Send a VictorOps alert notification in Splunk App for Infrastructure
Use VictorOps for Splunk (VictorOps) to create and manage alerts in Splunk App for Infrastructure. VictorOps is an incident management software that aligns log management, monitoring, chat tools, and more, for a single-pane of glass into system health. Alerts delivery is automated to get the right alert, to the right person, at the right time.
Prerequisites
- A VictorOps user account, which you can get from your system administrator.
- VictorOps must be installed by your system administrator. VictorOps is available from Splunkbase at VictorOps For Splunk.
- Your system administrator has configured VictorOps for Splunk with Splunk App for Infrastructure. See Configure alert notifications using VictorOps in Splunk App for Infrastructure.
Steps
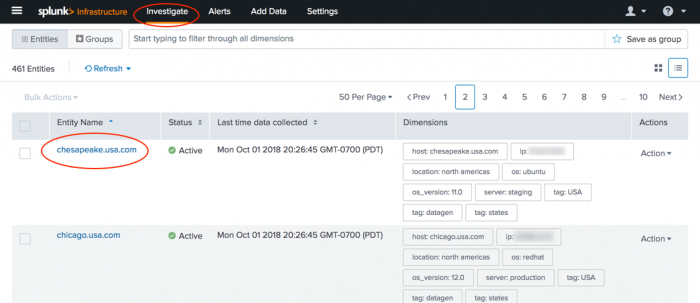
1. In Splunk App for Infrastructure, go to Investigate page.
2. Click an entity you want to investigate.
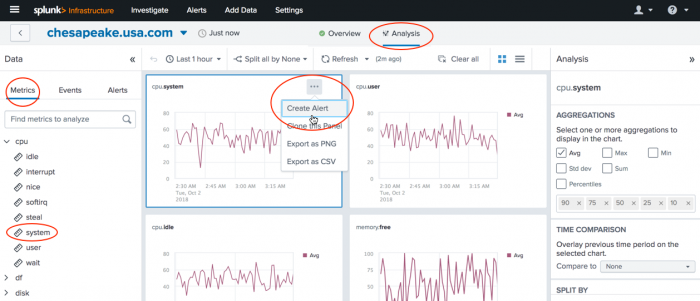
3. Click the Analysis tab.
4. Select a metric for which you want to create an alert.
5. On the chart panel for the selected metric, click the ellipsis (three dots) and click Create Alert.
6. (Optional). If you have selected to create an alert for a group, click Select All By for the metric you want to split (for example, host).
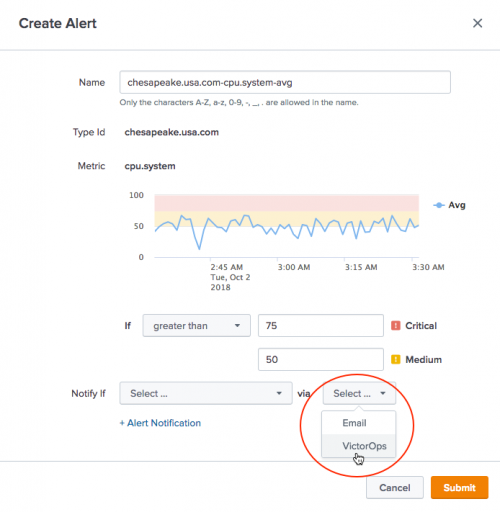
7. In the Create Alert dialog, set alert thresholds. The alert chart in the dialog visually displays the thresholds.
8. In the Notify if field, select the severity and VictorOps.
9. Click Submit. The VictorOps-enabled alert is created.
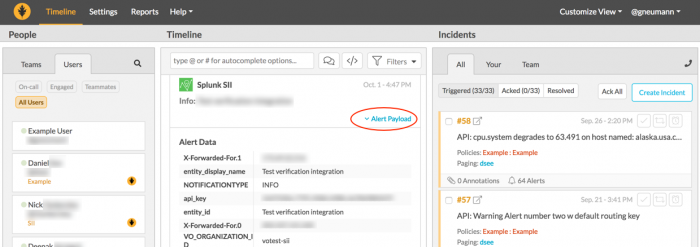
10. When this alert triggers, the results display in your VictorOps account timeline. Click Alert Payload link to view details of the alert.
| Send an email alert notification in Splunk App for Infrastructure | Monitor CPU usage using Splunk App for Infrastructure |
This documentation applies to the following versions of Splunk® App for Infrastructure (EOL): 1.2.0
 Download manual
Download manual
Feedback submitted, thanks!