Integrate ITSI with BMC Remedy
Integrate BMC Remedy with IT Service Intelligence (ITSI) so you can create and update incidents in a Remedy system from ITSI, either through episode actions or through automated action rules in aggregation policies. Splunk ITSI ships with a built-in integrations with Remedy incident management system.
Prerequisites
- You must have BMC Remedy version 9.1 or later.
- You must have the
itoa_adminrole to set up Remedy integration with ITSI. - Install and configure the Splunk Add-on for Remedy 2.0 or later. For instructions, see Install the Splunk Add-on for BMC Remedy.
Configure ITSI action rules
Configure aggregation policy action rules to create and update Remedy incidents when certain conditions are met.
- Within ITSI, click Configuration > Notable Event Aggregation Policies.
- Open the aggregation policy you want to integrate with Remedy.
- Go to the Action Rules tab.
- Click Add Rule and configure trigger conditions for when to create a Remedy incident:
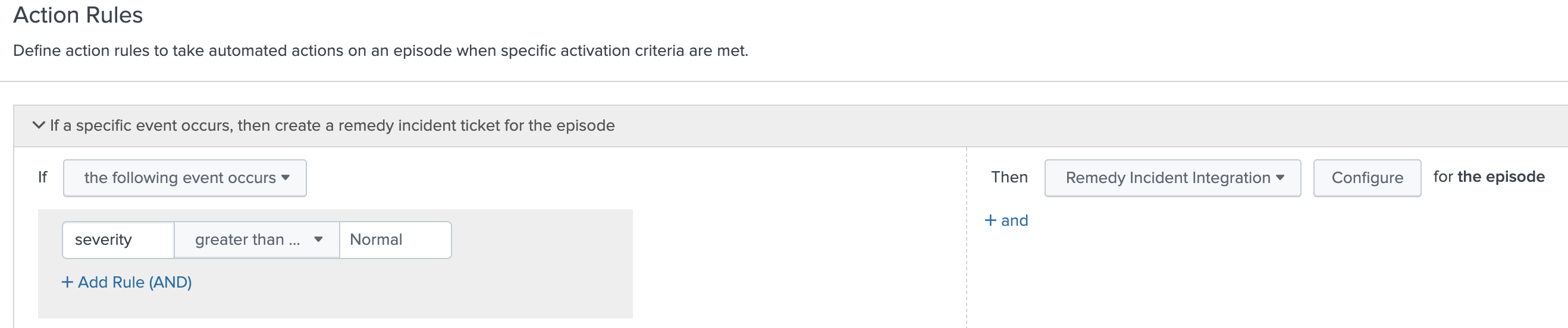
- Click Configure and configure the following fields:
Field Description Correlation ID Don't enter a correlation ID even though this field is marked as required. ITSI takes care of associating the episode with the Remedy ticket for you. Summary A description of the incident. Configuration Item The configuration item to associate with the Remedy incident. Impact The impact of the Remedy incident. Urgency The overall urgency of the Remedy incident. Status Select Resolved if you want to immediately resolve the Remedy incident upon opening it. Status Reason The status reason is for informational use and does not affect how the application behaves. This means that you can assign meanings to the status reasons that are appropriate to your organization's needs. Work Info Keep notes about the work that you perform on the incident or pass information to colleagues also working on the incident. - Optionally, configure additional action rules to update the Remedy incident status when the corresponding ITSI episode changes. For example, create an action rule to change the Remedy incident urgency to Low if the ITSI episode's severity is less than or equal to Normal.
For more information about configuring action rules, see Configure episode action rules in ITSI.
Enable non-admins to test and send alerts
Non-admin roles creating VictorOps incidents through the Episode Review Actions must be assigned certain permissions. To provide non-admin roles the ability to create and test VictorOps incidents, assign them the following capabilities:
- execute-notable_event_action
- write-notable_event
- delete-notable_event
- list_storage_passwords
| Integrate ITSI with ServiceNow | Integrate ITSI with Splunk On-Call (VictorOps) |
This documentation applies to the following versions of Splunk® IT Service Intelligence: 4.11.0, 4.11.1, 4.11.2, 4.11.3, 4.11.4, 4.11.5, 4.11.6, 4.12.0 Cloud only, 4.12.1 Cloud only, 4.12.2 Cloud only, 4.13.0, 4.13.1, 4.13.2, 4.13.3, 4.15.2, 4.15.3
 Download manual
Download manual
Feedback submitted, thanks!