 Download topic as PDF
Download topic as PDF
Windows Help
This topic discusses each of the pages in the Windows module of the Splunk App for Microsoft Exchange. It describes actions you can perform in each of the panels, as well as what data inputs populate each page.
You can access any of these pages by selecting the appropriate item under the Windows menu.
Overview
The Splunk App for Microsoft Exchange has several sets of pages, each of which displays a different element of Windows data collection. You can access these pages from the "Windows" menu in the app.
- The Event Monitoring page set displays information on Windows event log data that has been collected.
- The Performance Monitoring set of pages displays information about performance monitor statistics that has been collected.
- The Applications and Updates page group displays information on applications that have been installed or have crashed, as well as Windows Update information.
- The Host Monitoring page group displays information on hosts on the Windows network.
- The Network Monitoring page group displays information on network statistics, including network usage by host and process.
- The Print Monitoring page group displays information on printers, print jobs, and print queues for each host.
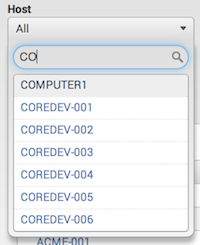
Use the wild card capability in the 'Host' drop down control on nearly all pages
Nearly all of the pages in the Windows module of the Splunk App for Microsoft Exchange have a Host drop-down control box. In all such controls, you can type in text, including wildcards, and the Splunk App for Microsoft Exchange filters the data to include only those events generated by hosts whose names match the text that you enter.
This works particularly well if you use a standard host naming convention in your environment. For example, if all domain controllers in the environment have host names which contain the strong "DC", or all IIS servers' host names contain the string "IIS", you can type in "DC" in any Host control to display data collected from all domain controllers, or "IIS" to display information from all computers in your environment that run Internet Information Server.
This feature is only available for 'Host' drop-down controls.
Windows Overview
The Overview page contains three panels: Windows events, Windows performance counters and All indexed data. The "Windows events" and "Windows performance counters" panels have counters which, when clicked, take you to a Search page that lists all of the events found for that particular counter.
The "Windows events" panel has counters for numbers of hosts, log names, and event IDs. The "Windows performance counters" panel has counters for numbers of hosts, performance objects, and performance counters.
Windows events: Provides information on the number of hosts from which event log data is being collected, the number of event logs and number of event IDs.
Windows performance counters: Provides information on the number of hosts from which performance data is being collected, number of objects and total number of counters.
All indexed data: Provides a chronologically-sorted list of the sources, source types, and hosts that the Splunk App for Microsoft Exchange has collected data on.
You can control how much data this panel displays by clicking the time picker and choosing one of the available range presets or selecting a custom time range.
Event Monitoring
The Event monitoring page contains page panels for many Windows Event Log statistics. They include trend lines which help you isolate areas of peak activity. You can mouse over the trend lines to get individual values, and click the trend lines to open a Search window that shows events collected in the time frame where you clicked.
The panels are:
- Event source names
- Task categories
- Hosts
- Event IDs
- The number of events by host over time
- The number of events by event code over time
- The number of events by log name over time
- The number of events by event type over time
Filter event log data
At the top of the Event Monitoring page, there is a row of drop-down boxes that lets you filter the indexed data via a number of parameters:
- Host
- Event Log Name
- Source Name
- Task Category
- Event Code
- Type
The parameters filter out data based on what you pick in each drop down. For example, if you select a host in the Host drop down, the other drop-downs update to show only data collected for that host. In this way, you can "drill down" to find the event log data for the host, log channel, source name, task category, event code, and type you seek.
Additionally, each drop down box is also a text field. You can click your mouse on any drop down box on the page to enter text into that box. The Splunk App for Windows immediately filters the collected data to show only entries that match what you type into any of the boxes.
Finally, the Additional Search Criteria text entry box allows you to search for a specific word or phrase across all of your indexed event log data.
Requirements
The pages on this page require you to enable one or more Windows event log inputs (Splunk recommends that you enable at least the Application, System, Security, and Setup log channels).
Performance Monitoring
The Performance Monitoring page contains pages for CPU, Memory, Physical Disk, Logical Disk, Network Interface, and System metrics.
You can customize the data that appears in the panels by selecting different counters and instances. You can also drill into specifics on memory, CPU, disk and network traffic by host, process, and user.
The page also provides a list of useful reports at the bottom of the page. These reports can be used as a guide to customize new reports as you see fit.
Filter performance metrics
Each of the drop downs in the pages on the Performance Monitoring page is also a text box. You can click your mouse on any drop down box on the page to enter text into that box. The Splunk App for Windows immediately filters the collected performance metrics to show only entries that match what you type into any of the boxes.
Requirements
The pages on this page require the following inputs to display data:
- CPU Metrics: Requires Performance monitoring input "Processor".
- Memory Metrics: Requires Performance monitoring input "Memory".
- Physical Disk Metrics: Requires Performance monitoring input "PhysicalDisk".
- Logical Disk Metrics: Requires Performance monitoring input "LogicalDisk".
- Network Metrics: Requires Performance monitoring input "Network Interface".
- System Metrics: Requires Performance monitoring input "System".
Applications & Updates
The Applications & Updates menu contains information about application crashes, application installs and Windows Updates.
Application Crashes
This page displays the status of application crashes on all of the machines in your environment. It has panels that show you information about:
- Which applications are crashing.
- Which hosts these crashes occur on.
- The number of crashes over time, by host.
- The number of crashes over time, by application.
- The details of each crash, by host.
It also provides a list of useful searches that can be used as a guide to customize the page as you see fit.
This page requires you to enable one or more Windows event log inputs to function correctly. We recommend you enable at least the Application log channel.
Application installs
This page displays the status of application installs on all of the machines in your environment. It has panels that show you information about:
- The total number of installs, by host (A list with trend lines.)
- The total number of installs, by application (A list with trend lines.)
- The number of installs over time, by application (A line chart.)
- The details of an installation, by host.
It also provides a list of useful searches that can be used as a guide to customize the page as you see fit.
This page requires you to enable the Windows event log inputs to function correctly. We recommend you enable at least the Application log channel.
Windows updates
This page displays the status of Windows updates on all of the machines in your environment. It has panels that show you information on:
- The number of failed Windows updates, by host.
- The number of failed Windows updates, by Knowledge Base (KB) number.
- The number of failed Windows updates over time, by host.
- The number of failed Windows updates over time, by KB number.
- The number of successfu Windows updates, by host.
- The number of successful Windows updates, by Knowledge Base (KB) number.
- The number of successful Windows updates over time, by host.
- The number of successful Windows updates over time, by KB number.
It also displays a list of useful searches at the bottom of the page that can be used as a guide to customize the page as you see fit.
This page requires you to enable the Windowsupdate.log file monitoring input to function correctly.
Host Monitoring
Overview
The "Host Monitoring Overview" page lists every host that the Splunk App for Microsoft Exchange has collected data on.
You can filter the host list by entering text into the Host field or selecting entries from the "OS Version", "Domain", or "Architecture" drop-down lists.
To find out more information about a host, click on its name in the list. The Splunk App for Microsoft Exchange takes you to the Host Information page for the selected host.
Host Information
Operations
The "Host Monitoring Operations" page provides operations information about a specific host, and displays pie charts for:
- The peak CPU utilization above 50% over the last 24 hours.
- The peak memory utilization above 50% over the last 24 hours.
- The free disk space distribution.
You can filter this page to show a single host by selecting it from the "Host" drop-down list in the upper right side of the page.
If you click on any of the pie chart slices, the Splunk App for Microsoft Exchange loads the Host Monitoring Overview page filtered to the selected host.
Disk Information
The "Disk Information" page displays information on disk subsystems for each host. The page has a single panel, which lists hostname, drive name, drive type, total disk space, free disk space, and percentage of free space.
You can filter the host list by selecting entries from the "Host", "File System", "Type", "Free Space %", or "Total Space (GB)" drop-down lists.
Process Information
The "Process Information" page displays information on processes that run on each host. The page has a single panel, which lists hostname, process name, start time, and any command-line arguments that might have been passed to the process.
You can filter the host list by selecting entries from the "Host" or "Name" drop-down lists. In this case, "Name" refers to the name of the process or processes you want to filter by.
Service Information
The "Service Information" page displays information on the services that run on each host. The page has a single panel, which lists hostname, service name, start mode, and current service state.
You can filter the host list by selecting entries from the "Host", "StartMode", or "State" drop-down lists, or entering text into the "Name" text box. In this case, "Name" refers to the name of the service or services you want to filter by.
Network Monitoring
Operations
This page displays network activity information for a certain host. The page has bar charts which show:
- The top hosts with inbound connections to the selected host.
- The top hosts with outbound connections from the selected host.
- The top processes with inbound connections to the selected host.
- The top processes with outbound connections from the selected host.
To filter results to a specific host, select that host from the "Local Host" drop-down list box. You can also control the amount of time that the bar charts reference by selecting the time range you desire in the time range picker on the upper left side of the page.
Network monitoring browser
The "Network monitoring browser" page allows you to monitor many aspects of your Windows network. The page has a single panel, which lists:
- Host name.
- Network communication direction.
- Packet type.
- Protocol version.
- Remote host name.
- Local and remote ports the transaction used.
- The process that spawned the network activity.
- The user that started the process.
You can filter the host list by selecting entries from the following drop-down list boxes:
- "Local Host"
- "Direction"
- "Protocol"
- "Packet type"
- "Remote host"
- "Remote port"
- "Local port"
- "Process name"
- "User name"
Print Monitoring
Overview
The "Print Monitoring Overview" page lists information on every host that has a printer on the network. It has a single panel that lists:
- Host name
- Printer
- Printer status
- Last print-related operation.
- Printer driver.
- Print processor.
- Print job priority.
- The printer port that was used.
You can filter the host list by selecting entries from the "Host", "Printer", or "Operation" drop-down lists.
|
PREVIOUS Non-owner Mailbox Access |
NEXT Active Directory Reports |
This documentation applies to the following versions of Splunk® App for Microsoft Exchange (EOL): 3.0
Feedback submitted, thanks!