Migrate from the Splunk Supporting Add-on for VMware or the Splunk App for VMware to the Content Pack for VMware Dashboards and Reports
On January 11, 2023, the Splunk Supporting Add-on for VMware will reach its end of life and Splunk will no longer maintain or develop this product.
The Content Pack for VMware Dashboards and Reports replicates the dashboards and reports available in the Splunk Supporting Add-on for VMware and the Splunk App for VMware. Migrate from these legacy apps to the content pack to take advantage of a consolidated experience within one app, either ITSI or IT Essentials Work. In addition, you can upgrade all content packs by upgrading the one app, the Splunk App for Content Packs.
On August 31, 2022, the Splunk App for VMware will reach its end of life. After this date, Splunk will no longer maintain or develop this product. The functionality in this app is migrating to the Content Pack for VMware Dashboards and Reports.
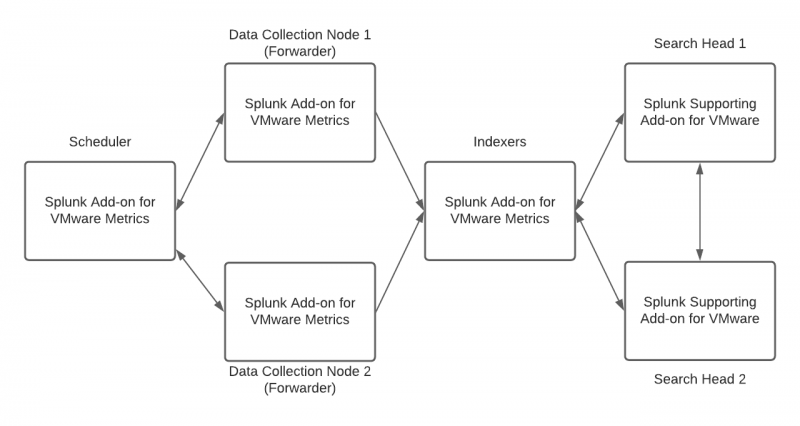
If you are currently using Splunk Supporting Add-on for VMware your deployment might look like the following image and table:
| Component | Search head | Scheduler | Indexer | Data Collection Node (DCN) | ESXi log forwarder | vCenter log forwarder |
|---|---|---|---|---|---|---|
| Splunk App for VMware | ✓ | |||||
| Splunk Add-on for VMware | ✓ | ✓ | ✓ | |||
| Splunk Add-on for ESXi Logs | ✓ | ✓ | ✓ | |||
| Splunk Add-on for vCenter Logs | ✓ | ✓ | ✓ | |||
| Splunk Add-on for VMware Indexes | ✓ | |||||
| Splunk Add-on for VMware Extractions | ✓ |
You can review the dashboards included in the Content Pack for VMware Dashboards before you migrate. See Dashboard reference for the Content Pack for VMware Dashboards and Reports.
Migration steps for Cloud environments
Splunk App for VMware consumes data produced from Splunk Add-on for VMware. The Content Pack for VMware Dashboards and Reports consumes data produced from Splunk Add-on for VMware Metrics.
Before you submit a request for migration
Before you submit a request to migrate from Splunk App for VMware to Content Pack for VMware Dashboards and Reports, make sure that you have configured Splunk Add-on for VMware Metrics to forward data in your Splunk Cloud environment. See Installation and Configuration Overview of Splunk Add-on for VMware Metrics to install and configure Splunk Add-on for VMware Metrics in your environment.
After Splunk Add-on for VMware Metrics is configured to ingest the data in Splunk Cloud environment, to start migrating from Splunk App for VMware to Content Pack for VMware Dashboards and Reports on Cloud, open a service ticket on the Splunk Support Portal, in the Support and Services section. Splunk Cloud TechOps will assist you with migration from Splunk App for VMware to Content Pack for VMware Dashboards and Reports.
Migration steps for On-Premises environments
Splunk App for VMware consumes the data collected by Splunk Add-on for VMware, while Content Pack for VMware Dashboards and Reports consumes the data collected by Splunk Add-on for VMware Metrics.
Update the VMware data collection mechanism
If you plan to use Content Pack for VMware Dashboards and Reports Content Pack in your environment, then configure Splunk Add-on for VMware Metrics to collect the VMware data in that environment. For steps to install and configure Splunk Add-on for VMware Metrics, see Installation and Configuration Overview of Splunk Add-on for VMware Metrics.
Splunk Add-on for VMware and Splunk Add-on for VMware Metrics can not co-exist on same Scheduler/DCN components. Make sure to disable one or the other if you are planning to install both add-ons on the same machines. Failure to first one or the other can cause conflicts between knowledge objects.
Before you migrate
Before migrating to Content Pack for VMware Dashboards and Reports, make sure to follow the steps below to make a backup of your custom configurations and lookups.
- Make a backup of the following directories present in the splunk_for_vmware package present in
$SPLUNK_HOME/etc/appson the search head where the App is being used:/localdirectory that contains all the local configurations under conf files/lookupsdirectory that contains the CSV lookups
- Make a backup of the configuration files from the local folder of the SA-VMW-HierarchyInventory package on the search head where App is being used:
datamodels.conf
- Make a backup of the lookups from the SA-VMW-HierarchyInventor/lookups package in
$SPLUNK_HOME/etc/appson the search head where the App is being used:DatastoreList.csvFullHierarchy.csvTimeAboutHost.csvTimeClusterServicesAvailability.csvTimeDatastoreSummary.csvTimeInvHostHardwareAndLicense.csvUniqueNameLookup.csv
- Make a backup of the lookups from the SA-VMW-Performance package on the search head where the App is being used:
ACFields.csvHSFieldList.csvHSInstanceList.csv
- Make a backup of the lookups from the SA-VMW-LogEventTask package on the search head where the App is being used:
vmware_event_lookup.csvvmware_task_lookup.csv
- Perform the following steps on each role present in the instance:
- Navigate to Settings > Roles
- Click on Edit > Edit
- Deselect the
splunk_vmware_adminrole from the Inheritance tab if shows as selected. - Click on Save.
- Perform the following steps on user inheriting the
splunk_vmware_userrole:- Navigate to Settings > Users.
- Click on Edit > Edit.
- Navigate to Assign Roles.
- From Selected item(s) > Remove
splunk_vmware_userrole. - Click on Save.
Steps to migrate from Splunk App for VMware to Content Pack for VMware Dashboards and Reports
Follow the procedure below to migrate from Splunk App for VMware to Content Pack for VMware Dashboards and Reports. Make sure you've backed up existing lookups and custom configurations before you start following the steps below.
- Perform the steps below on each Search Head present in your deployment to disable the Splunk App for VMware:
- Navigate to
{SPLUNK_HOME}/etc/apps/splunk_for_vmware/local/app.conf(create app.conf file in local directory if it is not present) - Edit the "state" property of the "install" stanza as shown below:
- Perform the steps below on each Search Head present in your deployment to disable the Splunk App for VMware Performance:
- Navigate to
{SPLUNK_HOME}/etc/apps/SA-VMW-Performance/local/app.conf(create app.conf file in local directory if it is not present) - Edit the "state" property of the "install" stanza as shown below:
- Perform the steps below on each Search Head present in your deployment to disable the Splunk App for Threshold:
- Navigate to
{SPLUNK_HOME}/etc/apps/SA-Threshold/local/app.conf(create app.conf file in local directory if it is not present) - Edit the "state" property of the "install" stanza as shown below:
- Perform the steps below on each Search Head present in your deployment to disable the Splunk App for VMware Log Event Task:
- Navigate to
{SPLUNK_HOME}/etc/apps/SA-VMW-LogEventTask/local/app.conf(create app.conf file in local directory if it is not present) - Edit the "state" property of the "install" stanza as shown below:
- Perform the steps below on each Search Head present in your deployment to disable the Splunk App for VMware NetApp Utils:
- Navigate to
{SPLUNK_HOME}/etc/apps/SA-VMNetAppUtils/local/app.conf(create app.conf file in local directory if it is not present) - Edit the "state" property of the "install" stanza as shown below:
- Perform the steps below on each Search Head present in your deployment to disable the Splunk App for VMware Hierarchy Inventory:
- Navigate to
{SPLUNK_HOME}/etc/apps/SA-VMW-HierarchyInventory/local/app.conf(create app.conf file in local directory if it is not present) - Edit the "state" property of the "install" stanza as shown below:
- Perform the steps below on each Search Head present in your deployment to disable the Splunk Add-on for VMware Extractions:
- Navigate to
{SPLUNK_HOME}/etc/apps/TA-VMW-FieldExtractions/local/app.conf(create app.conf file in local directory if it is not present) - Edit the "state" property of the "install" stanza as shown below:
- Perform the steps below on each Search Head present in your deployment to disable the Splunk Add-on for VMware:
- Navigate to
{SPLUNK_HOME}/etc/apps/Splunk_TA_vmware/local/app.conf(create app.conf file in local directory if it is not present) - Edit the "state" property of the "install" stanza as shown below:
- Perform the steps below on each Search Head present in your deployment to disable the Splunk App for Hydra:
- Navigate to
{SPLUNK_HOME}/etc/apps/SA-Hydra/local/app.conf(create app.conf file in local directory if it is not present) - Edit the "state" property of the "install" stanza as shown below:
- Restart the all the Search Heads and Indexers present in your deployment.
- Install IT Service Intelligence or IT Essentials Work on the same search head with VMware data according to your type of deployment. Refer to these topics in the Splunk IT Service Intelligence Install and Upgrade Manual:
- Install Splunk IT Service Intelligence on a single instance.
- Install Splunk IT Service intelligence in a distributed environment.
- Install IT Essentials Work.
- Install the Splunk App for Content Packs according to your type of deployment:
- Install the Splunk App for Content Packs in a single on premises environment.
- Install the Splunk App for Content Packs in a distributed environment.
- Install the Splunk Add-on for VMware Metrics according to your type of deployment:
- Install the Splunk Add-on for VMware Metrics in a single on-premises environment
- Install the Splunk Add-on for VMware Metrics on a distributed environment
- Install the Splunk Add-on for VMware Metrics Indexes according to your type of deployment:
[install] state = disabled
[install] state = disabled
[install] state = disabled
[install] state = disabled
[install] state = disabled
[install] state = disabled
[install] state = disabled
[install] state = disabled
[install] state = disabled
$SPLUNK_HOME/bin/splunk restart
After following the previous steps, the deployment is installed as shown in the following table.
| Component | Search head | Scheduler | Indexer | Data Collection Node (DCN) |
ESXi log forwarder |
vCenter log forwarder |
|---|---|---|---|---|---|---|
| Splunk App for VMware | Disabled | |||||
| Splunk Add-on for VMware | Disabled | Disabled | Disabled | |||
| Splunk Add-on for ESXi Logs | ✓ | ✓ | ✓ | |||
| Splunk Add-on for vCenter Logs | ✓ | ✓ | ✓ | |||
| Splunk Add-on for VMware Indexes | ✓ | |||||
| Splunk Add-on for VMware Extractions | Disabled | |||||
| ITSI or IT Essentials Work | ✓ | ✓ | ||||
| Splunk App for Content Packs | ✓ | |||||
| Splunk Add-on for VMware Metrics | ✓ | ✓ | ||||
| Splunk Add-on for VMware Metrics Indexes | ✓ |
Splunk Add-on for VMware Indexes is not automatically disabled or deleted from the environment to avoid data loss. After you are ready to use the Content Pack for VMware Dashboards and Reports and Splunk Add-on for VMware Metrics, you can follow the steps below to disable the app in your environment:
- Navigate to
{SPLUNK_HOME}/etc/apps/SA-VMWIndex/local/app.conf(create app.conf file in local directory if it is not present) - Edit the "state" property of the "install" stanza as shown below:
- Restart the all the Search Heads present in your deployment.
[install] state = disabled
$SPLUNK_HOME/bin/splunk restart
After you migrate
Perform the steps below on each search head in your deployment:
- Move the following directories from the App package to the
DA-ITSI-CP-vmware-dashboardsfolder that you backed up while going through the procedure in the "Before you migrate" section: - /local directory from
splunk_for_vmwarethat contains all the local configurations under conf files - /lookups directory from
splunk_for_vmwarethat contains the CSV lookups - Move the
datamodels.confconfiguration file from the local folder of the SA-VMW-HierarchyInventory package to the
DA-ITSI-CP-vmware-dashboards/local/package. - Move the following lookups files from the SA-VMW-HierarchyInventory package to
DA-ITSI-CP-vmware-dashboards/lookups/package: - DatastoreList.csv
- FullHierarchy.csv
- TimeAboutHost.csv
- TimeClusterServicesAvailability.csv
- TimeDatastoreSummary.csv
- TimeDatastoreSummary.csv
- TimeInvHostHardwareAndLicense.csv
- UniqueNameLookup.csv
- Move the following lookups files from the SA-VMW-Performance package to the
DA-ITSI-CP-vmware-dashboards/lookups/package - ACFields.csv
- HSFieldList.csv
- HSInstanceList.csv
- Move the following lookups files from the SA-VMW-LogEventTask package to the
DA-ITSI-CP-vmware-dashboards/lookups/package. - vmware_event_lookup.csv
- vmware_task_lookup.csv
- Remove the app.conf file from the
DA-ITSI-CP-vmware-dashboards/localdirectory. - Restart the instance.
$SPLUNK_HOME/bin/splunk restart
Install and configure the content pack
- Make sure the VMware data collected using Splunk Add-on for VMware Metrics (v4.2.0 or higher) is searchable from the search head where you installed the Splunk App for Content Packs.
- Install and configure the Content Pack for VMware Dashboards and Reports.
- Configure data collection for the Content Pack for VMware Dashboards and Reports.
Access the dashboards in the content pack
You can now access the dashboards from the content pack:
- In Splunk Web, open IT Service Intelligence or IT Essentials Work.
- From the main navigation bar choose Dashboards > Dashboards.
- From the list of dashboards, those with the suffix - VMware are from the Content Pack for VMware Dashboards and Reports. Select the dashboard title to open the dashboard.
- Remove the
{SPLUNK_HOME}/etc/apps/splunk_for_vmware , {SPLUNK_HOME}/etc/apps/SA-VMW-Performance, {SPLUNK_HOME}/etc/apps/SA-Threshold, {SPLUNK_HOME}/etc/apps/SA-VMW-LogEventTask, {SPLUNK_HOME}/etc/apps/SA-VMNetAppUtils, {SPLUNK_HOME}/etc/apps/SA-VMW-HierarchyInventory, {SPLUNK_HOME}/etc/apps/TA-VMW-FieldExtractions, {SPLUNK_HOME}/etc/apps/Splunk_TA_vmware, and{SPLUNK_HOME}/etc/apps/SA-Hydradirectories to use the Content Pack for VMware Dashboards and Reports.
| Configure data collection for the Content Pack for VMware Dashboards and Reports | Use the Content Pack for VMware Dashboards and Reports |
This documentation applies to the following versions of Content Pack for VMware Dashboards and Reports: 1.3.0, 1.3.1
 Download manual
Download manual
Feedback submitted, thanks!