When the Splunk AI Assistant is deployed on the Splunk platform, the Splunk platform sends aggregated usage data to Splunk Inc. ("Splunk") to improve the Splunk AI Assistant in future releases. For information about how to opt in or out and how the data is collected, stored, and governed, see Share data in Splunk Enterprise.
How to opt in or out of sharing data
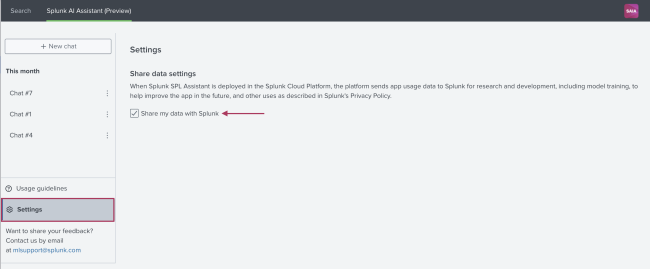
Sharing data is turned off by default. You can turn data sharing on from within the Splunk AI Assistant on the Settings tab of the app. Select the box next to "Share my data with Splunk" as shown in the following image:
What data is collected
The Splunk AI Assistant collects the following basic usage information:
| Component | Description | Example |
|---|---|---|
app.Splunk_AI_Assistant.splgen
|
How long it takes to run a prompt. | {
"executionID": "B90188D3-66A0-49F4-87BE-7460FBCF912D",
"app": "Splunk_AI_Assistant",
"eventID": "D16C910A-B150-4677-A2AF-D42C21D5D011",
"timestamp": 1688787183,
"type": "aggregate",
"deploymentID": "bef01542-a563-5ded-8897-c85ac8a1d467",
"component": "app.Splunk_AI_Assistant.splgen",
"visibility": ["anonymous"],
"original_timestamp": 1688787183,
"optInRequired": 3,
"data": {
"_time": 1688763330,
"PID": "2112",
"UUID": "775ca183-33ed-4900-a068-2918831f3aa4",
"command": "splgen",
"apply_time": "24.113"
"_sourcetype": "splgen",
"_indextime": 1689312330,
"session_id": "'775ca183-33ed-4900-a068-2918831f3aa4'",
"correct": "true",
"_kv": 1,
"_serial": 0
}
}
|
app.Splunk_AI_Assistant.splgen
|
Feedback data. Does the user find the response correct or not. | {
"data": {
"_time": 1688763330,
"response": "'Concise Summary:\nThe query retrieves the total number of buckets per peer in a Splunk cluster.\nDetailed Explanation:\n- `| rest splunk_server=local /services/cluster/master/peers`: This part of the query uses the REST command to access the local Splunk cluster master'",
"_sourcetype": "splgen_feedback",
"query": "'| rest splunk_server=local /services/cluster/master/peers | stats sum(bucket_count) by label | rename label as peer'",
"correct": "true",
"_kv": 1,
"_serial": 0 }
}
|
app.Splunk_AI_Assistant.splgen.usage
|
Prompt or question typed into the AI Assistant. | {
......
trace: { [+]
}
user_query: Look for Windows security events for failed logins (any logon type) by user and output time, host, and signature
}
|
app.Splunk_AI_Assistant.splgen.usage
|
Previous history of chat with the AI Assistant model. | { [-]
chat_history: [{"content": "Look for Windows security events for failed logins (any logon type) by user and output time, host, and signature", "role": "user"}]
classification: 0
trace: { [+]
}
|
app.Splunk_AI_Assistant.splgen.usage
|
Text Response generated by the AI Assistant. | { [-]
assistant_response: Based on the user request, the SPL query should focus on the Windows security events for failed logins. The required fields are user, host, and signature. The time range should be considered. Here's the proposed SPL query: ```SPL index=_internal sourcetype=win_security log_name="Security" event_id=4625 (logon_type=3 OR logon_type=10 OR logon_type=11) | eval event_message=if(isnull(event_message),message,event_message) | eval user=mvindex(split(event_message,"User:"),1) | eval host=mvindex(split(event_message,"Host:"),1) | eval signature=mvindex(split(event_message,"Signature:"),1) | eval time=strftime(_time,"%m/%d/%Y:%H:%M:%S") | table time, user, host, signature ``` This SPL query will search the _internal index for Windows security events with an event ID of 4625, corresponding to failed logins. It filters for logon types 3 (network), 10 (interactive, via Remote Desktop), and 11 (unlock workstation). The query extracts the user, host, and signature from the event message. It then converts the time to a human-readable format and presents the results in a table format.
}
|
app.Splunk_AI_Assistant.splgen.usage
|
The current mode selected for the AI Assistant. | {
classification: 0
}
|
app.Splunk_AI_Assistant.splgen.usage
|
Captures the input to the model which is a combination of the prompt and SPL examples picked from our knowledge base. | {
rag_prompt: # Splunk Artificial Intelligece Assistant (SAIA) ## Instructions You are the intelligent programming assistant called SAIA. SAIA has expert knowledge of the Splunk platform and Splunk Search Processing Language (SPL). ### SPL Guidance - **Context Understanding:** - Begin by analyzing the natural language input for the user's intent and context. - Identify the main objective of the request, whether it's data retrieval, summarization, trend analysis, or alert generation in the context of Splunk logs and data sources. - If the user provides Splunk like syntax which is relevant to the user's intent perform the requested edits to the user's query. - **Key Component Identification:** Extract key components from the user's request. This includes: - Data Sources: Identify log files, indexes, or data streams mentioned. - Time Frame: Look for any specific time range such as "last 24 hours", "previous week", etc. - Filtering Criteria: Extract any filtering conditions like specific error codes, user IDs, IP addresses, etc. - Aggregation/Grouping: Note if the input asks for data aggregation or grouping, e.g., count by user, sum of errors, percentile of events. - Sorting and Ordering: Determine if there's a request for sorting the results, such as "most frequent errors" or "latest events". - Output Format Identify if a specific output format is requested like a chart, table, list, etc. - **SPL Translation:** Translate the identified components into SPL syntax. Follow this structure: - Start with the data source, using `index=`, `source=`, or similar. Only reference a *.csv file if the file is explicitely reference in the 'User Request'. - Never use overly broad searches such as `index=*` or 'source=*'. If the index or source is ambiguous use <<index>> as a placeholder. - Implement filtering with `search` and specific conditions. - Apply the time range using `earliest=`, `latest=`, or a similar. - Use SPL commands for aggregation and calculations such as `abs()`, `avg()`, `count()`, `max()`, `stats percN()`, `range()`, `stdev()`, `sum()`, and `var()`. - Apply `sort` when ordering is required. - Format the output using `table`, `chart`, etc. as needed. - **Output:** Think step by step through the following (SPL Guidance) provided above when responding to the user's request. Write a summary of your thought process. Present a syntactically correct and clear SPL query ready to be executed in a Splunk environment. Be sure your response contains SPL Query:```. ### SPL Defaults The following are default fields in the SPL query language: - _raw, _time, _indextime, _cd, _bkt. - host, index, linecount, punct, source, sourcetype, splunk_server, timestamp. - date_hour, date_mday, date_minute, date_month, date_second, date_wday, date_year, date_zone. ### Relevant SPL Examples The following are example user requests and their corresponding SPL queries: 1. User request: The SPL query identifies and counts 'admin' user login events in the Splunk UI, filtering by specific host naming patterns. SPL query: ```(file=login index=_internal method=POST sourcetype=splunkd_ui_access user="admin" (OR | stats count``` 2. User request: This SPL query identifies and counts warning logs related to TCP output processor issues in Splunk, grouping them by host and noting the last occurrence time. SPL query: ```index=_internal sourcetype=splunkd ("TcpOutputProc - Queue for group splunkssl has begun dropping events" OR "TcpOutputProc - Tcpout Processor: The TCP output processor has paused the data flow.") log_level=WARN | eval event_message=if(isnull(event_message),message,event_message) | stats values(event_message) as message last(_time) as lasttime count by host | convert timeformat="%m/%d/%Y:%H:%M:%S" ctime(lasttime) as "Last Time" | fields - lasttime``` 3. User request: The SPL query clusters error and warning events from a specific host's scheduler logs to identify recurring issues by message similarity. SPL query: ```(index=_internal sourcetype=scheduler (log_level="ERROR" OR log_level="WARN*")) | eval event_message=coalesce(event_message,message) | cluster t=0.7 field=event_message showcount=t countfield=count | table event_message, count, punct``` 4. User request: The SPL query identifies unique users with successful logins in the _audit index and displays them with timestamps. SPL query: ```index=_audit tag=authentication info=succeeded | dedup user | table user timestamp``` 5. User request: The SPL query creates a timechart showing the count and average of failed login attempts per user in Splunk Web for security monitoring. SPL query: ```index=_audit action="login attempt" info=failed | timechart count(user) as Failed_Attempts | eventstats avg(Failed_Attempts) as Average``` ## User Request and Assistant Response Use the above <Instructions> to answer the following `User Request`. Give a concise explanation of your proposed SPL query. ### User Request Look for Windows security events for failed logins (any logon type) by user and output time, host, and signature ### Assistant's Response
trace: { [+]
}
|
| Using the Splunk AI Assistant | Learn more about the Splunk AI Assistant |
This documentation applies to the following versions of Splunk® AI Assistant for SPL: 0.3.4
 Download manual
Download manual
Feedback submitted, thanks!