Migrate from the Splunk App for Microsoft Exchange to the Content Pack for Microsoft Exchange
Dashboards of Splunk App for Microsoft Exchange are packaged and available in Splunk App for Content Packs. Based on the use case scenarios for the dashboards, these dashboards have been packaged in the following two content packs:
- Content Pack for Microsoft Exchange: Contains the dashboards and Knowledge objects related to Exchange. For more details, see Dashboard reference for the Content Pack for Microsoft Exchange.
- Content Pack for Windows Dashboards and Reports: Contains the dashboards and knowledge objects for Windows and Active Directory. For more details, see Dashboard reference for the Content Pack for Windows Dashboards and Reports.
Depending on the scenario that you're using Splunk App for Microsoft Exchange for, you may want to use one or both of the above mentioned Content Packs.
Users of ITSI version 4.9.0 or higher, or IT Essentials Work version 4.9.0 or higher, can migrate from the legacy app to the content pack to take advantage of a consolidated experience. In addition, migrating means you can upgrade all content packs by upgrading the one app, the Splunk App for Content Packs.
Refer to the following table to compare the features of the app versus the content pack:
| Feature | Splunk App for Microsoft Exchange | Splunk Content Pack for Microsoft Exchange | Splunk Content Pack for Windows Dashboards and Reports |
|---|---|---|---|
| Installation and Configuration | Manual | Automatic with Splunk App for Content Packs | Automatic with Splunk App for Content Packs |
| Built-in Microsoft Best Practices | No | Yes | Yes |
| Dashboards | Yes - Exchange + Windows + Active Directory use case | Yes - Exchange use case | Yes - Windows use case + Active Directory |
| Entity Types | 0 | 0 | 1 |
| Glass Tables | 0 | 3 | 0 |
| KPIs | 0 | 440 | 0 |
| Services | 0 | 64 | 0 |
On October 22 2021, the Splunk App for Microsoft Exchange will reach its end of life. After this date, Splunk will no longer maintain or develop this product. The functionality in this app is migrating to the Content Pack for Microsoft Exchange.
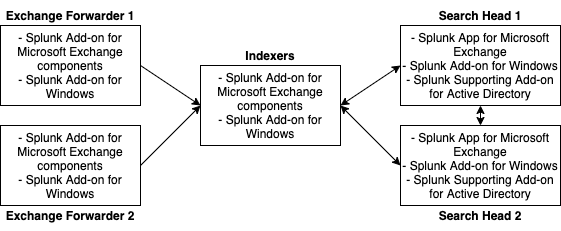
If you are currently using the Splunk App for Microsoft Exchange your deployment might look like the following image:
| Exchange forwarder | Indexer | Search head | |
|---|---|---|---|
| Splunk Add-on for Microsoft Exchange | ✓ | ✓ | |
| Splunk Add-on for Windows | ✓ | ✓ | ✓ |
| Splunk App for Microsoft Exchange | ✓ | ||
| Splunk Supporting Add-on for Active Directory | ✓ |
You can review the dashboards included in the Content Pack for Microsoft Exchange before you migrate. See, Dashboard reference for the Content Pack for Microsoft Exchange.
Migration steps for Cloud environments
For migration on Cloud, file a ticket on the Splunk Support Portal in the Support and Services section. Splunk Cloud TechOps personnel will assist you with the migration from Splunk App for Microsoft Exchange to Content Pack for Microsoft Exchange. Follow the steps mentioned in the sub-sections below to update the configurations (in the case of custom index usage), and access the dashboards.
Update configuration and access dashboards for Microsoft Exchange
If you are ingesting Exchange data in custom indexes other than the default indexes used by Splunk Add-on for Microsoft Exchange and Splunk App for Microsoft Exchange, then perform the following steps after your stack is migrated from Splunk App for Microsoft Exchange to Splunk App for Content Packs (which includes the Content Pack for Windows Dashboards and Reports and the Content Pack for Microsoft Exchange).
- Open the Splunk IT Essentials Work or Splunk IT Service Intelligence application.
- Navigate to Settings > Event types.
- Search for the respective Event type in Search bar mentioned in the RHS column of the table.
- Click on Event type.
- Update the definition with the custom index value.
| Type of data ingested from Splunk Add-on for Microsoft Exchange/Splunk Add-on for Microsoft Windows in custom index | Corresponding Eventtype to be configured in Microsoft Exchange Content Pack to configure custom indexes | Example value for Eventtype |
|---|---|---|
| Wineventlog data | wineventlog-index | index = custom_index1 AND index = custom_index2 |
| Perfmon data | msperfmon-index | index = custom_index1 AND index = custom_index2 |
| MSAD data | msad-index | index = custom_index1 AND index = custom_index2 |
| Windows data | windows-index | index = custom_index1 AND index = custom_index2 |
| MS Exchange data | msexchange-index | index = custom_index1 AND index = custom_index2 |
After you perform the steps above, you can use the knowledge objects included in the Content Pack for Microsoft Exchange. For a list of the included dashboards, see Dashboard reference for the Content Pack for Microsoft Exchange.
Update configuration and access the dashboards for Windows
For an explanation of how to update the configuration of and access to dashboards for Windows, see the "Update configuration and access the dashboards" section of Migration for cloud environments in the Content Pack for Windows Dashboards and Reports.
Migration steps for on-premises standalone or distributed environments
You can migrate from Splunk App for Microsoft Exchange to the Content Pack for Microsoft Exchange by following the procedures in this section.
Before you migrate
Before migrating to Content Pack for Microsoft Exchange, make sure to follow the steps below to make a backup of your custom configurations and lookups.
- Make a backup of the directories below present in the
splunk_app_microsoft_exchangepackage in $SPLUNK_HOME/etc/apps on each search head:/localdirectory which contains all the local configurations under conf files/lookupsdirectory which contains the CSV lookups
- Make a backup of the KV Store lookups present in the app:
- Identify the KV store captain from each search head (perform this step if you have multiple search heads in your environment):
$SPLUNK_HOME/bin/splunk show kvstore-status - Log in to the KV store captain search head and run the following command:
$SPLUNK_HOME/bin/splunk backup kvstore -archiveName splunk_app_microsoft_exchange_kvstore_backup -appName splunk_app_microsoft_exchange - Identify the latest backup in
$SPLUNK_HOME/var/lib/splunk/kvstorebackupand copy the splunk_app_microsoft_exchange_kvstore_backup.tar.gz backup file to $SPLUNK_HOME/tmp. This archive file will be required to restore the App lookup data during migration.
- Identify the KV store captain from each search head (perform this step if you have multiple search heads in your environment):
- Perform the following steps on each role present in the instance.
- Navigate to Settings > Roles.
- Click on Edit > Edit.
- Navigate to Assign Roles.
- Deselect the
exchange-adminrole in the inheritance tab if it is selected. - Click on Save.
- Perform the following steps on each user inheriting the
exchange-adminrole. - Navigate to Settings > Users.
- Click on Edit > Edit.
- Navigate to Assign Roles.
- From Selected item(s) > Remove
exchange-adminrole. - Click on Save.
If you are currently using the Splunk App for Microsoft Exchange, your deployment setup might resemble the following table:
| Data collection node (forwarder) | Indexer | Search head | |
|---|---|---|---|
| Splunk Add-on for Windows | ✓ | ✓ | ✓ |
| Splunk App for Microsoft Exchange | ✓ | ||
| Splunk Supporting Add-on for Active Directory | ✓ |
Steps to migrate from Splunk App for Microsoft Exchange to Content Pack for Microsoft Exchange
Follow these steps to migrate from Splunk App for Microsoft Exchange to Content Pack for Microsoft Exchange. Be sure to make a backup of existing lookups and custom configurations before you migrate, as described in Before you migrate.
- Perform the following steps on each search head present in your deployment to disable the Splunk App for Microsoft Exchange:
- Navigate to
{SPLUNK_HOME}/etc/apps/splunk_app_microsoft_exchange/local/app.conf(create app.conf file in local directory if it is not present) and edit the "state" property of "install" stanza as mentioned below: - Restart the instance:
$SPLUNK_HOME/bin/splunk restart - Install ITSI or IT Essentials Work on the same search head with Exchange data according to your type of deployment. Refer to these topics in the Splunk IT Service Intelligence Install and Upgrade Manual:
- Install the Splunk App for Content Packs according to your type of deployment:
[install] state = disabled
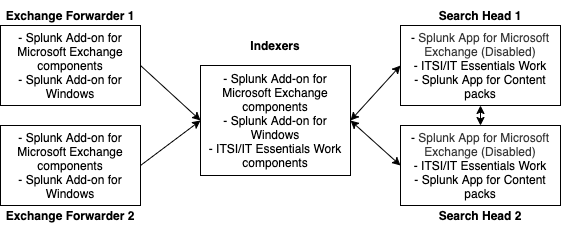
When you've completed the previous steps, the deployment is installed as shown in the following table:
| Data collection node (forwarder) | Indexer | Search head | |
|---|---|---|---|
| Splunk Add-on for Windows | ✓ | ✓ | ✓ |
| ITSI or IT Essentials Work | ✓ | ✓ | |
| Splunk App for Microsoft Exchange | Disabled | ||
| Splunk App for Content Packs | ✓ | ||
| Splunk Supporting Add on For Active Directory | ✓ |
After following the previous steps, the deployment looks like the following image:
After you install the Splunk App for Content Packs with Content Pack for Microsoft Exchange and Content Pack for Windows Dashboards and Reports
- Restore the backup of the KV Store lookup:
- Identify the KV store captain from different search heads. (Perform this step if the you have a search head cluster deployment). For a single search head deployment, the only search head will be the KV store captain:
$SPLUNK_HOME/bin/splunk show kvstore-status - If KV store captain is changed, then move the KV store backup file from the old KV store captain to the current KV store captain. Run the following command on the search head where KV store backup taken as part of the Before you migrate section:
scp /path_of_splunk_app_microsoft_exchange_kvstore_backup.tar.gz {SPLUNK_USER}@{$search_head_ip}:/{SPLUNK_HOME}/tmp - On your current KV store captain, untar the backup tar file:
tar -xzvf $SPLUNK_HOME/tmp/splunk_app_microsoft_exchange_kvstore_backup.tar.gz - Rename the folder name:
mv $SPLUNK_HOME/tmp/splunk_app_microsoft_exchange $SPLUNK_HOME/tmp/DA-ITSI-CP-microsoft-exchange - Tar the upgraded folder name:
tar -czf $SPLUNK_HOME/tmp/DA-ITSI-CP-microsoft-exchange_kvstore_backup.tar.gz DA-ITSI-CP-microsoft-exchange - Rename the folder name:
mv $SPLUNK_HOME/tmp/DA-ITSI-CP-microsoft-exchange $SPLUNK_HOME/tmp/DA-ITSI-CP-windows-dashboards - Tar the upgraded folder name:
tar -czf $SPLUNK_HOME/tmp/DA-ITSI-CP-microsoft-exchange_kvstore_backup.tar.gz DA-ITSI-CP-windows-dashboards - Move the
$SPLUNK_HOME/tmp/DA-ITSI-CP-microsoft-exchange_kvstore_backup.tar.gzfile in$SPLUNK_HOME/var/lib/splunk/kvstorebackup. - Move the
$SPLUNK_HOME/tmp/DA-ITSI-CP-windows-dashboards_kvstore_backup.tar.gzfile in$SPLUNK_HOME/var/lib/splunk/kvstorebackup. - Restore the backup for Content Pack for Microsoft Exchange content pack
splunk restore kvstore -archiveName DA-ITSI-CP-microsoft-exchange_kvstore_backup.tar.gz -appName DA-ITSI-CP-microsoft-exchange - Restore the backup for Content Pack for Windows Dashboards and Reports content pack
splunk restore kvstore -archiveName DA-ITSI-CP-windows-dashboards_kvstore_backup.tar.gz -appName DA-ITSI-CP-windows-dashboards - Perform the steps below on each search head present in your deployment:
- Move the following directories from the App package to DA-ITSI-CP-microsoft-exchange folder that are backed up as part of the Before you migrate section:
/localdirectory collected from the app which contains all the local configurations of the app/lookupsdirectory
- Remove
app.conffile from local directory. - Remove
msftapps_exchange_setup.conffile from local directory. - Remove
splunk_msftapp.conffile from local directory. - Restart the instance:
$SPLUNK_HOME/bin/splunk restart - If you are ingesting the Exchange data in custom indexes other than the default indexes used by Splunk Add-on for Microsoft Exchange and Splunk App for Microsoft Exchange, then perform the following steps after your stack is migrated from Splunk App for Microsoft Exchange to Splunk App for Content Packs (with the Content Pack for Windows Dashboards and Reports and Content Pack for Microsoft Exchange).
- Go to Splunk IT Essentials Work or Splunk IT Service Intelligence.
- Navigate to Settings > Event types
- Search for Event type in the Search bar mentioned in the RHS column of the table
- Click on Event type
- Update the definition with the custom index value
| Type of data ingested from Splunk Add-on for Microsoft Exchange/Splunk Add-on for Microsoft Windows in custom index | Corresponding Eventtype to be configured in Microsoft Exchange Content Pack to configure custom indexes | Example value for Eventtype |
|---|---|---|
| Wineventlog data | wineventlog-index | index = custom_index1 AND index = custom_index2 |
| Perfmon data | msperfmon-index | index = custom_index1 AND index = custom_index2 |
| MSAD data | msad-index | index = custom_index1 AND index = custom_index2 |
| Windows data | windows-index | index = custom_index1 AND index = custom_index2 |
| MS Exchange data | msexchange-index | index = custom_index1 AND index = custom_index2 |
| Type of data ingested from Splunk Add-on for Microsoft Windows in custom index | Corresponding Eventtype to be configured in Windows Dashboards and Reports Content Pack to configure custom indexes | Example value for Eventtype |
|---|---|---|
| Wineventlog data | wineventlog_index_windows | index = custom_index1 AND index = custom_index2 |
| Perfmon data | perfmon_index_windows | index = custom_index1 AND index = custom_index2 |
| MSAD data | msad_index_windows | index = custom_index1 AND index = custom_index2 |
| Windows data | windows_index_windows | index = custom_index1 AND index = custom_index2 |
The searches of the Splunk App for Microsoft Exchange use a macro-based index, but searches of Content Pack for Microsoft Exchange contain eventtype-based specifications. You will need to configure corresponding eventtype indexes after migrating to Content Pack for Microsoft Exchange.
For more information about configuring eventtype indexes, see Set up multiple indexes.
Install and configure the Content Pack for Microsoft Exchange
Dashboards present in the Splunk App for Microsoft Exchange are installed by default in Content Pack for Microsoft Exchange. Follow the steps below to enable the Savedsearches used by Content Pack Dashboards and ITSI objects, and install additional ITSI objects provided by Content Pack:
- Make sure that the Exchange data collected using Splunk Add-on for Microsoft Exchange is searchable from the search head where you installed the Splunk App for Content Packs.
- Follow the steps to install and configure the Content Pack for Microsoft Exchange.
- Access the dashboards of Microsoft Exchange Content Pack by opening Dashboards > Dashboards from ITSI or IT Essentials Work. The dashboards listed with App name of DA-ITSI-CP-microsoft-exchange are from the Content Pack. Select the name of the dashboard you want to open.
Install and configure the Content Pack for Windows Dashboards and Reports
Dashboards present in the Splunk App for Microsoft Exchange are installed by default in Content Pack for Windows Dashboards and Reports. Follow the below steps to enable the Savedsearches used by Content Pack Dashboards and ITSI objects, and install additional ITSI objects provided by Content Pack.
- Make sure that the Windows data collected using Splunk Add-on for Microsoft Windows is searchable from the search head where you installed the Splunk App for Content Packs.
- Follow the steps to install and configure the Content Pack for Windows Dashboards and Reports.
- Access the dashboards of Windows Dashboards and Reports Content Pack by opening Dashboards > Dashboards from ITSI or IT Essentials Work. The dashboards listed with App name of DA-ITSI-CP-windows-dashboards are from the Content Pack. Select the name of the dashboard you want to open.
Access the Microsoft Exchange dashboards in the content pack
To access the dashboards from the Content Pack for Microsoft Exchange:
- In Splunk Web, open ITSI or IT Essentials Work.
- From the main navigation bar choose Dashboards > Dashboards.
- From the list of dashboards, those with the App name of DA-ITSI-CP-microsoft-exchange are from the Content Pack for Microsoft Exchange. Select the name of the dashboard you want to open.
This documentation applies to the following versions of Content Pack for Microsoft Exchange: 1.5.1, 1.5.2, 1.6.0, 1.6.1, 1.7.0
 Download manual
Download manual
Feedback submitted, thanks!