Incident Review
The Incident Review dashboard displays notable events and their current status. As an analyst, you can use the dashboard to gain insight into the severity of events occurring in your system or network. You can use the dashboard to triage new notable events, assign events to analysts for review, and examine notable event details for investigative leads.
How identifies notable events
detects patterns in your data and automatically reviews events for security-relevant incidents using correlation searches. When a correlation search detects a suspicious pattern, the correlation search creates an alert called a notable event.
The Incident Review dashboard surfaces all notable events, and categorizes them by potential severity so you can quickly triage, assign, and track issues.
To view sequenced events in the Incident Review dashboard, make sure that governance="pci" is cleared from the Search field.
Incident review workflow
You can use this example workflow to triage and work notable events on the Incident Review dashboard.
- An administrative analyst monitors the Incident Review dashboard, sorting and performing high-level triage on newly-created notable events.
- When a notable event warrants investigation, the administrative analyst assigns the event to a reviewing analyst to start investigating the incident.
- The reviewing analyst updates the status of the event from New to In Progress, and begins investigating the cause of the notable event.
- The reviewing analyst researches and collects information on the event using the fields and field actions in the notable event. The analyst records the details of their research in the Comments field of the notable event.
- After the reviewing analyst addresses the cause of the notable event and any remediation tasks have been escalated or solved, the analyst sets the notable event status to Resolved.
- The analyst assigns the notable event to a final analyst for verification.
- The final analyst reviews and validates the changes made to resolve the issue, and sets the status to Closed.
Triage notable events on the Incident Review dashboard
Use this dashboard as part of your incident triage workflow. You can monitor notable events and the actions that analysts take to resolve the issues that triggered a notable event.
You must wait for your search to complete before you can manage notable events or view event details.
Accelerate triage with tags and filters
Speed up your notable event triage with search filters, tagging, and sorting. For example, focus on groups of notable events or an individual notable event with the search filters and time range selector. Notable events contain Urgency, Status, and Owner fields to help you categorize, track, and assign events.
Simplify searching and add identifiers to notable events using tags. Click Edit Tags in the field actions menu for a notable event field such as Title, Status, or Owner to add new tags or modify existing ones. After you create a tag, you can use it to filter the dashboard.
Assign notable events
You can assign one event at a time or several at once.
- Select a notable event.
- Click Edit selected.
- Select an Owner to assign the event or events to. Or, click Assign to me to assign the event or events to yourself.
- Save your changes.
Owners are unassigned by default, and you can assign notable events to any user with an administrator, pci_admin, or pci_analyst role. For more on user roles, see Configure users and roles in the Installation and Upgrade Manual.
Update the status of a notable event
New notable events have the New status. As analysts triage and move a notable event through the incident review workflow, the owner can update the status of the notable event to reflect the actions they take to address the event.
- Select one or more events, then click Edit all selected. To take action on all displayed events, click Edit all ## matching events.
- In the Edit Events window, update the fields to reflect your actions.
- (Optional) Add a Comment to describe the actions you took.
- Save changes.
Note: If your changes are not immediately visible, check the dashboard filters. For example, if the filter is set to "New" after you changed an event to "In Progress", your updated event will not display.
You can require analysts to enter comments when updating a notable event. See Customize Incident Review for more.
You can choose from the following notable event statuses.
| Status | Description |
|---|---|
| Unassigned | The event has not been assigned to an owner. |
| New | Default status. The event has not been reviewed. |
| In Progress | An owner is investigating the event. |
| Pending | An action must occur before the event can be closed. |
| Resolved | The owner has addressed the cause of the event and is waiting for verification. |
| Closed | The resolution of the event has been verified. |
You can customize the notable event status names and workflow progression to match your process.
Prioritize notable events by urgency
Use the urgency level of a notable event to prioritize incident review. Every notable event is assigned an urgency. Urgency levels can be unknown, low, medium, informational, high, or critical.
Urgency levels are calculated using the severity of the correlation search event and the priority of the asset or identity involved in the event.
By default, security analysts can change the urgency of a notable event. See Customize Incident Review to learn how to change that default.
Notify an analyst of untriaged notable events
You can use a correlation search to notify an analyst if a notable event has not been triaged.
- Select Configure > Content Management.
- Locate the Untriaged Notable Events correlation search using the filters.
- Modify the search, changing the notable event owner or status fields as desired.
- Set the desired alert action.
- Save the changes.
- Enable the Untriaged Notable Events correlation search.
Review details of notable events
After you finish triaging notable events, begin your investigation. Use the available fields on a notable event to assess the urgency, contributing events, and risk scores associated with the notable event.
Open the event details to learn more about a notable event.
- Review the History to see the recent investigation activity on the notable event. Click View all recent activity for this Notable Event to see analyst comments, status changes, and other activities for the event.
- See which correlation search generated the notable event. Click the name of the correlation search to make changes to or review the correlation search to understand why the notable event was created.
- View the Contributing Events that caused the notable event to be created.
- Review the risk scores listed for assets and identities involved in a notable event. Click a risk score to open the Risk Analysis dashboard filtered on that asset or identity.
- If one original event created a notable event, you can see the full details.
- Review the Adaptive Responses to see which adaptive response actions have been performed for this notable event, whether the actions were successfully performed, and drill down for more details. Click the name of the response action to see potential results generated by this action's invocation. Click View Adaptive Response Invocations to see the raw audit events for the response actions associated with this correlation search. It takes up to five minutes for updates to appear on this table.
- Review the Next Steps to see if any next steps for notable event triage are defined.
Take action on a notable event
From Incident Review, you can suppress or share a notable event, add an event or multiple events to an investigation, analyze the risk that an asset or identity poses to your environment, or investigate a field in more detail on another dashboard.
Run an adaptive response action
Based on the details in a notable event, you may want to run a response action to gather more information, take an action in another system, send information to another system, modify a risk score, or something else.
- From a notable event, select the arrow to expand the Actions column.
- Click Run Adaptive Response Actions.
- Click Add New Response Action and select an adaptive response action from the list. You can use the category filter or search to reduce the number of actions that you can select.
- Fill out the form fields for the response action. Use the field name to specify a field, rather than the name that shows on Incident Review.
For example, type "src" instead of "Source" to specify the source field for an action. - Click Run.
You can check the status of the response action in the notable event details. You cannot run adaptive response actions from the Search dashboard. View the original field names of fields displayed on Incident Review on the Incident Review - Event Attributes panel of the Incident Review Settings dashboard.
Adblock extensions in your browser can cause response actions to fail. Add the host name of your Splunk Enterprise Security host to the site whitelist for the adblock extension.
See Included adaptive response actions with for more about the different adaptive response actions included with .
Share a link to a notable event with another analyst, or bookmark it for later. From the event actions, click Share Notable Event. You cannot share a notable event from the Search dashboard.
Analyze risk of an asset or identity
You can analyze the risk that an asset or identity poses to your environment in the Incident Review dashboard.
- Open the event details.
- Review the risk score next to asset or identity fields such as src or host.
- Click the risk score to open the Risk Analysis dashboard filtered on the asset or identity.
Not all assets and identities display a risk score. Risk scores that display for an asset or identity in Incident Review may not match the risk score on the Risk Analysis dashboard for that risk object. See How risk scores display in Incident Review for more.
Add a notable event to an investigation
Add a single event by selecting Add Event to Investigation from the Event Actions.
Add multiple events to an investigation timeline to investigate them further.
- Select several notable events, then click Add to Investigation.
- A dialog box appears. Select Create new investigation.
- Add a title (required) and a description (optional) for your new investigation.
- Click Save to add the selected events to the investigation. Clicking Cancel will create a new investigation without adding the selected notable events.
See Investigation Timelines for more.
Investigate a field in more detail
Take action on a specific field, such as host, src, src_ip, dest, or dest_ip. Different actions are available to take depending on the field you select.
- Tag fields by selecting Edit tags.
- Investigate an asset by selecting Asset Investigator to open the Asset Investigator dashboard filtered on the asset.
- Search for access-related events for a specific destination IP address by selecting Access Search (as destination).
- Investigate a domain by selecting Domain Dossier.
- Find other notable events with matching malware signatures by selecting Notable Event Search.
Suppress a notable event
Hide notable events from the Incident Review dashboard by suppressing them. Creating a notable event suppression does not change the counts of notable events on the posture or auditing dashboards.
- Select a notable event on the Incident Review dashboard.
- From the Actions menu, select Suppress Notable Events.
- Type a Suppression Name.
For example, Excessive_Failed_Logins.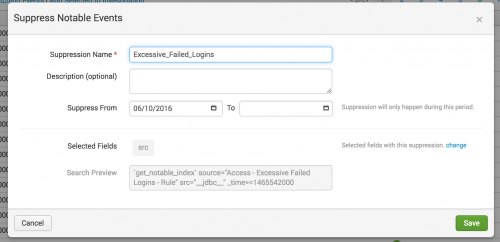
- (Optional) Provide a reason for the suppression using the Description field.
- (Optional) Set a date range. After the time limit ends, the suppression filter expires and stops hiding events.
- Review the Selected Fields to validate the fields that you want to suppress notable events from. For example, the
srcfield. - (Optional) Click change to modify the notable event fields used for the suppression.
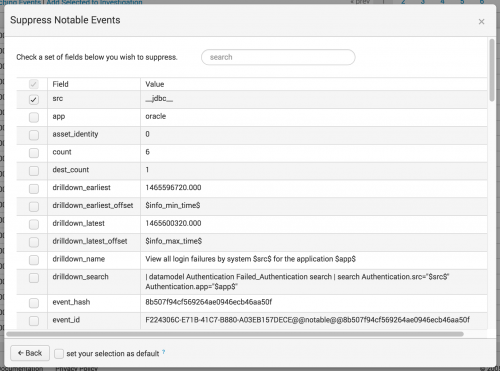
- Save changes.
This example notable event suppression hides all notable events created after June 10, 2016 that contain a src=_jdbc_ field from Incident Review.
You cannot suppress notable events from the Search dashboard.
Audit incident review activity
You can audit and review incident review activity on the Incident Review Audit dashboard.
Customize Incident Review
Customize the display of the Incident Review dashboard, and also modify analyst capabilities and permissions.
Modify analyst capabilities and permissions
You can change the default capabilities and permissions assigned to analysts to better fit your workflow.
Configure whether analysts can override the calculated urgency of a notable event and choose whether to require an analyst to add a comment when updating a notable event on the Incident Review Settings page.
- Select Configure > Incident Management > Incident Review Settings to view the Incident Review settings.
- Allow or prevent analysts from overriding the calculated urgency of a notable event with the Allow Overriding of Urgency checkbox. Analysts are allowed to override urgency by default.
- Require analysts to add a comment when updating a notable event by checking the Required checkbox under Comments.
- If you require analysts to add a comment, enter the minimum character length for required comments. The default character length is 20 characters.
Configure the desired capacity of your security analysts on the General Settings page.
- Select Configure > General > General Settings to view the General Settings.
- Enter a preferred number of incidents that should be assigned to an analyst with the Incident Review Analyst Capacity setting. The default is 12.
This value is used for tracking purposes, and does not prevent more than the default number of notable events from being assigned to an analyst.
Change Incident Review columns
You can change the columns displayed on the Incident Review dashboard.
- Review the existing columns in Incident Review - Table Attributes.
- Use the action column to edit, remove, or change the order of the available columns.
- Add custom columns by selecting Insert below or selecting More..., then Insert above.
Change notable event fields
Make changes to the fields displayed on the Incident Review dashboard for notable events on the Incident Review Settings dashboard.
- From the menu bar, select Configure > Incident Management > Incident Review Settings.
- Review the Incident Review - Event Attributes.
- Click Edit to change the field or the field label for a specific field.
- Click Remove to remove a field from displaying on the Incident Review dashboard.
How risk scores display in Incident Review
Risk scores do not display in Incident Review for every asset or identity. Only assets or identities (risk objects) that have a risk score and a risk object type of "system" or "user" display in Incident Review. Risk scores only show for the following fields: orig_host, dvc, src, dest, src_user, and user.
The risk score for an asset or identity might not match the score on the Risk Analysis dashboard. The risk score is a cumulative score for an asset or identity, rather than a score specific to an exact username.
- For example, if a person has a username of "buttercup" that has a risk score of 40, and an email address of "buttercup@splunk.com" with a risk score of 60, and the identity lookup identifies that "buttercup" and "buttercup@splunk.com" belong to the same person, a risk score of 100 displays on Incident Review for both "buttercup" and "buttercup@splunk.com" accounts.
- As another example, if an IP of 10.11.36.1 has a risk score of 80 and an IP of 10.11.36.19 has a risk score of 30, and the asset lookup identifies that a range of IPs "10.11.36.1 - 10.11.36.19" belong to the same asset, a risk score of 110 displays on Incident Review for both "10.11.36.1" and "10.11.36.19" IP addresses.
Risk scores are calculated for Incident Review using the Threat - Risk Correlation - Lookup Gen lookup generation search. The search runs every 30 minutes and updates the risk_correlation_lookup lookup file. To see more frequent updates to the risk scores in Incident Review, update the cron_schedule of the saved search.
| PCI Compliance Posture dashboard | Scorecards |
This documentation applies to the following versions of Splunk® App for PCI Compliance: 5.0.0
 Download manual
Download manual
Feedback submitted, thanks!