 Download topic as PDF
Download topic as PDF
Use Splunk App for Fraud Analytics to detect fraud
Fraud detection is used by many industries such as banking and insurance to prevent financial and asset loss through activities such as migration to new information systems or a cybersecurity breach, and so on. The Splunk App for Fraud Analytics covers the following two use cases:
- New account fraud: Also known as Account Opening Fraud or Online Account Origination Fraud. Any organization that acquires new customers benefits from identifying new accounts created by bogus users. For example: In banking, fraudsters use stolen or synthetic identities to open new accounts, intending to maximize their credit limits before disappearing, usually within 90 days.
- Account takeover: Organizations are prone to attacks by hackers and cyber criminals, who illegally gain access and take ownership of online accounts using false identities, stolen passwords, and usernames, typically gained from social media, data breaches, bots, and phishing attacks.
The Splunk App for Fraud Analytics includes correlation searches that can identify fraud based on specific types of data elements. Ingesting data that corresponds to specific data models populates the dashboards and correlation searches in the app.
For example: The correlation searches that identify new account fraud use the following data:
- Phone number
- Password (Includes hash, nonce, token, or password)
- IP address
- Zip code
- Bank account (Includes destination and deposit)
- Email address
- Username
The correlation searches that identify account takeover use the following data:
- Username
- IP address
- Login status (Includes success or failure)
- Browser language
- Action (Includes actions such as editing password, editing profiles, log in, log out, and so on)
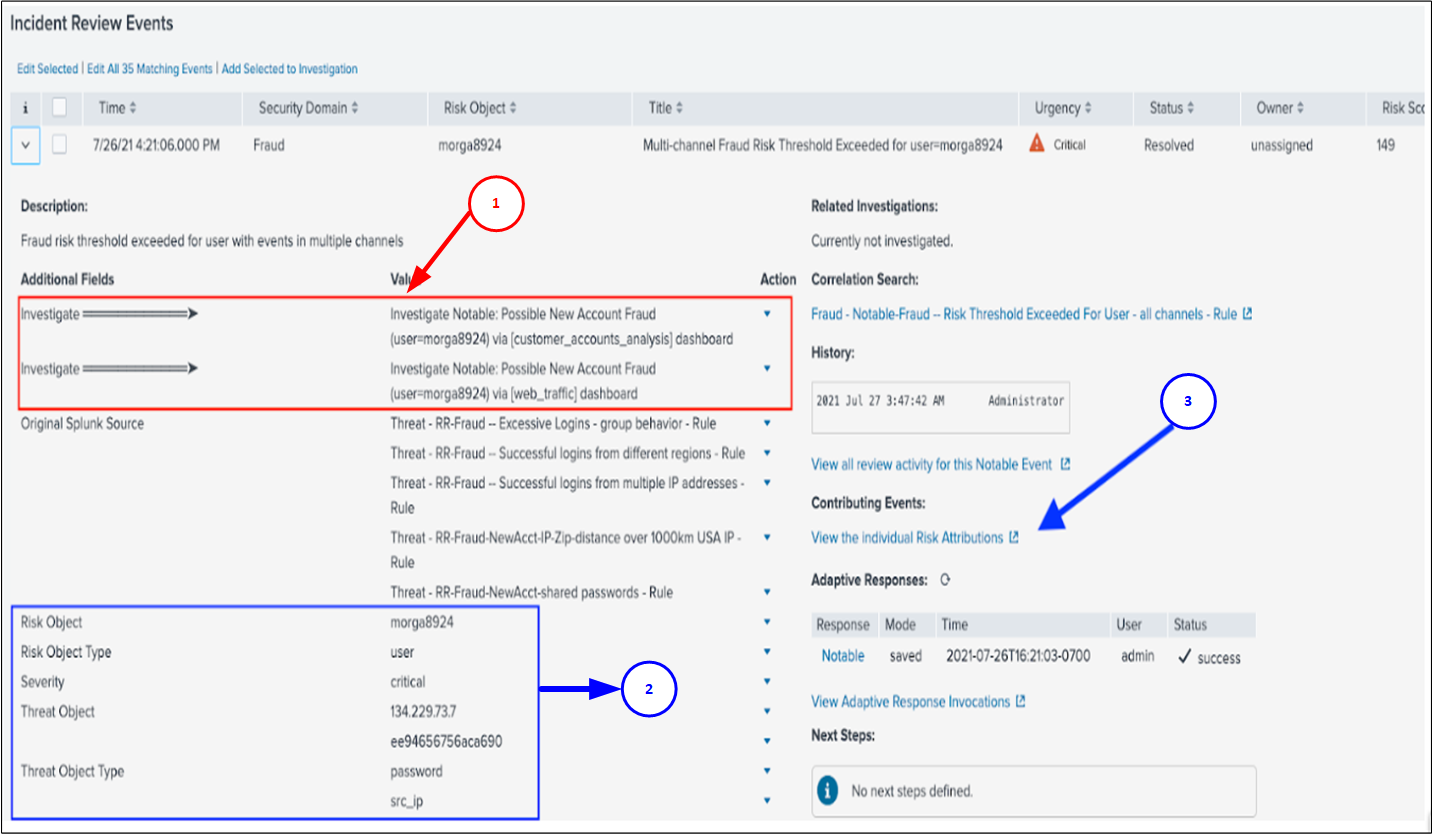
The following figure indicates how to access the Fraud Analytics dashboards by drilling down from the fraud notables on the Incident Review panel in Splunk Enterprise Security:
The Splunk App for Fraud Analytics has some additional fields and features on the Incident Review page. In this example, clicking the Action menu and selecting Click Here to Investigate reverts you to the customer_account_analytics dashboard and the web_traffic dashboards for further investigation of the notable.
| Annotation Number | Description |
|---|---|
| 1 | Links to different investigative dashboards
Risk based correlation searches might be based on different datasets, which requires different investigative dashboards for some functions. |
| 2 | Risk and threat objects in the Risk Analysis adaptive response action |
| 3 | Link to the risk based correlation searches and scores that create notables |
|
PREVIOUS Overview of the Splunk App for Fraud Analytics |
NEXT Install Splunk App for Fraud Analytics |
This documentation applies to the following versions of Splunk® App for Fraud Analytics: 1.1.3, 1.2.4
Feedback submitted, thanks!