Notable Event Suppressions
A notable event suppression is a search filter that hides any notable events matching the search conditions. The suppression filter is created to stop an excessive or unwanted number of notable events from being displayed on the Incident Review dashboard.
For example, you may want to prevent certain types of notable events from appearing on the Incident Review dashboard or contributing to defined alert thresholds.
- Suppression is applied to events that are already in the notable index. A suppression filter hides notable events so they will not be seen.
- Throttling is applied to events before they are added to the notable index. Throttling prevents notable events from being created.
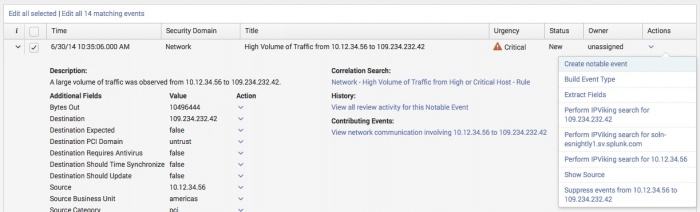
Create a suppression from Incident Review
- Find the notable event that you want to suppress in the Incident Review dashboard.
- From the Actions select: Suppress events to/from... which opens the New Notable Event Suppression page.
- Review the contents of the fields. An Expiration Time field is available to define a time limit for the suppression filter. After the time limit is met, the suppression filter is disabled. Save the changes.
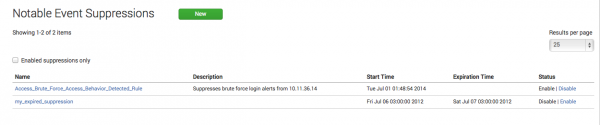
To review the suppression filter, browse to Configure > Incident Management > Notable Event Suppressions.
Creating a suppresion for events in the Incident Review dashboard will not suppress notable events in the Security Posture dashboard. Event suppression only suppresses events from Incident Review, as there is no need for an analyst to review them. They still represent load on the system and will continue to be represented in Security Posture, Audit, and other screens
Create a suppression from Notable Event Suppressions
- Browse to Configure > Incident Management > Notable Event Suppressions.
- Click on New to create a new notable event suppression.
- Set the Name and Description used for the suppression filter.
- Populate the Search field with the search that finds the events to suppress.
- Set the Expiration Time: Defines a time limit for the suppression filter. If the time limit is met, the suppression filter is disabled.
Edit notable event suppressions
- Browse to Configure > Incident Management > Notable Event Suppressions.
- Selecting a notable event suppression opens the Edit Notable Event Suppression page.
- Edit the Description and Search fields used for the suppression filter.
Disable notable event suppressions
- Browse to Configure > Incident Management > Notable Event Suppressions.
- Select Disable in the Status column for the notable event suppression.
Remove a notable event suppression
- Browse to Settings > Event types.
- Search for the the suppression event:
notable_suppression-<suppression_name>. - Select delete in the Actions column for the notable event suppression.
Suppression activity audit
The Enterprise Security app tracks all suppression activity for auditing on the Suppression Audit dashboard.
| Manual notable event creation | Predictive Analytics dashboard |
This documentation applies to the following versions of Splunk® Enterprise Security: 3.1, 3.1.1, 3.2, 3.2.1, 3.2.2, 3.3.0, 3.3.1, 3.3.2, 3.3.3
 Download manual
Download manual
Feedback submitted, thanks!