Tag field-value pairs in Search
You might have groups of events with related field-value pairs. To help you search for these events, assign the same tag to these related field-value pairs.
Tag field-value pairs
You can tag any field-value pair directly from the results of a search.
Prerequisites
- See About tags and aliases for information on tags.
Steps
- Locate an event with a field-value pair that you want to tag.
- Expand a row to see the full list of fields extracted from the event.
- Click the Actions arrow for the field-value pair that you want to create a tag for and select Edit Actions.
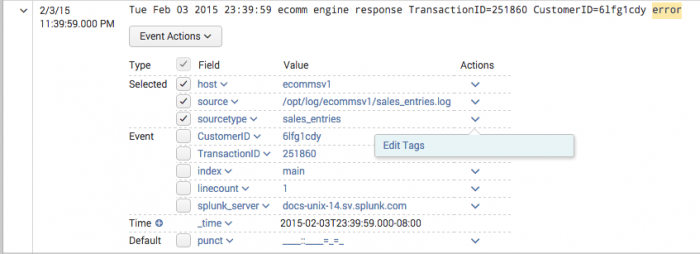
- In the Create Actions dialog box , define one or more tags for the field-value pair.
- Values for the Tag(s) field must be separated by commas or spaces.
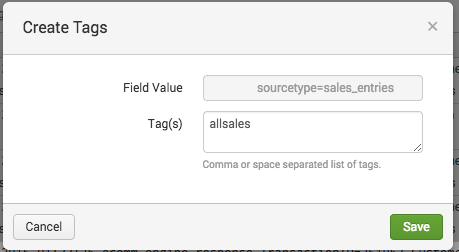
- Click Save.
Remove URL-encoded values from tag definitions
When you tag a field-value pair, the value part of the pair cannot be URL-encoded. If your tag has any %## format URL-encoding, decode it and then save the tag with the decoded URL.
For example, you want to give the following field-value pair the tag Useful.
url=http%3A%2F%2Fdocs.splunk.com%2FDocumentation.
Define the tag in Settings.
- Select Settings > Tags > List by tag name.
- Click on the Useful tag name to open the detail page for that tag.
- Under Field-value pair replace
url=http%3A%2F%2Fdocs.splunk.com%2FDocumentationwith the decoded version:url=http://docs.splunk.com/Documentation. - Click Save.
See Define and manage tags in Settings.
Search for tagged field values
You have two ways to search for tags. To search for a tag associated with a value in any field, use the following syntax:
tag=<tagname>
To search for a tag associated with a value in a specific field, use the following syntax:
tag::<field>=<tagname>
Use wildcards to search for tags
You can use the asterisk (*) wildcard when you search keywords and field values, including for eventtypes and tags.
For example, if you have multiple eventtype tags for various types of IP addresses, such as IP-src and IP-dest, you can search for all of them with:
tag::eventtype=IP-*
To find all hosts whose tags contain "local", search for the following tag:
tag::host=*local*
To search for the events with eventtypes that have no tags, you can search for the following Boolean expression:
NOT tag::eventtype=*
Disable and delete tags
You can remove a tag association for a specific field value through the Search app. You can also disable or delete tags, even if they are associated with multiple field values in Settings.
See Define and manage tags in Settings.
Remove a tag association for a specific field value in search results
You can remove a tag associated with a field value in your search results.
- Click the arrow next to the event.
- Under Actions, click open the arrow next to the field value.
- Select Edit Tags to open the Create Tags window.
- In the Create Tags window, delete the tags that you want to disable from the Tags field.
- Click Save.
This action removes this tag and field value association from the system. If this is the only field value the tag is associated with, the tag is removed from the system.
Tagging event types in settings
You can add tags when you create or edit an event type. See Tag event types.
Rename source types
When you configure a source type in props.conf, rename the source type. Multiple source types can share the same name,so you can group a set of source types for a search. For example, you can normalize source type names that include "-too_small" to remove the classifier. See Rename source types at search time.
| About tags and aliases | Define and manage tags in Settings |
This documentation applies to the following versions of Splunk® Enterprise: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.7, 7.0.8, 7.0.9, 7.0.10, 7.0.11, 7.0.13, 7.1.0, 7.1.1, 7.1.2, 7.1.3, 7.1.4, 7.1.5, 7.1.6, 7.1.7, 7.1.8, 7.1.9, 7.1.10, 7.2.0, 7.2.1, 7.2.2, 7.2.3, 7.2.4, 7.2.5, 7.2.6, 7.2.7, 7.2.8, 7.2.9, 7.2.10, 7.3.0, 7.3.1, 7.3.2, 7.3.3, 7.3.4, 7.3.5, 7.3.6, 7.3.7, 7.3.8, 7.3.9, 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.4, 8.0.5, 8.0.6, 8.0.7, 8.0.8, 8.0.9, 8.0.10, 8.1.0, 8.1.1, 8.1.2, 8.1.3, 8.1.4, 8.1.5, 8.1.6, 8.1.7, 8.1.8, 8.1.9, 8.1.10, 8.1.11, 8.1.12, 8.1.13, 8.1.14, 8.2.0, 8.2.1, 8.2.2, 8.2.3, 8.2.4, 8.2.5, 8.2.6, 8.2.7, 8.2.8, 8.2.9, 8.2.10, 8.2.11, 8.2.12, 9.0.0, 9.0.1, 9.0.2, 9.0.3, 9.0.4, 9.0.5, 9.0.6, 9.0.7, 9.0.8, 9.0.9, 9.0.10, 9.1.0, 9.1.1, 9.1.2, 9.1.3, 9.1.4, 9.1.5, 9.1.6, 9.1.7, 9.1.8, 9.1.9, 9.2.0, 9.2.1, 9.2.2, 9.2.3, 9.2.4, 9.2.5, 9.2.6, 9.3.0, 9.3.1, 9.3.2, 9.3.3, 9.3.4, 9.4.0, 9.4.1, 9.4.2
 Download manual
Download manual
Feedback submitted, thanks!