About Splunk Phantom
Splunk Phantom is a Security Orchestration, Automation, and Response (SOAR) system. The Splunk Phantom platform combines security infrastructure orchestration, playbook automation, and case management capabilities to integrate your team, processes, and tools to help you orchestrate security workflows, automate repetitive security tasks, and quickly respond to threats.
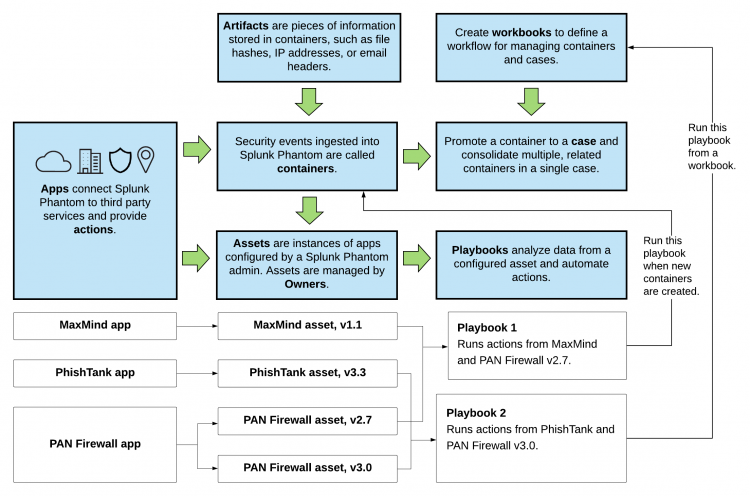
This diagram shows the end-to-end flow of security automation in Splunk Phantom. See the table immediately following the diagram for more information about each Splunk Phantom component in the diagram.
| Component | Description |
|---|---|
| App | Adds connectivity to third-party security technologies. The connections allow Splunk Phantom to access and run actions that are provided by the third-party technologies. Some apps also provide a visual component such as widgets that can be used to render data produced by the app.
See Add and configure apps and assets to provide actions in Splunk Phantom in the Administer Splunk Phantom manual. |
| Asset | A specific instance of an app. Each asset represents a physical or virtual device within your organization such as a server, endpoint, router, or firewall. For example, you might have a Palo Alto Network (PAN) firewall app that connects the firewall to Splunk Phantom. You can configure an asset with the specific connection details for this firewall. If your environment has multiple firewalls, you can configure one asset for each firewall.
See Add and configure apps and assets to provide actions in Splunk Phantom in the Administer Splunk Phantom manual. |
| Container | A security event that is ingested into Splunk Phantom.
You can create custom labels in Splunk Phantom as needed. See Configure labels to apply to containers in the Administer Splunk Phantom manual. |
| Case | A special kind of container that can hold other containers. For example, if you have several closely related containers for a security incident, you can promote one of those containers to a case and then add the other related containers to the case. Doing this lets you consolidate your investigation rather than having to investigate each container individually.
|
| Artifact | A piece of information added to a container, such as a file hash, IP address, or email header. |
| Indicator or Indicator of Compromise (IOC) | A piece of data such as an IP address, host name, or file hash that populates the Common Event Format (CEF) fields in an artifact. Indicators are the smallest unit of data that can be acted upon in Splunk Phantom. |
| Playbook | Defines a series of automation tasks that act on new data entering Splunk Phantom. For example, you can configure a playbook to run actions against all new containers with a specific label. Or you can configure running a playbook as part of the workflow in a workbook.
See Use playbooks to automate analyst workflows in Splunk Phantom in the Build Playbooks with the Visual Editor manual. |
| Workbook | A template providing a list of standard tasks that analysts can follow when evaluating containers or cases.
|
| Action | A high level primitive used throughout the Splunk Phantom platform, such as get process dump, block ip, suspend vm, or terminate process. Actions are run in playbooks or manually from the Splunk Phantom web interface.
|
| Owner | The person responsible for managing assets in your organization. Owners receive approvals, which are requests to run a particular action on an asset. Approvals are sent to the asset owners and contain a service level agreement (SLA) dictating the expected response time. SLAs can be set on events, phases, and tasks.
|
| Who should read this manual? |
This documentation applies to the following versions of Splunk® Phantom (Legacy): 4.9, 4.10, 4.10.1, 4.10.2, 4.10.3, 4.10.4, 4.10.6, 4.10.7
 Download manual
Download manual
Feedback submitted, thanks!