests the data or on a heavy forwarder that sends data to the instance.
For more information about configuration files in general, see About configuration files in the Splunk Enterprise Admin Manual.
Configure a transforms.conf stanza with a host name override transform
The transforms.conf file controls where and how the Splunk platform transforms the incoming event data.
The host name override transformation stanza in transforms.conf uses the following syntax:
[<unique_stanza_name>] REGEX = <your_regex> FORMAT = host::$1 DEST_KEY = MetaData:Host
There are a few things to note in this stanza:
- Use the
<unique_stanza_name>part of the syntax to refer to the transform from the props.conf configuration file. A best practice is for it to reflect that it involves a host value. <your_regex>is the regular expression that identifies where in the event you want to extract the host value and assign that value as the default field for that event.FORMAT = host::$1writes theREGEXvalue into thehost::field.
Configure a props.conf stanza to reference the host name override transform
The props.conf file references the stanza in the transforms.conf file that performs the transformation:
[<spec>] TRANSFORMS-<class> = <unique_stanza_name>
There are a few things to note in this stanza:
<spec>can be any of these values:<sourcetype>, the source type of an event.host::<host>, where<host>is the host value for an event.source::<source>, where<source>is the source value for an event.
<class>is any unique identifier that you want to give to your transform.<unique_stanza_name>is the name of the stanza you created in transforms.conf.
Example of host name default field overriding
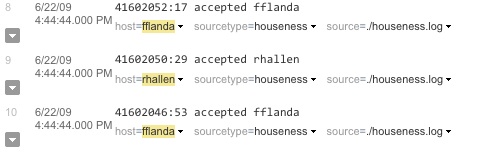
Given the following set of events from the houseness.log file. You want the Splunk platform to set the host default field for each event to the host name found within the event. The host is in the third position of each line in the log file. In this example, it's fflanda.
41602046:53 accepted fflanda 41602050:29 accepted rhallen 41602052:17 accepted fflanda
First, create a new stanza in the transforms.conf file and provide a regular expression that extracts the host value:
[houseness] DEST_KEY = MetaData:Host REGEX = \s(\w*)$ FORMAT = host::$1
Next, reference the transforms.conf stanza in a stanza in the props.conf configuration file. See the following example:
[source::.../houseness.log] TRANSFORMS-rhallen=houseness SHOULD_LINEMERGE = false
This example stanza has the additional setting SHOULD_LINEMERGE = false to break events at each new line.
The events then appear in search results like this:
| Set a default host for a file or directory input | Change host values after indexing |
This documentation applies to the following versions of Splunk® Enterprise: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.7, 7.0.8, 7.0.9, 7.0.10, 7.0.11, 7.0.13, 7.1.0, 7.1.1, 7.1.2, 7.1.3, 7.1.4, 7.1.5, 7.1.6, 7.1.7, 7.1.8, 7.1.9, 7.1.10, 7.2.0, 7.2.1, 7.2.2, 7.2.3, 7.2.4, 7.2.5, 7.2.6, 7.2.7, 7.2.8, 7.2.9, 7.2.10, 7.3.0, 7.3.1, 7.3.2, 7.3.3, 7.3.4, 7.3.5, 7.3.6, 7.3.7, 7.3.8, 7.3.9, 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.4, 8.0.5, 8.0.6, 8.0.7, 8.0.8, 8.0.9, 8.0.10, 8.1.0, 8.1.1, 8.1.2, 8.1.3, 8.1.4, 8.1.5, 8.1.6, 8.1.7, 8.1.8, 8.1.9, 8.1.10, 8.1.11, 8.1.12, 8.1.13, 8.1.14, 8.2.0, 8.2.1, 8.2.2, 8.2.3, 8.2.4, 8.2.5, 8.2.6, 8.2.7, 8.2.8, 8.2.9, 8.2.10, 8.2.11, 8.2.12, 9.0.0, 9.0.1, 9.0.2, 9.0.3, 9.0.4, 9.0.5, 9.0.6, 9.0.7, 9.0.8, 9.0.9, 9.0.10, 9.1.0, 9.1.1, 9.1.2, 9.1.3, 9.1.4, 9.1.5, 9.1.6, 9.1.7, 9.1.8, 9.1.9, 9.2.0, 9.2.1, 9.2.2, 9.2.3, 9.2.4, 9.2.5, 9.2.6, 9.3.0, 9.3.1, 9.3.2, 9.3.3, 9.3.4, 9.4.0, 9.4.1, 9.4.2
 Download manual
Download manual
Feedback submitted, thanks!