Troubleshoot the Splunk App for Windows Infrastructure
This topic discusses how you can troubleshoot your Splunk App for Windows Infrastructure deployment if you aren't seeing the data that you expect.
Is the Splunk App for Windows Infrastructure deployment correctly configured?
The first thing to check when Splunk App for Windows Infrastructure data is incomplete or incorrect is to confirm that the central Splunk instance is properly configured and is receiving data.
- Confirm that every indexer in the deployment has been configured to receive data. See Install and configure a Splunk Enterprise indexer in this manual or Enable a receiver in the core Splunk documentation for instructions.
- If present, confirm that every search head in the central Splunk instance has been configured properly. Search heads must search all available indexers to get all indexed AD data.
See Distributed search deployment overview and Configure distributed search in the core Splunk Enterprise documentation for specific instructions on configuring search heads and search peers (indexers).
See How to deploy the Splunk App for Windows Infrastructure for specific instructions on what to install on search heads. - Confirm that you have installed and configured all the components properly.
- Indexes that the Splunk App for Windows Infrastructure requires must be present on all indexers.
msad: for AD health metricswineventlog: for Directory Service, Replication Service, DNS server event logsperfmon: for performance metrics
- The Splunk App for Windows Infrastructure must reside on all search heads in the deployment.
- The Splunk Supporting Add-on for Active Directory (SA-ldapsearch) must be configured properly and reside on all search heads in the deployment. See Troubleshoot issues with SA-LDAPsearch.
eventtypes.conf(in%SPLUNK_HOME%\etc\apps\splunk_app_windows_infrastructure\local) must be configured with the proper indexes for the defined event types.
- Indexes that the Splunk App for Windows Infrastructure requires must be present on all indexers.
- Confirm that the lookup tables for the app have been properly created.
From the Tools and Settings menu, select Build lookups.
Troubleshoot issues with ldapsearch
When the Splunk App for Windows Infrastructure cannot complete a search using the SA-ldapsearch supporting add-on, it notifies you by displaying an error message in Manager's status bar (at the top of your browser window), as follows:
External search command 'ldapsearch' returned error code 1.
ERROR: com.unboundid.ldap.sdk.LDAPException: 80090308: LdapErr: DSID-0C090334, comment: AcceptSecurityContext error, data 525, vece
The Splunk App for Windows Infrastructure also writes a message to $SPLUNK_HOME/var/log/splunk/SA-ldapsearch.log, similar to the following:
2012-08-10 14:58:34.108 -0700 pid=877 com.splunk.program.LDAPSearch:main#-1 ERROR Exception com.unboundid.ldap.sdk.LDAPException thrown: 80090308: LdapErr: DSID-0C090334, comment: AcceptSecurityContext error, data 525, vece^@
If you see an error message similar to this when performing a search, use the following table to decode the data value and figure out how to resolve the error.
| Data value | What it means | What you should do |
|---|---|---|
| 255 | Either the domain was not found or there was a syntax error in the search command. | Confirm that the domain that you want to monitor exists and is configured properly, or that your search string is properly formatted and syntactically correct. |
| 525 | The username provided in ldap.conf is not valid.
|
Edit ldap.conf and provide the correct user, then restart your central Splunk instance.
|
| 52E | The password provided in ldap.conf is not valid.
|
Edit ldap.conf and provide the correct password, then restart your central Splunk instance.
|
| 530 | The user account provided is not allowed to log into Active Directory at this time. | Remove the user's log on time restrictions from within Active Directory, then try again. |
| 531 | The user account provided is not allowed to log into Active Directory from the current server. | Modify the local security policy of the server from which the specified user is trying to log in to Active Directory, then try again. |
| 532 | The user account provided has an expired password. | Change the user's password or set the "Password never expires" bit from within Active Directory, then try again. |
| 533 | The user account provided is disabled. | Re-enable the user account from within Active Directory, then try again. |
| 701 | The user account provided has expired. | Re-enable the user account from within Active Directory, then try again. |
| 773 | The user account provided has the "User must reset password at next logon" bit set. | Un-set the "User must reset password at next logon" bit for the user account from within Active Directory, then try again. |
| 775 | The user account provided is locked because an incorrect password has been entered too many times. | Re-enable the user account from within Active Directory and change the password to a known good one, then try again. |
Windows event log or performance events from universal forwarders go to the 'main' index
When you install a universal forwarder on a Windows server, you must not select any options in the Enable Inputs screen of the installer. Doing so enables the scripted inputs that come with the forwarder by default. Those inputs send data to the "default" index as specified in their configuration files, which, on a standard Splunk installation, is main.
After you install the universal forwarder onto your Windows server, deploy the appropriate add-ons included in the Splunk App for Windows Infrastructure installation package. See "Deploy the Splunk Add-on for Windows" and "Deploy the Splunk Add-ons for Active Directory".
Dashboards fail to load after upgrading the app or Splunk Enterprise
If you experience an issue where some dashboard panels or menus fail to load after you upgrade either Splunk Enterprise or the Splunk App for Windows Infrastructure, clear your web browser's cache, log out of Splunk Enterprise, then log back in. This should fix the problem.
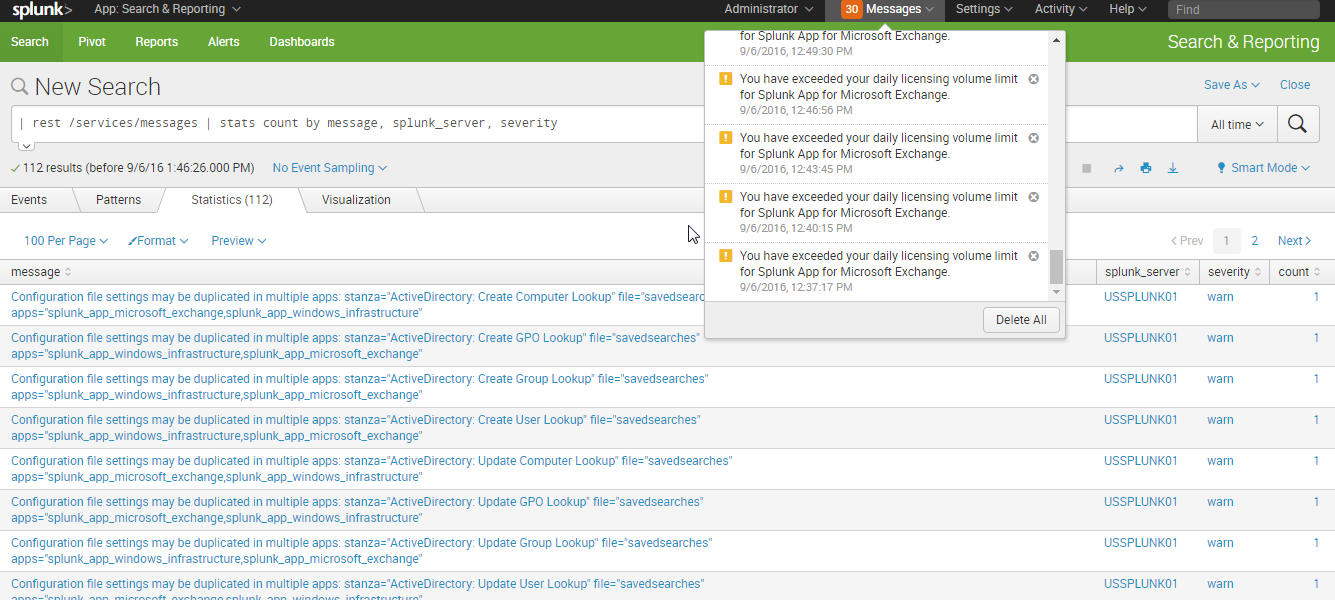
Error message: Configuration file settings may be duplicated in multiple apps
Your deployment receives the following error.
Configuration file settings may be duplicated in multiple apps: stanza="ActiveDirectory: Create Computer Lookup" file="savedsearches" apps="splunk_app_microsoft_exchange,splunk_app_windows_infrastructure"
This error happens when the Splunk App for Windows Infrastructure and the Splunk App for Microsoft Exchange are installed on the same search head. The Splunk App for Windows Infrastructure and the Splunk App for Microsoft Exchange contain identical knowledge objects that cause a conflict when installed on the same search head deployment.
Removing either the Splunk App for Windows Infrastructure or the Splunk App for Microsoft Exchange will resolve this issue.
Lookup errors on all searches for WinEventLog:System:IAS and source:::Security' If running Windows App For Infrastructure 1.5.0 with Splunk_TA_windows 4.8.4.
If you experience the following search errors on UI while running Windows App For Infrastructure 1.5.0 with the Splunk_TA_windows 4.8.4, then remove windows_apps lookup and its transforms definition from Windows App For Infrastructure.
Error 'Could not find all of the specified lookup fields in the lookup table.' for conf 'source::*:Security' and lookup table 'windows_app_lookup'.
Remove windows_apps.csv lookup from main app.
- Remove
windows_appslookup from/etc/shcluster/apps/splunk_app_windows_infrastructure/lookupson the searchhead deployer (In case of standalone searchhead, remove it from/etc/apps/splunk_app_windows_infrastructure/lookups). - Remove following
windows_appslookup definition from/etc/shcluster/apps/splunk_app_windows_infrastructure/default/transforms.confon the searchhead deployer (In case of standalone searchhead, remove it from/etc/apps/splunk_app_windows_infrastructure/default/transforms.conf). - Push bundle from deployer to SHs (In case of standalone searchhead, restart Splunk on SH).
[windows_app_lookup] filename = windows_apps.csv [windows_apps] filename=windows_apps.csv max_matches=1
Precheck error in Splunk App for Windows Infrastructure guided setup for Splunk version 7.0.x
If you're using Splunk version 7.0.x and the Splunk App for Windows Infrastructure version 1.5.2, you may experience an error while running the guided setup precheck step. Bypass the the precheck step and continue. Bypassing the step does not impact app functionality.
tSessions_collection space consumption is very high
- Navigate to Settings > Searches, reports, and alerts.
- Edit and Disable the following saved searches:
tSessions_Lookup_UpdatetSessions_Lookup_Update_Per_DaytSessions_Lookup_Update_For_Lost_DatatSessions_Lookup_Update_One_TimetSessions_Lookup_Migrate
- Run the following command from the terminal to clean your tSessions kvstore collection:
$SPLUNK_HOME/bin/splunk clean kvstore -app splunk_app_windows_infrastructure -collection tSessions_collection - Stop Splunk using the following command:
$SPLUNK_HOME/bin/splunk stop - Remove the below saved search stanza located under
splunk_app_windows_infrastructure/local/savedsearches.conf:[tSessions_Lookup_Update] disabled = 1 [tSessions_Lookup_Update_For_Lost_Data] disabled = 1 [tSessions_Lookup_Update_Per_Day] disabled = 1 [tSessions_Lookup_Update_One_Time] disabled = 1 [tSessions_Lookup_Migrate] disabled = 1
- Remove the following stanza located under
splunk_app_windows_infrastructure/default/collections.conf:
[tSessions_collection] enforceTypes = false profilingEnabled = false
- Remove the following stanzas located under
splunk_app_windows_infrastructure/default/macros.conf:
[session-to-host] definition = lookup tSessions local=true session_id OUTPUTNEW login_username,login_domain,login_host [tsessions] definition = \ `wineventlog-index` eventtype=wineventlog_security session_id="*x*" session_id!="0x3e7" \ | eval login_username=if(eventtype=="msad-successful-user-logons",user,NULL) \ | eval login_domain=if(eventtype=="msad-successful-user-logons",dest_nt_domain,NULL) \ | stats earliest(_time) as _time values(eventtype) as eventtype count as eventcount values(src_ip) as src_ip values(user) as user values(host) as host values(login_username) as login_username values(login_domain) as login_domain by session_id \ | where eventtype=="msad-successful-user-logons" AND eventcount>=1 AND isnotnull(src_ip) AND isnotnull(user) \ | eval login_host=if(src_ip=="127.0.0.1" OR src_ip=="::1" OR src_ip=="-",upper(host),src_ip) \ | table _time,session_id,login_username,login_domain,login_host \ - Remove the following stanzas located under
splunk_app_windows_infrastructure/default/savedsearches.conf:
[tSessions_Lookup_Update] disabled = 0 search = `wineventlog-index` `tsessions`|eval _key = session_id |sort 0 _time|outputlookup tSessions append=true enableSched = 1 cron_schedule = */10 * * * * realtime_schedule = 1 dispatch.earliest_time = -15m dispatch.latest_time = now [tSessions_Lookup_Update_Per_Day] disabled = 0 search = | inputlookup tSessions | where _time > relative_time(now(), "-7d@d") | outputlookup tSessions enableSched = 1 cron_schedule = 0 0 * * 0 realtime_schedule = 1 [tSessions_Lookup_Update_For_Lost_Data] disabled = 0 search = `wineventlog-index` `tsessions`|eval _key = session_id |sort 0 _time|outputlookup tSessions append=true enableSched = 1 cron_schedule = 2 1,2 * * 0 realtime_schedule = 1 dispatch.earliest_time = -0d@d dispatch.latest_time = now [tSessions_Lookup_Update_One_Time] alert.track = 0 dispatch.earliest_time = -7d@d dispatch.latest_time = now search = `wineventlog-index` eventtype=wineventlog_security session_id="*x*" session_id!="0x3e7" earliest=-7d@d latest=now() \ | eval login_username = if(eventtype=="msad-successful-user-logons",user,NULL) \ | eval login_domain=if(eventtype=="msad-successful-user-logons",dest_nt_domain,NULL) \ | stats earliest(_time) as _time values(eventtype) as eventtype count as eventcount values(src_ip) as src_ip values(user) as user values(host) as host values(login_username) as login_username values(login_domain) as login_domain by session_id \ | where eventtype=="msad-successful-user-logons" AND eventcount>=1 AND isnotnull(src_ip) AND isnotnull(user) \ | eval login_host=if(src_ip=="127.0.0.1" OR src_ip=="::1" OR src_ip=="-",upper(host),src_ip) \ | table _time,session_id,login_username,login_domain,login_host |eval _key = session_id |sort 0 _time|outputlookup tSessions append=true [tSessions_Lookup_Migrate] disabled = 0 search = | inputlookup tSessions.csv | outputlookup tSessions enableSched = 0 - Remove the following stanzas located under
splunk_app_windows_infrastructure/default/transforms.conf:[tSessions] external_type = kvstore time_field=_time collection = tSessions_collection fields_list = _key, _time, session_id, login_username, login_domain, login_host</li>
- Take a backup of the following files:
splunk_app_windows_infrastructure/default/data/ui/views/ad_audit_gpo.xmlsplunk_app_windows_infrastructure/default/data/ui/views/ad_sec_admin_audit.xmlsplunk_app_windows_infrastructure/default/data/ui/views/ad_chg_gpo.xmlsplunk_app_windows_infrastructure/appserver/static/js/splunk_app_windows_infrastructure/setup/finish_page.jssplunk_app_windows_infrastructure/appserver/static/js/splunk_app_windows_infrastructure/setup/AppSetupConfigs/WinfraSetupConfig.js
- Replace the below files at
splunk_app_windows_infrastructure/default/data/ui/views:
- Replace the finish_page.js file at
splunk_app_windows_infrastructure/appserver/static/js/splunk_app_windows_infrastructure/setup/. - Replace the WinfraSetupConfig.js file at
splunk_app_windows_infrastructure/appserver/static/js/splunk_app_windows_infrastructure/setup/AppSetupConfigs/. - Start Splunk using the
$SPLUNK_HOME/bin/splunk startcommand. - Click on the bump button at
<splunkurl>:8000/en-US/_bump.
| Build custom dashboards | Size and scale a Splunk App for Windows Infrastructure deployment |
This documentation applies to the following versions of Splunk® App for Windows Infrastructure (Legacy): 2.0.3, 2.0.4
 Download manual
Download manual
Feedback submitted, thanks!