About Private Spacebridge
Use the Connected Experiences mobile apps on your own Kubernetes cluster with Private Spacebridge. Spacebridge is the backend infrastructure that allows mobile devices to securely connect to a Splunk platform instance. You can deploy Private Spacebridge directly within your own Kubernetes cluster so that you can own an end-to-end pipeline for connecting mobile devices to your Splunk platform instance.
To learn more about Spacebridge, Splunk Secure Gateway, and how we keep your data safe, see About the Splunk Secure Gateway security process in the Administer Splunk Secure Gateway manual.
Is Private Spacebridge right for your deployment?
Splunk recommends you use the Splunk-hosted Spacebridge services for the best experience for the following reasons:
- Private Spacebridge doesn't support push notifications for mobile devices. Mobile device users can still view dashboards but cannot receive alert notifications.
- Privately hosting your own Spacebridge requires familiarity with Kubernetes and Helm. An admin must deploy our Helm chart and be responsible for managing the networking to and from the application as well as persistent volumes required by the application.
However, you might want to host a Private Spacebridge for the following reasons:
- You want to deploy the Connected Experiences applications so that they can access Splunk data on a closed network.
- You don't plan to make use of mobile push notifications.
- You're unable to use our globally hosted Spacebridge. See Splunk Secure Gateway and Spacebridge Compliance Standards in the Administer Splunk Secure Gateway manual to learn more about Spacebridge security and compliance standards.
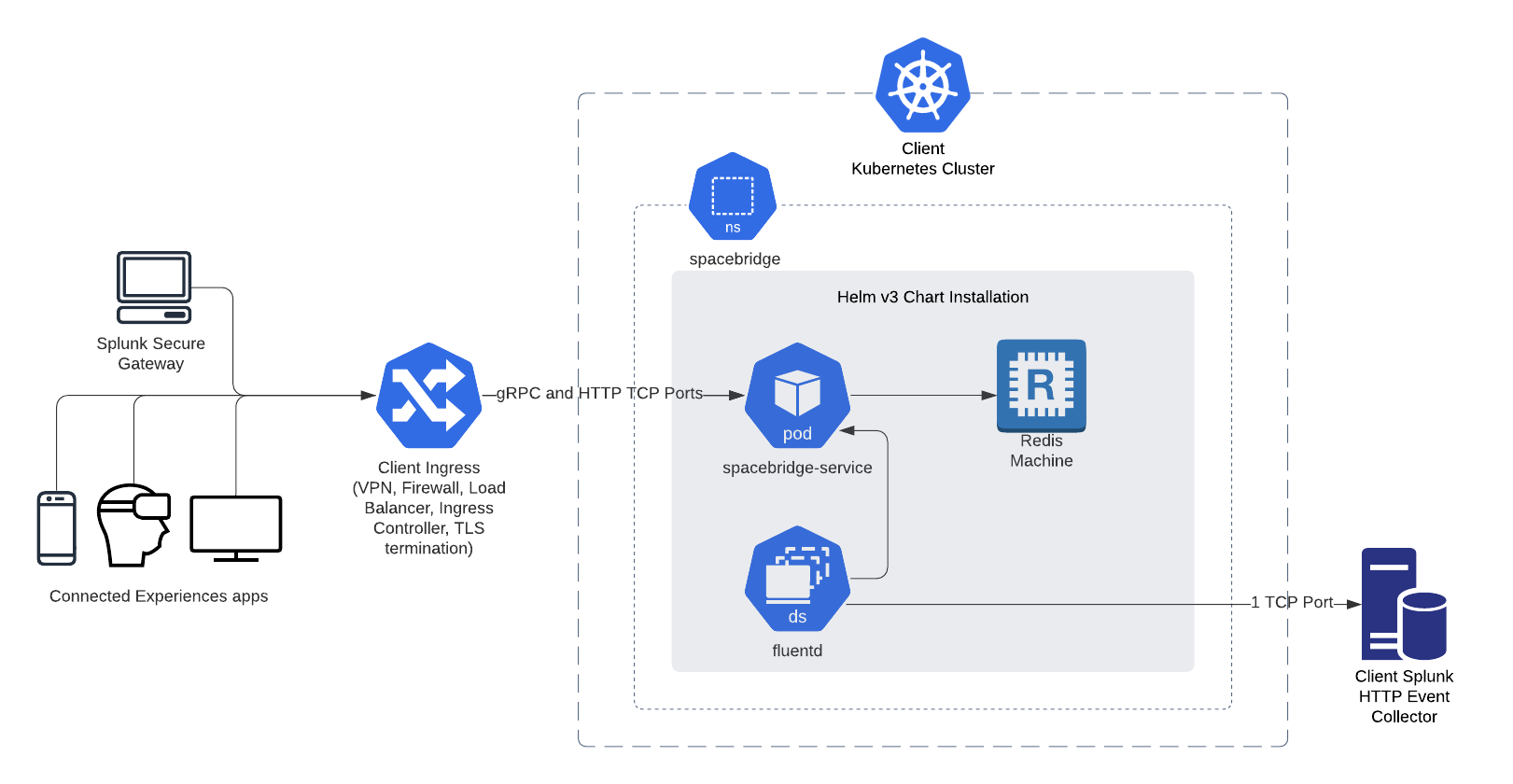
Private Spacebridge architecture
The following diagram illustrates connections from the initiating client. The Kubernetes namespace is spacebridge, the Kubernetes pod is spacebridge-service, and the Kubernetes DaemonSet is fluentd.
Kubernetes network policy accepts ingress from two ports on TCP -- gRPC and HTTP. Kubernetes network policy restricts egress from the spacebridge namespace, except for Splunk log forwarding. Internal resources, such as Redis, are not accessible external to the spacebridge namespace.
Get started
See Get started with Private Spacebridge to set up Private Spacebridge.
| Get started with Private Spacebridge |
This documentation applies to the following versions of Splunk® Private Spacebridge: 1.0.0, 1.1.0
 Download manual
Download manual
Feedback submitted, thanks!