Define event types in Splunk Web
An event type represents a search that returns a specific type of event or a useful collection of events. Every event that can be returned by that search gets an association with that event type. For example, say you have this search:
sourcetype=access_combined status=200 action=purchase
If you save that search as an event type named successful_purchase, any event that could be returned by that search gets eventtype=successful_purchase added to it at search time. This happens even if you are searching for something completely different.
And later, if you want to build a search that works with events that match that event type, include eventtype=successful_purchase in the search string.
A single event can match multiple event types. When an event matches two or more event types, eventtype acts as a multivalue field.
Save a search you ran as an event type
When you run a search, you can save that search as an event type. Event types usually represent searches that return a specific type of event, or that return a useful variety of events.
When you create an event type, the event type definition is added to eventtypes.conf in $SPLUNK_HOME/etc/users/<your-username>/<app>/local/, where <app> is your current app context. If you change the permissions on the event type to make it available to all users (either in the app, or globally to all apps), the Splunk platform moves the event type to $SPLUNK_HOME/etc/apps/<App>/local/.
Prerequisities
- See About event types for more information on event types.
- See About tags and aliases, for information about event type tagging.
- See About event type priorities, for more information about the Color and Priority fields.
Saving a search as an event type
- In the Search view, run a search.
- Click Save As and select Event Type.
- Give the event type a unique Name.
- (Optional) Add one or more comma-separated Tag(s).
You can apply the same tag to event types that produce similar results. A search that is just on that tag returns the set of events that collectively belong to those event types. - (Optional) Select a Color.
This causes a band of color to appear at the start of the listing for any event that fits this event type. For example, this event matches an event type that has a Color of Purple.
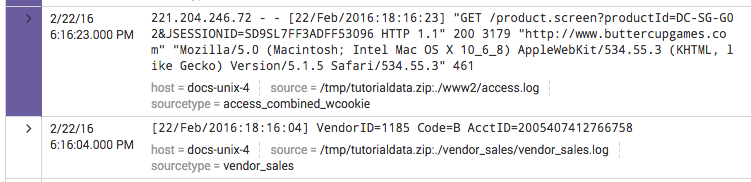
You can change the color of an event type (or remove its color entirely) by editing it in Settings. - (Optional) Give the event type a Priority.
Priority affects the display of events that match two or more event types. 1 is the best Priority and 10 is the worst. See About event type priorities. - Click Save to save the new event type.
You can access the list of event types that you and other users have created at Settings > Event types.
Any event type that you create with this method also appears on the Event Types listing page in Settings. You can update the event type in the Event Types listing page.
Event Types page in Settings
The Event Types page in Settings displays a list of the event types that you have permission to view or edit. You can use the Event Types page to create event types and maintain existing event types.
Add an event type in Settings
You can create a new event type through the Event Types page.
Prerequisites
- See About event types for more information on event types.
- See Save a search you ran as an event type. Most of the fields are discussed there.
- See About tags and aliases, for information about event type tagging.
- See About event type priorities, for more information about the Color and Priority fields.
Adding a new event type in Settings
- Select Settings > Event Types.
- Click New.
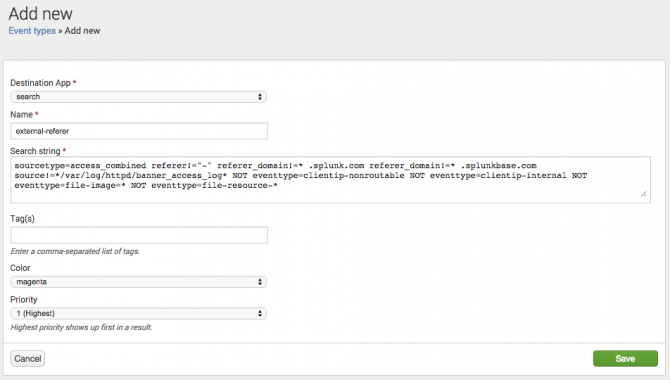
- (Optional) Change the Destination App value to the correct app for the event type, if it is not your current app context.
- Provide a unique Name for the event type.
- Enter the Search String for the event type.
This search consistently returns a specific kind of event. - (Optional) Add one or more comma-separated Tag(s).
You can apply the same tag to event types that produce similar results. A search that is just on that tag returns the set of events that collectively belong to those event types. - (Optional) Select a Color.
This causes a band of color to appear at the start of the listing for any event that fits this event type. - (Optional) Give the event type a Priority.
Priority affects the display of events that match two or more event types. 1 is the best Priority and 10 is the worst.
Priority determines the order of the event type listing in the expanded event. It also determines which color displays for the event type if two or more of the event types matching the event have a defined Color value.
For more see About event type priorities. - Click Save to save the event type.
Note: All event types are initially created for a specific Splunk app. To make a particular event type available to all users on a global basis, you have to give all roles read or write access to the Splunk app and make it available to all Splunk apps. For more information about setting permissions for event types (and other knowledge object types), see Manage knowledge object permissions, in this manual.
Update an event type in Settings
Prerequisites
- See About event types for more information on event types.
- See Save a search you ran as an event type. Most of the fields are discussed there.
- See About tags and aliases, for information about event type tagging.
- See About event type priorities, for more information about the Color and Priority fields.
Steps
You can update the definition of any event type that you have created or which you have permissions to edit.
- Navigate to Settings > Event Types.
- Locate the event type that you would like to update in the Event Types listing page and click its name.
- Update the Search String, Tag(s), Color, and Priority of the event type as necessary.
- Click Save to save your changes.
| About event types | About event type priorities |
This documentation applies to the following versions of Splunk® Enterprise: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.7, 7.0.8, 7.0.9, 7.0.10, 7.0.11, 7.0.13, 7.1.0, 7.1.1, 7.1.2, 7.1.3, 7.1.4, 7.1.5, 7.1.6, 7.1.7, 7.1.8, 7.1.9, 7.1.10, 7.2.0, 7.2.1, 7.2.2, 7.2.3, 7.2.4, 7.2.5, 7.2.6, 7.2.7, 7.2.8, 7.2.9, 7.2.10, 7.3.0, 7.3.1, 7.3.2, 7.3.3, 7.3.4, 7.3.5, 7.3.6, 7.3.7, 7.3.8, 7.3.9, 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.4, 8.0.5, 8.0.6, 8.0.7, 8.0.8, 8.0.9, 8.0.10, 8.1.0, 8.1.1, 8.1.2, 8.1.3, 8.1.4, 8.1.5, 8.1.6, 8.1.7, 8.1.8, 8.1.9, 8.1.10, 8.1.11, 8.1.12, 8.1.13, 8.1.14, 8.2.0, 8.2.1, 8.2.2, 8.2.3, 8.2.4, 8.2.5, 8.2.6, 8.2.7, 8.2.8, 8.2.9, 8.2.10, 8.2.11, 8.2.12, 9.0.0, 9.0.1, 9.0.2, 9.0.3, 9.0.4, 9.0.5, 9.0.6, 9.0.7, 9.0.8, 9.0.9, 9.0.10, 9.1.0, 9.1.1, 9.1.2, 9.1.3, 9.1.4, 9.1.5, 9.1.6, 9.1.7, 9.1.8, 9.1.9, 9.2.0, 9.2.1, 9.2.2, 9.2.3, 9.2.4, 9.2.5, 9.2.6, 9.3.0, 9.3.1, 9.3.2, 9.3.3, 9.3.4, 9.4.0, 9.4.1, 9.4.2
 Download manual
Download manual
Feedback submitted, thanks!