Configure correlation searches in the Splunk Security Add-on for SAP solutions
The Splunk Security Add-on for SAP® solutions ships with three configured correlation searches that help you detect suspicious events based on certain SAP ETD alert categories and generate a notable event.
The correlation searches are turned off by default and must be turned on by the user. To turn on correlation searches follow these steps:
- Select Settings.
- Under Knowledge, choose Searches, reports, and alerts.
- Filter the page by app. From the app menu choose Splunk Security Add-on for SAP solutions (splunk_ta_sap_etd_alerts).
- For each of the listed searches, choose the Edit action and select Enable.
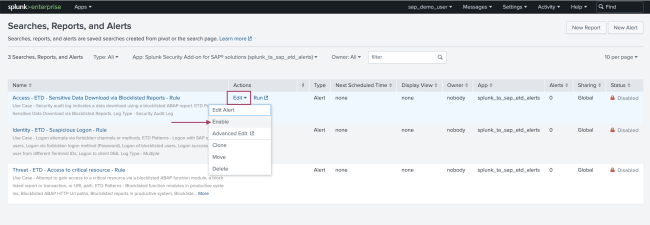
- On the resulting modal window confirm the status change by selecting Enable again.
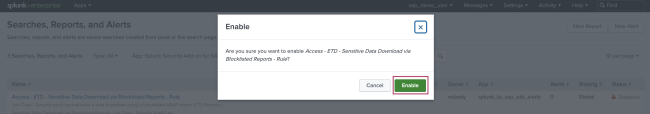
- The search status is now updated.
For more information on correlation searches and how to use them, see Correlation search overview for Splunk Enterprise Security in the Administer Splunk Enterprise Security manual.
Available correlation searches
The following table lists the correlation searches that come configured with Splunk Security Add-on for SAP solutions:
| Correlation search name | Description | ETD patterns | Log type |
|---|---|---|---|
| Access - ETD - Sensitive Data Download via Blocklisted Reports - Rule | Security audit log indicates a data download using a blocklisted ABAP report. | Sensitive Data Download via Blocklisted Reports. | Security Audit Log |
| Identity - ETD - Suspicious Logon - Rule | Logon attempts using forbidden channels or methods. | Logon with SAP standard users, Logon through forbidden logon method (Password), Logon of blocklisted users, Logon success same user from different Terminal IDs, Logon to client 066. | Multiple |
| Threat - ETD - Access to critical resource - Rule | Attempt to gain access to a critical resource through a blocklisted ABAP function module, a blocklisted report or transaction, or URL path. | Blocklisted function modules in productive systems, Blocklisted ABAP HTTP URL paths, Blocklisted reports in productive system, Blocklisted transaction in productive systems, Suspicious Activity in Client 066. | Security Audit Log |
| Get SAP ETD data into the Splunk Security Add-on for SAP solutions | Workflow actions in the Splunk Security Add-on for SAP solutions |
This documentation applies to the following versions of Splunk® Security Add-on for SAP® solutions: 1.0.0
 Download manual
Download manual
Feedback submitted, thanks!