Customize notable event settings in Splunk Enterprise Security
As a Splunk Enterprise Security administrator, you can make configuration changes to notable events.
- Change notable event fields.
- Manage notable event statuses.
- Create and manage notable event suppressions.
Change notable event fields
Make changes to the fields displayed on the Incident Review dashboard for notable events on the Incident Review Settings dashboard. For example, change the label of a field in the notable event details, remove a field, or add a new field to the Additional Fields section of the notable event details. Changes that you make to notable event fields affect all notable events.
- From the menu bar, select Configure > Incident Management > Incident Review Settings.
- Review the Incident Review - Event Attributes.
- Click Edit to change a field or the label for a specific field that appears on Incident Review.
- Click Remove to remove a field from the notable event details on the Incident Review dashboard.
- Click Save to save your changes.
Add a field to the notable event details
A field appears in the Additional fields of the notable event details if the field exists in the correlation search results and Incident Review can display the field. To add a field to the notable event details, first make sure that the correlation search results include the field and then make sure that Incident Review can display the field.
- Determine if the field you want to see is included in the correlation search results. Run the correlation search on the Search page to review the output or review the search syntax.
- If the field exists in the search results, go to step four.
- If the field does not exist in the search results, go to step two.
- Modify the correlation search to include the field.
- If you can edit the search with the guided search editor, add the field as an aggregate function with an alias. Use the values function to return all possible values of a given field, or the latest function to return the most recent value for the field.
- If you created the search manually, modify the search to extract the fields. Make sure that you do not modify the correlation criteria when you modify the search.
- If the search does not include statistical transformations, add
| fields + newfieldnameto the end of the search, wherenewfieldnameis the name of the new field you want to see in the additional details. - If the search does include statistical transformations, extract the fields when you perform the statistical transformation. For example, if your search includes a stats search
| stats count by src | where count>5, thesrcandcountfields appear in the notable event details. To add thedestfield to the notable event details, you might change the search to the following:| stats values(dest) as dest,count by src.
- If the search does not include statistical transformations, add
- Verify changes to correlation searches on the Search page before saving them.
- Add the field to the list of additional fields.
- From the menu bar, select Configure > Incident Management > Incident Review Settings.
- Click Add new entry to add the new field to the Additional Fields section of the notable event details.
- Type a Label to use as the display name of the field in the notable event details.
- Type a Field to match the field that you want to appear in the notable event details.
- Click Done.
- Click Save.
Manage notable event statuses
An analyst assigns a status to a notable event to communicate the state of the notable event in the investigation workflow. The status aligns with the stages of an investigation, and can be used to review and report on the progress of a notable event investigation on the Incident Review Audit dashboard.
To see the available statuses for notable events, select Configure > Incident Management > Notable Event Statuses
| Label | Description | Can be edited |
|---|---|---|
| Unassigned | Used by Enterprise Security when an error prevents the notable event from having a valid status assignment. | No |
| New (default) | A notable event has not been reviewed. | No |
| In Progress | An investigation or response to the notable event is in progress. | Yes |
| Pending | A notable event closure is pending some action. | Yes |
| Resolved | A notable event has been resolved and awaits verification. | Yes |
| Closed | A notable event has been resolved and verified. | Yes |
Every notable event is assigned a status of New by default when it is created by a correlation search. You can customize notable event statuses to match an existing workflow at your organization.
Edit notable event statuses
Change the available statuses for notable events on the Edit Notable Event Status page.
- On the Splunk Enterprise Security toolbar, select Configure > Incident Management > Notable Event Statuses.
- Select a notable event status to open the Edit Notable Event Status page.
- Change the Label or Description as desired.
You cannot edit the Unassigned and New statuses because they are defaults used when creating notable events.
Manage notable event status history
Notable events are associated with users, statuses, and comments. Changes made to status names affect only the name of a status, not the status ID assigned to the notable event in the notable index.
If you change the name of a default notable event status, the name will change for both past and future notable events. For example, if you rename pending to waiting for customer, all notable events with a status of pending will then have a status of waiting for customer. The status ID assigned to the notable events will remain the same.
Notable event status transitions
The status names represent the steps required in investigating a notable event. Status transitions define the path of a notable event investigation.
An analyst assigned a notable event will change the status of the notable event as the investigation progresses. To change the current status on a notable event:
- The analyst must be a member of a role that has permission to change a status. Notable event status transitions are available to the ess_analyst and ess_admin roles by default.
- The follow-on status must allow a transition from the current status. Every status can transition to any other status by default. For example, a notable event in a New status can transition directly to any other status including Closed.
Restrict status transitions
You can define a transition workflow and limit which status can transition to another status, creating a predefined path for the notable event investigation workflow. By default, no transition path is defined or required and every status can transition to every other status.
Prerequisites
- In order to edit status transitions, you must have the ess_analyst role or your role must be assigned the Edit Notable Event Statuses capability. For more information about user roles and capabilities, see Configure user and roles in the Installation and Upgrade Manual.
- Define the status workflow for notable event investigations. Determine which statuses to require, and whether analysts should follow a specific sequence of statuses before completing the investigation workflow. Determine whether any roles can bypass the full workflow.
Restrict notable event status transitions
- On the Splunk Enterprise Security toolbar, select Configure > Incident Management > Notable Event Statuses.
- Select a notable event status to open the Edit Notable Event Status page.
- In Status Transitions, modify the To Status fields.
- To define which roles are allowed to transition a notable event to the selected status, choose the Authorization field and add or remove roles.
- To remove a transition an event to the selected status, choose Unselect All.
- Save the changes.
- Test the changes to the status workflow. If any transitions required adding or removing roles, test with credentials assigned to each role.
Add a new status
Add a new status to the notable event investigation workflow. If you restrict status transitions, determine where this status fits in the workflow.
- Define the status workflow for notable events.
- Determine where the new status is needed in the workflow.
- Determine whether any roles (e.g. ess_admin) will be allowed to bypass the new status in the workflow.
- On the Splunk Enterprise Security toolbar, open Configure > Incident Management and select Notable Event Statuses.
- Select New.
- Add a label. This is the Status field value used on the Incident Review dashboard and for notable event status reporting. Example: Waiting on ITOps
- Add a description. The description is only referenced in the Notable Event Status page. Example: Waiting on another department.
- (Optional) Select Default status. Choose only if you are replacing the New status for notable events
- (Optional) Select End status. Choose when adding an additional Closed status for notable events.
- Define the Status Transitions by modifying the To Status fields.
- Review the status workflow and determine which statuses a notable event can transition to.
- Choose the Authorization field and add the roles allowed to transition a notable event to the selected status.
- Save the changes.
Example: In our workflow, the "Waiting on ITOps" status occurs after "New" and "In Progress", but before "Pending." It is not a required status and can be skipped over to choose "Pending." Edit the Status Transitions in "Waiting on ITOps" for "Pending," "Resolved," and "Closed" and add the roles ess_admin and ess_analyst added under Authorization. - Edit the statuses that will precede the new status in the workflow, and add the roles allowed to perform the transition.
Example: In our workflow, a notable event can be given a status of "Waiting on ITOps" from a status of "New" and "In Progress." Edit the Status Transitions in both "New" and "In Progress" adding the ess_admin and ess_analyst roles under Authorization for "Waiting on ITOps". - Test to ensure the status can be assigned and that any status transitions involving it work.
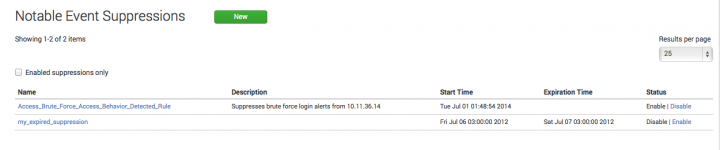
Create and manage notable event suppressions
You can hide notable events from the Incident Review dashboard by creating a notable event suppression.
A suppression is a search filter that hides additional notable events from view, and is used to stop excessive or unwanted numbers of notable events from appearing on the Incident Review dashboard. Notable events that meet the search conditions are still created and added to the notable index. Suppressed notable events continue to contribute to notable event counts on the Security Posture and auditing dashboards.
To prevent notable events that meet certain conditions from being created, see Throttle the number of response actions generated by a correlation search.
You can create a suppression filter in two ways.
- Create a suppression from Incident Review. See Suppress a notable event.
- Create a suppression from the Configure menu. See Create a suppression from Notable Event Suppressions.
Create a suppression from Notable Event Suppressions
- Select Configure > Incident Management > Notable Event Suppressions.
- Click Create New Suppression.
- Enter a Name and Description for the suppression filter.
- Enter a Search to use to find notable events to be suppressed.
- Set the Expiration Time. This defines a time limit for the suppression filter. If the time limit is met, the suppression filter is disabled.
Edit notable event suppressions
- Select Configure > Incident Management > Notable Event Suppressions.
- Select a notable event suppression to open the Edit Notable Event Suppression page.
- Edit the Description and Search fields used for the suppression filter.
Disable notable event suppressions
- Select Configure > Incident Management > Notable Event Suppressions.
- Select Disable in the Status column for the notable event suppression.
Remove a notable event suppression
- From the Splunk platform toolbar, select Settings > Event types.
- Search for the the suppression event:
notable_suppression-<suppression_name>. - Select delete in the Actions column for the notable event suppression.
Audit notable event suppressions
Audit notable event suppressions with the Suppression Audit dashboard.
| Manually create a notable event in Splunk Enterprise Security | Manage investigations in Splunk Enterprise Security |
This documentation applies to the following versions of Splunk® Enterprise Security: 4.7.0, 4.7.1, 4.7.2, 4.7.3, 4.7.4, 4.7.5, 4.7.6
 Download manual
Download manual
Feedback submitted, thanks!