Predictive Analytics dashboard
Use the Predictive Analytics dashboard to search for different varieties of anomalous events in your data. Predictive Analytics uses the predictive analysis functionality in Splunk to provide statistical information about the results, and identify outliers in your data.
These field filter options are available:
| Filter | Description |
|---|---|
| Data Model | Specifies the data model (from a drop-down list) for the search. Available data models are shown in the drop-down list. Choose a data model on which to base your search. |
| Object | Specifies the object within the data model for the search. Objects are searches that are available in the selected data model. |
| Function | Specifies the function within the object for the search Functions specify the type of analysis to perform on the search results. For example, choose " |
| Attribute | Specifies the constraint attributes within the object for the search Attributes are constraints on the search results. For example, choose " |
| Time range | Specify the time range for the search |
Choose a data model, object, function, attribute, and time range to analyze and click Search.
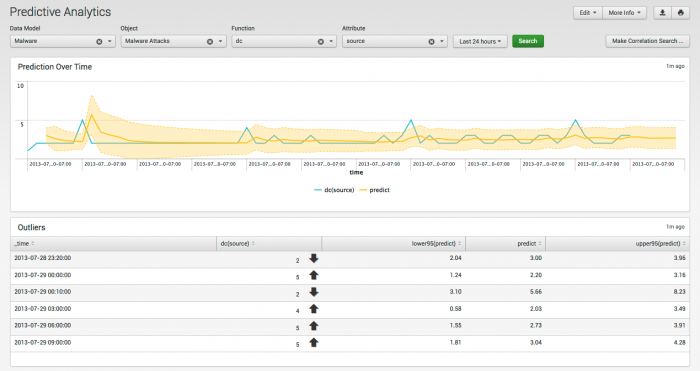
Prediction Over Time
The Prediction Over Time panel shows a predictive analysis of the results over time, based on the time range you chose. The shaded area shows results that fall within two standard deviations of the mean value of the total search results.
Outliers
The Outliers panel shows those results that fall outside of two standard deviations of the search results.
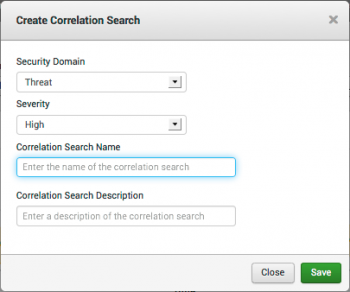
Create a correlation search
From this dashboard, create a correlation search based on the search parameters for your current predictive analytics search. This correlation search will create an alert when the correlation search returns an event.
Click Make Correlation Search... to open the Create Correlation Search dialog.
Select the Security domain and Severity for the notable event created by this search. Add a search name and search description. Click Save.
To view and edit correlation searches, go to Configure > Correlation Searches. See "Modify correlation searches" in the Splunk App for Enterprise Security Installation and Configuration Manual for more information.
Configuration information
For information on configuring the Predictive Analytics dashboard, see "Predictive Analytics dashboard" in the Splunk App for Enterprise Security Installation and Configuration Manual.
| Incident Review dashboard | Entity Investigator dashboards |
This documentation applies to the following versions of Splunk® Enterprise Security: 3.0, 3.0.1
 Download manual
Download manual
Feedback submitted, thanks!