Configure Incident Workflow
Notable event statuses are used to manage the workflow of notable events in the Splunk App for PCI Compliance. Most users do not need to change these settings from the default. The workflow status of a notable event enables you to manage PCI compliance workflow and events.
The default incident workflow is for a new event to be changed from Unassigned to Assigned and the status changed from New to In Progress. From there, the PCI compliance analyst can troubleshoot the issue. If there is some action that needs to be taken, the status might be changed to Pending, or it might go straight to Resolved. To move from Resolved to Closed the event must then be verified by another party (admin).
Change notable event settings
Navigate to Configure > Incident Management in to make various configuration changes to notable events.
- Review the default notable event statuses and add, remove or change a status as desired. See Managing and monitoring notable event statuses in this topic.
- Review existing or create new Notable event suppressions.
- Customize Incident Review to allow an urgency override or enforce comment usage.
Managing and monitoring notable event statuses
An analyst assigns a status to a notable event to communicate the state of the notable event in the investigation workflow. The status aligns with the stages of an investigation, and can be used to review and report on the progress of a notable event investigation on the Incident Review Audit dashboard.
To see the available statuses for notable events, select Configure > Incident Management > Status Configuration and select the Notable tab.
| Label | Description | Can be edited |
|---|---|---|
| Unassigned | A notable event has not been assigned. | No |
| New (default) | A notable event has not been reviewed. | No |
| In Progress | An investigation or response to the notable event is in progress. | Yes |
| Pending | A notable event closure is pending some action. | Yes |
| Resolved | A notable event has been resolved and awaits verification. | Yes |
| Closed | A notable event has been resolved and verified. | Yes |
Every notable event is assigned a status of New by default when it is created by a correlation search. You can customize notable event statuses to match an existing workflow at your organization.
Edit notable event statuses
Change the available statuses for notable events.
- On the toolbar, select Configure > Incident Management > Status Configuration.
- Select a notable event status on the Notable tab.
- Change the Label or Description as desired.
You cannot edit the '''Unassigned''' and '''New''' statuses because they are defaults used when creating notable events.
Manage notable event status history
Notable events are associated with users, statuses, and comments. Changes made to status names affect only the name of a status, not the status ID assigned to the notable event in the notable index.
If you change the name of a default notable event status, the name will change for both past and future notable events. For example, if you rename pending to waiting for customer, all notable events with a status of pending will then have a status of waiting for customer. The status ID assigned to the notable events will remain the same.
Notable event status transitions
The status names represent the steps required in investigating a notable event. Status transitions define the path of a notable event investigation.
An analyst assigned a notable event will change the status of the notable event as the investigation progresses. To change the current status on a notable event:
- The analyst must be a member of a role that has permission to change a status. Notable event status transitions are available to the pci_analyst and pci_admin roles by default.
- The follow-on status must allow a transition from the current status. Every status can transition to any other status by default. For example, a notable event in a New status can transition directly to any other status including Closed.
Restricting status transitions
You can define a transition workflow and limit which status can transition to another status, creating a predefined path for the notable event investigation workflow. By default, no transition path is defined or required and every status can transition to every other status.
Prerequisites
- In order to edit status transitions, you must have the pci_analyst role or your role must be assigned the Edit Statuses permission. For more information about user roles and capabilities, see Configure user and roles in the Installation and Upgrade Manual.
- Define the status workflow for notable event investigations. Determine which statuses to require, and whether analysts should follow a specific sequence of statuses before completing the investigation workflow. Determine whether any roles can bypass the full workflow.
Restrict notable event status transitions
- On the toolbar, select Configure > Incident Management > Status Configuration.
- Select a notable event status on the Notable tab.
- In Status Transitions, modify the To Status fields.
- To define which roles are allowed to transition a notable event to the selected status, choose the Authorization field and add or remove roles.
- To remove a transition an event to the selected status, choose Unselect All.
- Save the changes.
- Test the changes to the status workflow. If any transitions required adding or removing roles, test with credentials assigned to each role.
Add a new status
Add a new status to the notable event investigation workflow. If you restrict status transitions, determine where this status fits in the workflow.
- Define the status workflow for notable events.
- Determine where the new status is needed in the workflow.
- Determine whether any roles will be allowed to bypass the new status in the workflow.
- On the toolbar, open Configure > Incident Management > Status Configuration.
- On the Notable tab, select New.
- Add a label. This is the Status field value used on the Incident Review dashboard and for notable event status reporting. For example, Waiting on ITOps.
- Add a description. The description is only referenced in the Notable Event Status page. For example, Waiting on another department.
- (Optional) Select Default status. Choose only if you are replacing the New status for notable events
- (Optional) Select End status. Choose when adding an additional Closed status for notable events.
- Define the Status Transitions by modifying the To Status fields.
- Review the status workflow and determine which statuses a notable event can transition to.
- Select the Authorization field and add the roles allowed to transition a notable event to the selected status.
- Save the changes.
For example, the "Waiting on ITOps" status occurs after "New" and "In Progress", but before "Pending." It is not a required status and can be skipped over to choose "Pending." Edit the Status Transitions in "Waiting on ITOps" for "Pending," "Resolved," and "Closed" and add the roles pci_admin and pci_analyst added under Authorization. - Edit the statuses that will precede the new status in the workflow, and add the roles allowed to perform the transition.
For example, a notable event can be given a status of "Waiting on ITOps" from a status of "New" and "In Progress." Edit the Status Transitions in both "New" and "In Progress" adding the pci_admin and pci_analyst roles under Authorization for "Waiting on ITOps". - Test to ensure the status can be assigned and that any status transitions involving it work.
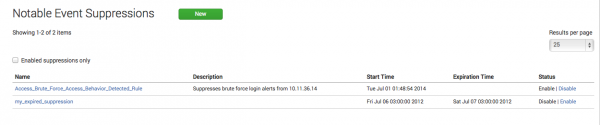
Create and manage notable event suppressions
You can hide notable events from the Incident Review dashboard by creating a notable event suppression.
A suppression is a search filter that hides additional notable events from view, and is used to stop excessive or unwanted numbers of notable events from appearing on the Incident Review dashboard. Notable events that meet the search conditions are still created and added to the notable index. Suppressed notable events continue to contribute to notable event counts on the Security Posture and auditing dashboards.
To prevent notable events that meet certain conditions from being created, see Throttle the number of response actions generated by a correlation search.
You can create a suppression filter in two ways.
- Create a suppression from Incident Review. See Suppress a notable event.
- Create a suppression from the Configure menu. See Create a suppression from Notable Event Suppressions.
Create a suppression from Notable Event Suppressions
- Select Configure > Incident Management > Notable Event Suppressions.
- Click Create New Suppression.
- Enter a Name and Description for the suppression filter.
- Enter a Search to use to find notable events to be suppressed.
- Set the Expiration Time. This defines a time limit for the suppression filter. If the time limit is met, the suppression filter is disabled.
Edit notable event suppressions
- Select Configure > Incident Management > Notable Event Suppressions.
- Select a notable event suppression to open the Edit Notable Event Suppression page.
- Edit the Description and Search fields used for the suppression filter.
Disable notable event suppressions
- Select Configure > Incident Management > Notable Event Suppressions.
- Select Disable in the Status column for the notable event suppression.
Remove a notable event suppression
- From the Splunk platform toolbar, select Settings > Event types.
- Search for the the suppression event:
notable_suppression-<suppression_name>. - Select delete in the Actions column for the notable event suppression.
Audit notable event activity
You can audit analyst incident review activity on the Incident Review Audit dashboard. Audit notable event suppressions with the Suppression Audit dashboard.
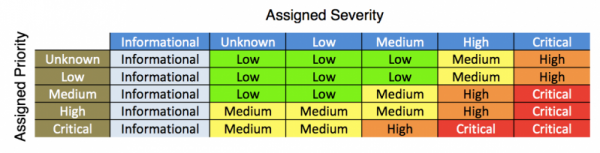
How urgency is assigned to notable events
Notable events are assigned an urgency level that is a combination of the severity of the correlation search and the priority assignment of the relevant asset or identity. You can use the Urgency field to prioritize the investigation of notable events.
You can change the urgency calculation defaults in .
- Select Configure > Content Management.
- Choose the Urgency Levels lookup. An editable, color coded table representing the urgency lookup file displays.
- In any row where the priority or severity is listed as "unknown," review the assigned Urgency.
- (Optional) Edit the table and change the Urgency.
- Save the changes
When calculating the severity level, a notable event displays a default of "low" urgency when an asset or identity is categorized as "unknown." The "unknown" classification typically represents an object that has no match in the asset and identities system.
A notable event is assigned an unknown urgency level if the severity value assigned by the correlation search or in a triggering event is not recognized by ES. This indicates an error in the severity value provided by the correlation search syntax. Verify that the correlation search severity is unknown, informational, low, medium, high, or critical.
| Notable events | Create and manage risk factors in |
This documentation applies to the following versions of Splunk® App for PCI Compliance: 3.5.0, 3.6.0, 3.6.1, 3.7.0, 3.7.1, 3.7.2, 3.8.0, 3.8.1, 4.0.0, 4.0.1, 4.1.0, 4.1.1, 4.3.0, 4.4.0, 4.4.1, 4.5.0 Cloud only, 4.6.0, 4.6.2
 Download manual
Download manual
Feedback submitted, thanks!