Overview of Splunk Intelligence Management custom integrations
You can write custom integrations between your data and the Splunk Intelligence Management platform. You can create integrations for the following types of third-party tools:
- Detection: Export data from Splunk Intelligence Management into your detection workflow to provide more accurate and timely alerts.
- Case Management: Automate and streamline the exchange of data between Splunk Intelligence Management and your cybersecurity tools.
- SOAR: Prioritize suspicious emails by using Splunk Intelligence Management to ingest emails, then extract and score indicators that are then sent to your orchestration workflow.
With any integration, you can also choose to validate, redact, and share information among Splunk Intelligence Management enclaves. This means you can disseminate information to internal teams and industry peers (ISACs/ISAOs) that have access to those enclaves.
Before you begin
- Read the Splunk Intelligence Management product overview so that you understand how the platform is structured.
- Make sure you have a Splunk Intelligence Management account because you'll need your API key and API secret to build the integration.
- Choose the developer tool, either the REST API or Python SDK, you want to use when coding your integration.
To learn how to create and manage users, assign permissions, and collect a user's API keys in Splunk Intelligence Management, see the following video:
Managing users and permissions
Supported functionality
When building an integration with Splunk Intelligence Management, you choose what functionality to include. This may be based on your customer knowledge, the capabilities of your detection tools, or other factors. Two levels of functionality for integrations are defined:
- Recommended: Provide the most useful functionality for that type of tool. Think of this as "must have" functionality, such as submitting reports to Splunk Intelligence Management and enriching observables.
- Optional: Functions that enhance the integration but are not essential. For example, you may choose to share observables or reports, but it is not a "must have" for most integrations.
Configuration requirements
Every integration with Splunk Intelligence Management needs to include basic information, including account information, whether or not a proxy is used, and the enclaves that will be accessed by the integration. Verify that you are able to provide the following information:
- Account settings: Required to ensure the user has a valid Splunk Intelligence Management account.
- Enclave Settings: For each type of Enclave your integration is using, you must provide a way to specify Enclave IDs.
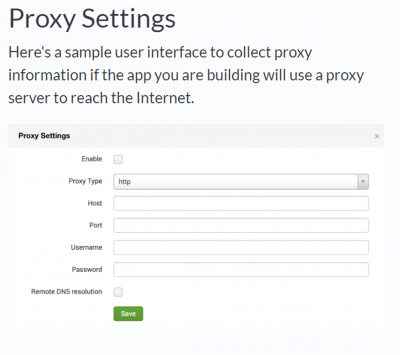
- Proxy Settings: If your integration will go through a proxy server to reach the internet, you must provide a way to specify those settings.
Account Settings
Your integration must provide a way for the user to enter three pieces of information:
- The Splunk Intelligence Management API URL. You can hardcode this to https://blog.postman.com/announcing-postman-for-the-web-now-in-open-beta/.
- The user's Splunk Intelligence Management API Key.
- The user's Splunk Intelligence Management API Secret.
Enclave settings
Depending on your integration, you can specify any number of enclaves.
Required enclaves
Your integration must specify the location of one or more enclaves where reports or indicators will be stored in Splunk Intelligence Management. Name this field Submission Enclave IDs. Separate multiple enclave IDs with commas, no spaces. See Finding enclave IDs.
You can also provide checkboxes to let the user choose to automatically submit reports and observables to Splunk Intelligence Management.
Optional enclaves
Depending on the integration you are building, you may need to provide fields for additional enclaves.
| Optional enclave type | Description |
|---|---|
| Enrichment Enclaves | If your integration will enrich observables in an event or report, you need to specify which enclaves can be used for that enrichment. Name this field Enrichment Enclave IDs.
You can also choose to offer an option to automatically enrich observables when they are submitted to Splunk Intelligence Management. Provide a checkbox for automatic submisstion of observables. |
| Sharing enclaves | If your integration allows the user to share observables or reports with other enclaves, you will need to provide one or more enclave IDs where the items can be moved or copied to in Splunk Intelligence Mangement. Name this field Destination Enclave IDs.
When sharing reports, you can offer the user the option to redact information from the reports using the Company Safelist stored in Splunk Intelligence Management. In most cases, this can be a checkbox. |
| Searching enclaves | You can specify one or more Enclave IDs to search for Observables. Name this field Search Enclave IDs. If no Enclave IDs are specified, the commands will search all Enclaves that the user has access to in Splunk Intelligence Management. |
| Phishing Triage enclaves | When using the Phishing Triage workflow, you can set up this functionality within your integration:
|
Proxy settings
Here's a sample user interface to collect proxy information if the app you are building will use a proxy server to reach the Internet.
Finding your API keys
Follow these steps to find your API Key and API Secret.
- In the Splunk intelligence Management Navigation Bar, click User Settings and select Settings from the dropdown menu.
- Click API to display the API panel.
- Select the checkbox and agree to the "Terms of Use" policy.
- Click Generate to generate API information.
Alternatively, click Regenerate if you must regenerate the API information for any reason.
| Access threat intelligence using the interfaces in Splunk Intelligence Management |
This documentation applies to the following versions of Splunk® Intelligence Management (Legacy): current
 Download manual
Download manual
Feedback submitted, thanks!