About the Splunk Cloud Gateway security process
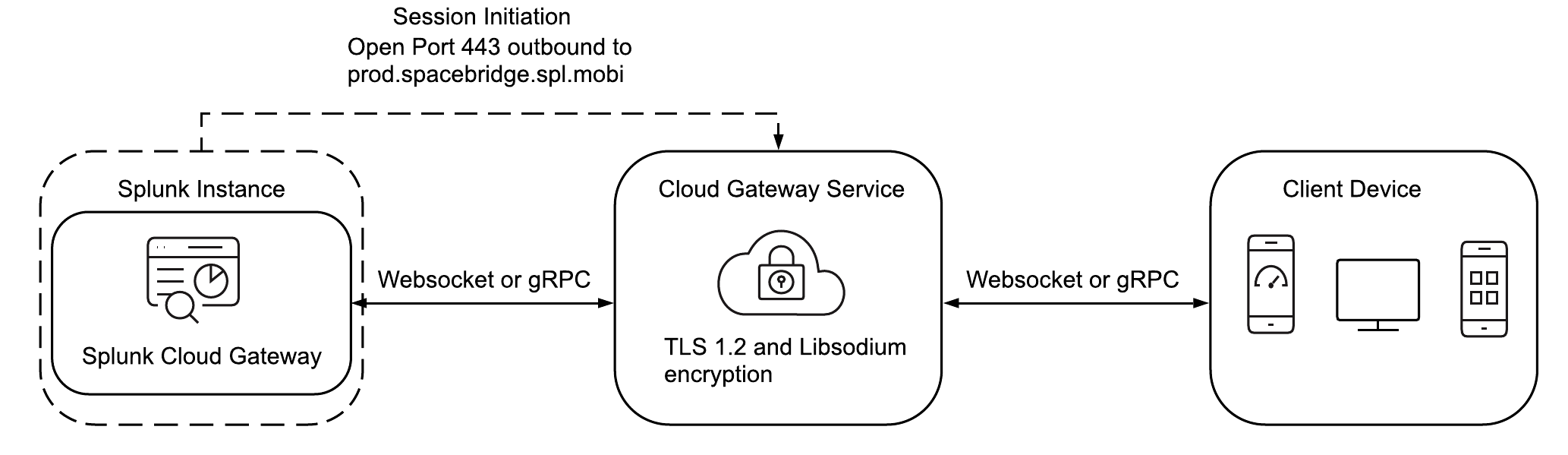
You can view and interact with data on your mobile device or Apple TV using the Splunk Connected Experiences apps and the Splunk Cloud Gateway app. The Connected Experiences apps connect to Splunk Cloud Gateway, a required Splunk Platform app that facilitates encrypted message exchanges between mobile devices and a Splunk platform instance. Sophisticated encryption and a secure data exchange process remove the need for ingress firewall rules, port mappings, domain registrations, and device login details.
The Splunk Cloud Gateway app connects devices to a Splunk Enterprise or Splunk Cloud instance. The app routes encrypted data through the Cloud Gateway service, an intermediary component that's hosted on the Splunk common cloud infrastructure. The Cloud Gateway service identifies client devices and establishes an encrypted transfer during transit and at rest.
Encryption
The Cloud Gateway service uses Libsodium to encrypt data end-to-end at multiple layers of the process. Libsodium, a high-level cryptographic tool, features Integrated Encryption Scheme (IES). IES is a hybrid encryption scheme that provides semantic security functionality. Transport Layer Security (TLS) 1.2, which uses secure hash algorithms and advanced cipher suites, provides transport-level encryption. Libsodium encryption and TLS 1.2 protocol provide data protection both at rest and in transit.
Unique private and public key pair generation
For client devices and Splunk platform instances to communicate through the Cloud Gateway service, both sides require a public and private key pair. Both the client and Splunk Cloud Gateway app generate a unique private and public key pair with a 256-bit ECC key strength.
The client device key pair is generated when you load a Connected Experiences app on your device. If you unregister a device, a new client device key pair is generated.
The Splunk Cloud Gateway app key pair is generated when you install the Splunk Cloud Gateway app. Once the Splunk Cloud Gateway keys are generated, websocket or Remote Procedure Call (gRPC) connection opens for data exchange between the client device and the Splunk Cloud Gateway app.
Session initiation and data exchange
The Splunk Cloud Gateway app requires you to open port 443 outbound to the host prod.spacebridge.spl.mobi, which allows the Cloud Gateway service to bidirectionally route the encrypted data between client devices and Splunk platform instances through websocket or gRPC connection. No inbound ports are opened.
Optionally, you can route the outbound connection through a proxy. See Install Splunk Cloud Gateway for more information about how to use a proxy with Splunk Cloud Gateway.
Does Splunk store my data?
Your data is not stored in Splunk servers. Splunk servers store only anonymized routing information. The Cloud Gateway service cannot read any identifying information and does not persist any user data.
For Splunk Natural Language Processing (NLP) requests, Splunk Cloud Gateway stores the fields required to create an intent, such as utterances, attribute types, and result types. NLP sends a saved search ID to your instance and uses the NLP fields to make a natural language request for data. NLP also uses the Libsodium cryptographic tool, which secures your data end to end during transit and at rest.
Device authentication
The client device and Splunk Cloud Gateway app exchange an authentication code, their public keys, and credentials during device registration. All registration details pass through the Cloud Gateway service, which performs encryption using Libsodium and TLS 1.2 protocol.
During registration, the Cloud Gateway service reads the client device public key and the Splunk Cloud Gateway app public key. The public key uniquely identifies the client to the Splunk Cloud Gateway app. The Splunk Cloud Gateway app then sends its public key and a session token that's encrypted with the client public key to the client device.
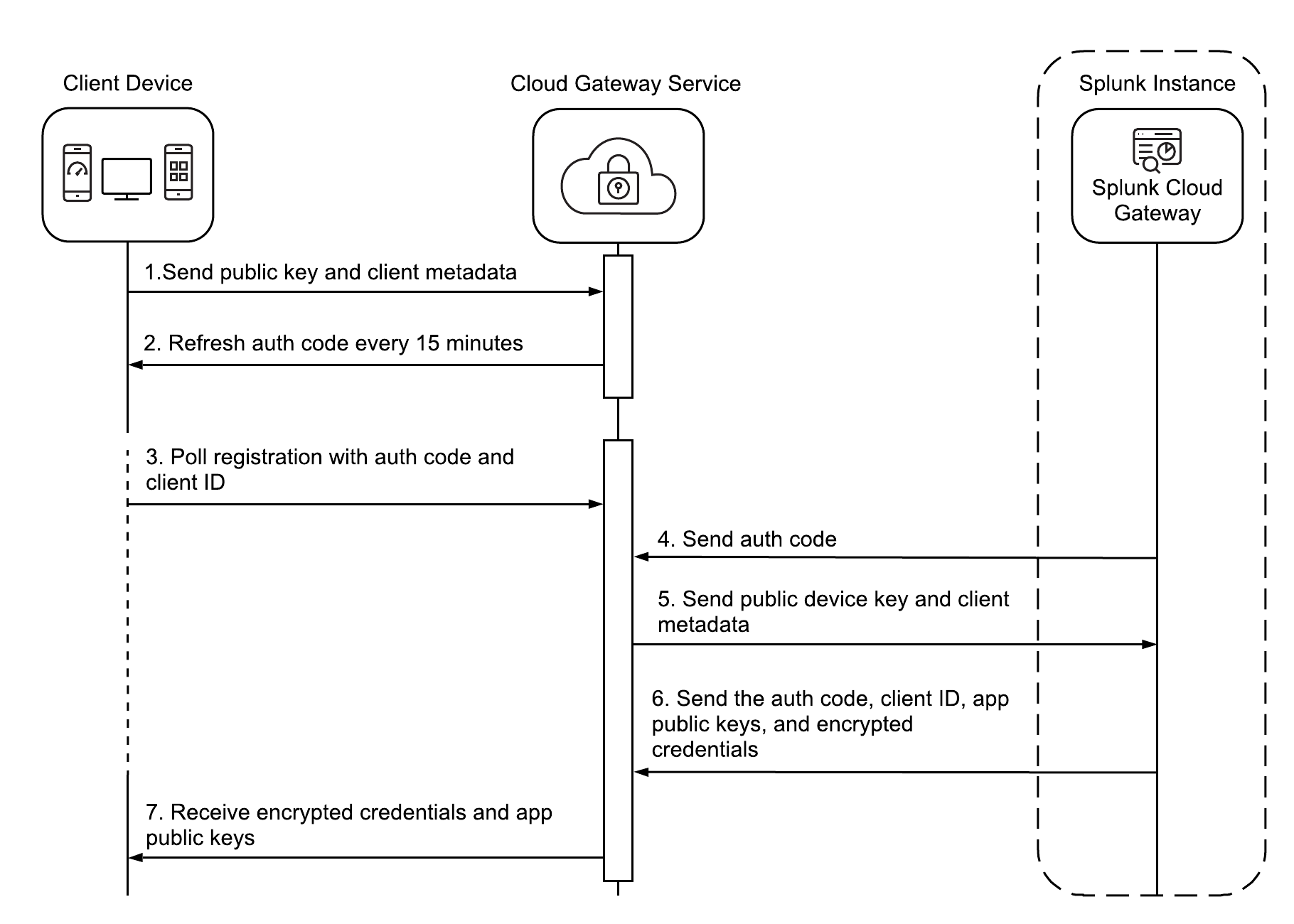
The following diagram illustrates the step-by-step client registration process:
This is the Splunk Cloud Gateway registration process in detail:
- When the user registers their device, the Connected Experiences app provides an authentication code. The user enters the authentication code into the Splunk Cloud Gateway app. The client device sends its public key and client metadata to the Cloud Gateway service.
- The authentication code refreshes every 15 minutes.
- The client polls registration with the authentication code and client ID.
- The Splunk Cloud Gateway app sends the authentication code to the Cloud Gateway service.
- The Cloud Gateway service sends device public key and client metadata to the Splunk Cloud Gateway app.
- The Splunk Cloud Gateway app sends the authentication code, client ID, app public key, and encrypted credentials to the Splunk Cloud Gateway service.
- The client receives the encrypted credentials and app public keys and device registration completes.
Message flow
The Cloud Gateway service facilitates message flow between the client device and the Splunk Cloud Gateway app using a hybrid encryption scheme called Elliptic Curve Integrated Encryption Scheme (ECIES). Routing information is anonymized, so that the sender's and receiver's identities are private. During message exchange, sensitive data is encrypted with the receiver's public key. The client identifies itself to the Cloud Gateway service with a hash of its public key. The entire payload is signed with the sender's private key. The Cloud Gateway service verifies the message's signature and verifies that the sender is allowed to send messages to the receiver.
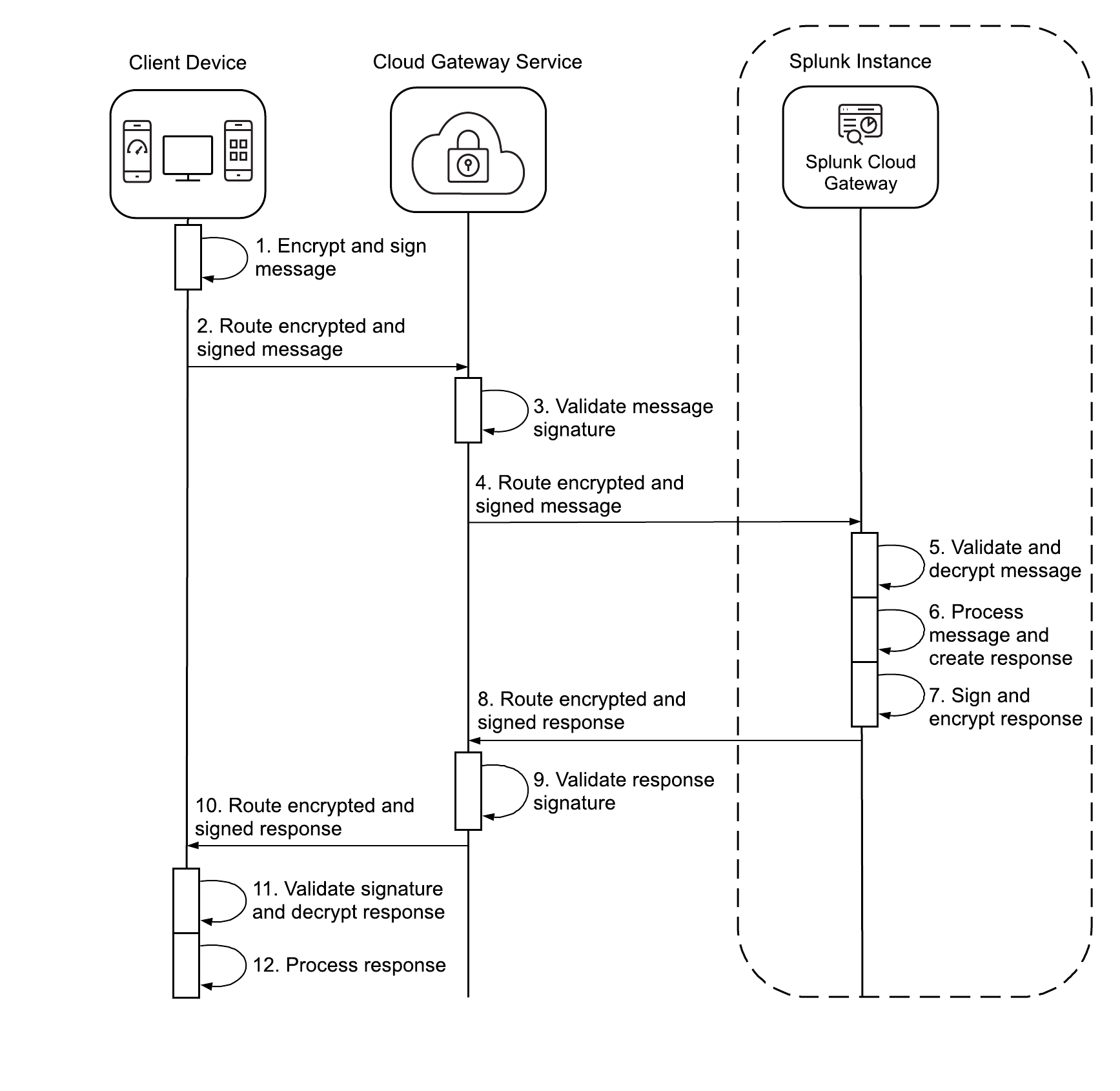
This diagram shows a message request from the client device to the Splunk Cloud Gateway app:
Here are the steps that occur during a message exchange between the client device and the Splunk Cloud Gateway app:
- When the user makes a message request, such as loading a list of dashboards, the client encrypts and signs the message.
- The client routes the encrypted and signed message to the Cloud Gateway service.
- The Cloud Gateway service validates the message signature.
- The Cloud Gateway service routes the encrypted and signed message to the Cloud Gateway app.
- The Cloud Gateway app validates the signature and decrypts the message.
- The Cloud Gateway app processes the message and creates a response.
- The Cloud Gateway app signs and encrypts the response.
- The Cloud Gateway app sends the encrypted and signed response to the Cloud Gateway service.
- The Cloud Gateway service validates the response signature.
- The Cloud Gateway Service routes the encrypted and signed response to the client.
- The client validates the response signature and decrypts the response.
- The client processes the response.
More security features
The Splunk Cloud Gateway app secures your data when connecting your Splunk platform instance to mobile devices in the following additional ways.
Sandbox security
Sandbox security allows you to restrict data to an isolated environment. The Cloud Gateway service sandbox is separate from your Splunk platform instance. You define exactly what data to encrypt and transfer and which devices can receive the data. The rest of your deployment is untouched.
Dynamic and static code analyses
Automated dynamic code analysis monitors system memory, behavior, and overall performance. Static code analysis defines structures and dependencies to enforce security standards at build time.
Periodic threat modeling
Periodic threat modeling identifies potential threats and vulnerabilities, allowing the Splunk Cloud Gateway team to develop strong and secure defenses.
BLAKE2b hash function
Splunk Cloud Gateway uses BLAKE2b, a secure cryptographic hash function to encrypt messages.
| Install Splunk Cloud Gateway | Enable Connected Experiences apps in Splunk Cloud Gateway |
This documentation applies to the following versions of Splunk® Cloud Gateway (Legacy): 1.1.0, 1.2.0, 1.2.2, 1.2.3, 1.3.0, 1.3.1, 1.4.0, 1.5.0, 1.6.0, 1.7.0, 1.7.2, 1.8.0, 1.9.0, 1.9.1
 Download manual
Download manual
Feedback submitted, thanks!