About the Content Pack for ITSI Monitoring and Alerting
The Content Pack for ITSI Monitoring and Alerting provides a prescriptive blueprint for enterprise-wide alerting across all your services. It helps ITSI administrators and service owners quickly translate service and KPI health into notable events and take action when necessary. The content pack provides a set of preconfigured correlation searches and notable event aggregation policies which, when enabled, produce meaningful and actionable alerts. The content pack also provides a faster method for onboarding external alerts into ITSI with universal alerting.
This content pack includes three feature areas:
- Service Monitoring, for ITSI services and KPIs
- Episode Monitoring, for open episodes
- Universal Alerting, for external alerts
Use this content pack as a starting point in a clean ITSI environment. If you do restore the content to an active environment, you must back up your environment first. See Create a full backup of ITSI in the Administration Manual.
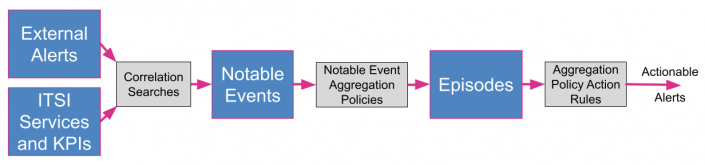
Refresher: How alerts are generated in ITSI
To better understand what's included in this content pack, consider the standard workflow for configuring ITSI to take action on service and KPI health with the following diagram. The grey boxes represent configurations that the ITSI administrator or service owner must perform before ITSI can produce actionable alerts.
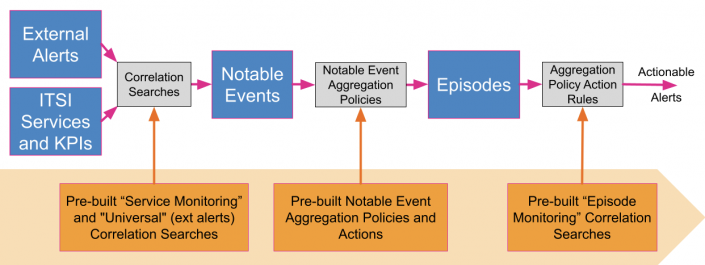
Content pack contents
This content pack contains objects that facilitate the entire alert configuration process as depicted in the following diagram:
The diagram shows content pack components in orange, below the outline of the alert configuration process. Each of the three main components of the content pack supports an aspect of configuration identified by a gray box in the workflow between finding something worth monitoring and generating alerts on that when system conditions warrant such notification. Logically related notable events are grouped together by pre-built aggregation policies into episodes. Rules for when to take action are built on the notable event aggregation policies, and special "episode monitoring" correlation searches are responsible for detecting alertable conditions and invoking actions on the aggregation policies.
This content pack contains the following object types:
| Object | Description |
|---|---|
| Service monitoring correlation searches | The service monitoring correlation searches routinely check service and KPI results written to the itsi_summary index and produce notable events based on a variety of noteworthy circumstances related to service and KPI health. For more information about these correlation searches, see About the correlation searches in the Content Pack for ITSI Monitoring and Alerting.
|
| Notable event aggregation policies | The aggregation policies provide configuration for grouping related notable events together in useful ways. The policies also contain action rules that you can tune to meet your organization's alerting strategy. For example, some action rules produce emails, create service tickets, or integrate with Splunk On-Call (formerly VictorOps) or other incident response platforms. For more information about these aggregation policies, see About the aggregation policies in the Content Pack for ITSI Monitoring and Alerting. |
| Episode monitoring correlation searches | The episode monitoring correlation searches routinely inspect open episodes and produce alerts based on a variety of noteworthy circumstances related to those episodes. For more information about these correlation searches, see About the correlation searches in the Content Pack for ITSI Monitoring and Alerting. |
| Universal correlation search | This correlation search onboards all external alerts that comply with the Universal Alerts Field Normalization Standard. For more information, see About Universal Alerting or About the correlation searches in the Content Pack for ITSI Monitoring and Alerting. |
The content pack also ships with other supporting objects including episode views, automatic lookups, dashboards, and sample services. For a full list of the contents contained within this content pack, see Release notes for the Content Pack for ITSI Monitoring and Alerting.
Installation
If you're using ITSI v4.9 or later, you can install the Content Pack for ITSI Monitoring and Alerting after installing the Splunk App for Content Packs. Install the content pack on the same search head where you installed ITSI or IT Essentials Work. For installation instructions, see Install and configure the Content Pack for ITSI Monitoring and Alerting.
If you're using ITSI v4.8 or earlier, you need to install the content pack using the backup ZIP file. See Install and configure the Content Pack for ITSI Monitoring and Alerting for detailed instructions.
Deployment requirements
Use the following table to determine ITSI version compatibility with the Content Pack for ITSI Monitoring and Alerting.
| Content pack version | ITSI version | Add-on version |
|---|---|---|
| 2.3.0 | 4.17.x | n/a |
| 2.2.0 | 4.14.x or higher | n/a |
| 2.1.0 | 4.13.x or higher | n/a |
| 2.0.3 | 4.9.4, 4.11.0 | n/a |
| 2.0.2 | 4.9.4, 4.11.0 | 2.0.2 |
| 2.0.0 | 4.4.0 or higher | 2.0.2 |
| 1.0.0 | 4.2.1 or higher | 1.2.1 |
Additional resources
- For ITSI deployment planning guidelines, see Plan your ITSI deployment in the Install and Upgrade manual.
- For ITSI version compatibility with Splunk Enterprise versions, see Splunk products version compatibility matrix.
| Release Notes for the Content Pack for ITSI Monitoring and Alerting |
This documentation applies to the following versions of Content Pack for ITSI Monitoring and Alerting: 2.3.0
 Download manual
Download manual
Feedback submitted, thanks!