For details, see:
ports and endpoints
These tables list the ports which must be open to inbound traffic and internet endpoints which must be accessible to use . Use these tables to design the firewall rules for your deployment.
If Splunk SOAR (On-premises) is deployed on Red Hat Enterprise Linux 8.x you must use TLS 1.3 or higher on all apps, connectors, or assets connecting to Splunk SOAR (On-premises).
Endpoints for all deployments
This table shows a list of the internet endpoints that a deployment uses. This list is not exhaustive.
| Endpoint | Outbound port | Protocol | Required? | Description |
|---|---|---|---|---|
| splunkbase.splunk.com | 443 | HTTPS | Required | Required for app installation and app upgrades. |
| Splunk Cloud | 9997, 8089 | TCP | Conditional | If your deployment uses a Splunk Cloud deployment instead of the embedded Splunk Enterprise instance, must be able to reach your Splunk Cloud deployment. If your Splunk SOAR (On-premises) deployment connects to a Splunk Cloud deployment in a restricted environment, you must ensure your Splunk Cloud deployment accepts and sends traffic on TCP port 9997. |
| grpc.prod1-cloudgateway.spl.mobi | 443 | HTTPS | Conditional | If you use Splunk Mobile to access on mobile devices, your deployment must be able to reach grpc.prod1-cloudgateway.spl.mobi |
| https://e1345286.api.splkmobile.com/1.0/e1345286 | 443 | HTTPS | Conditional | telemetry |
| https://rs.fullstory.com/rec/bundle/v2?OrgId=o-1JE2QP-na1 | 443 | HTTPS | Conditional | FullStory telemetry. See Share data from for more. |
| *.pool.ntp.org | 123 | UDP | Required | Used by the chronyd service for system clock synchronization. |
| CentOS and RHEL mirrors | 443 | HTTPS | Required | Required to run YUM updates for operating system components and installed software packages. If your organization prefers, you can use a satellite server instead. See the Red Hat Knowledgebase article https://access.redhat.com/solutions/29269. |
| github.com | 443 | HTTPS | Required | Used to access the community playbook repository. |
| Other source control system | Dependent on the source control system. | Dependent on the source control system. | Conditional | Access is required if your deployment uses an alternative repository for playbooks. |
| Google Maps embed API | 443 | HTTPS | Conditional | Used by the MaxMind app to add visualizations for IP address geolocation results. |
| pypi.org | 443 | HTTPS | Required | Used by some apps to update or install their PIP dependencies. |
| App specific endpoints | Dependent on the app. | Dependent on the app. | Conditional | Apps might need to reach specific endpoints in order to provide their functions. Consult the app's documentation for details. |
Ports for a standalone deployment
On a single instance deployment of where all services are contained on the same host, open these inbound ports in addition to allowing the Endpoints for all deployments.
| Port | Required? | Description |
|---|---|---|
| TCP 22 | Required | SSH port. Used for administering the operating system. |
| TCP 80 | Required | Port for requests sent over HTTP. redirects all HTTP requests to HTTPS. |
| TCP 443 | Optional | HTTPS port for the web interface and REST API. This port is for HTTPS traffic if you use the --port-forward option or answer "yes" to the port forwarding question when you install . This port must be exposed to access services without specifying the custom HTTPS port in the URL.
|
| TCP 8443 | Required, Configurable | HTTPS ports for the web interface and REST API. This port must be exposed to access services. You specify a custom HTTPS port during installation. It must be a port greater than 1023. During upgrades from privileged deployments, Splunk SOAR (On-premises) will set firewalld rules to forward TCP 443 to TCP 8443. AMI-based deployments do not need to open this port. |
| TCP 8888 | Required | Used for local communications between the WebSocket server and other components. Port must be available, but does not have to be open for external ingress or egress. |
| TCP 9999 | Required for AMI-based deployments |
HTTPS ports for the web interface and REST API. This port must be exposed to access services. For all AMI-based deployments, port 9999 is set as the custom HTTPS port. |
| TCP 9001, 9002 | Required | Customized ports for a universal forwarder, used in conjunction with Splunk Mission Control. These ports are configured at installation or upgrade of . |
Ports for externalized services
If you opt to deploy services such as Splunk Enterprise or Splunk Cloud, PostgreSQL, or a file share separately from your deployment, you need to make sure that can reach those services on your network.
In a clustered deployment, all services are external to , and there is an added load balancer. See Example: cluster for a diagram of a cluster.
Required ports for Splunk Universal Forwarders
The embedded Splunk Enterprise has been removed from Splunk SOAR (On-premises) release 6.2.0 replaced by Universal Forwarders. See About the universal forwarder in the Forwarder Manual.
Splunk Universal Forwarder version: 9.0.8
Open these inbound ports on each node for embedded Splunk cluster configuration.
| Port | Purpose |
|---|---|
| TCP 5121 | Used on localhost to communicate with Universal Forwarders. |
| TCP 9997 | Used for outbound communications by Universal Forwarders to Splunk Enterprise or Splunk Cloud deployments. |
Required ports for non-embedded Splunk Enterprise
If you are using an external version of Splunk Enterprise, open these inbound ports on each node.
| Port | Purpose |
|---|---|
| TCP 9996-9997 | Used for the universal forwarder to either forward or direct the indexers. |
PostgreSQL database
A single instance deployment of uses a local instance of a PostgreSQL database. If you choose to use an external PostgreSQL database instead, you must make sure that can reach the database on your network. Open these inbound ports on each node for PostgreSQL connections.
In a clustered deployment, each node must be able to reach the PostgreSQL database. See About clusters in Install and Upgrade .
| Port | Description |
|---|---|
| TCP 5432 | PostgreSQL service. This port is also used by warm standby configurations for PostgreSQL streaming replication. |
| TCP 6432 | Used by PgBouncer to interact with the PostgreSQL database. |
A single instance deployment of uses the local file system to store files for the vault. You can choose to expand storage capacity by using an external file share.
You can use any file system that meets your organization's security and performance requirements for your external file shares. You need to configure any required mounts and permissions. See Supported file systems and required directories.
These following tables uses NFS and GlusterFS as an example for file shares. In a clustered deployment, these inbound ports must be opened on each node, and in the case of GlusterFS, on each member of the GlusterFS server cluster.
| Port | Description |
|---|---|
| TCP 445 | CIFS protocol. |
| UDP 111 | RPC portmapper service for GlusterFS and NFS. |
| TCP 111 | RPC portmapper service for GlusterFS and NFS. |
| TCP 2049 | GlusterFS and NFS for NFS exports. Used by the nfsd process. |
| TCP 38465 | NFS mount protocol. |
| TCP 38466 | NFS mount protocol. |
| TCP 38468 | NFS Lock Manager, NLM. |
| TCP 38469 | NFS ACL support. |
| TCP 24007 | glusterd management port. |
| TCP 24008 | glusterd management port. |
| TCP 49152+ | For GlusterFS brick mounts. The total number of ports required to be open depends on the total number of bricks exported on the server. In most cases, 10 bricks is sufficient. You might need to open additional ports later if you add additional bricks. |
Warm Standby
A single instance deployment of can have a warm standby configured to take over in the event of a failure of the primary deployment . See Warm standby feature overview in Administer Splunk SOAR (On-premises).
Opening these inbound ports on each node is a prerequisite to enable warm standby.
| Port | Description |
|---|---|
| TCP 22 | SSH port. Used to send commands and to rsync data to the warm standby. |
| TCP 5432 | PostgreSQL service. This port is used by warm standby configurations for PostgreSQL streaming replication. |
Ports for connecting mobile devices to using Splunk Connected Experience apps
Open these inbound ports to enable registration of mobile apps, such as Splunk Mobile for iOS or Splunk Mobile for Android. In a clustered deployment, these ports must be opened on each node.
When the Enable Mobile App toggle is in the ON position, launches a new daemon, ProxyD. ProxyD connects to the Splunk Cloud Gateway automatically at grpc.prod1-cloudgateway.spl.mobi, on port 443 using the gRPC protocol.
uses the gRPC protocol to communicate to mobile apps through the Splunk Cloud Gateway.
For more information on Splunk Cloud Gateway, its encryption, and the data that is sent and received, see About the Splunk Cloud Gateway security process in Install and Administer Splunk Cloud Gateway.
| Port | Description |
|---|---|
| TCP 15505 | Port 15505 is used by ProxyD to listen for inter-process communication from other daemons on the same instance. |
| TCP 443 | Port 443 is the inbound port to 's REST endpoints from ProxyD. REST requests from connected mobile devices received from Splunk Cloud Gateway are sent to and received from other daemons by ProxyD on port 443. |
For other ports you might need to open, see Prerequisites and Requirements in the Install and Administer Splunk Cloud Gateway manual.
Ports for clustered deployments of
can be deployed as a cluster of nodes connected to a server or set of servers providing a PostgreSQL database, file shares, a Splunk platform deployment, and a load balancer. A cluster can be deployed on-premises or in Amazon Web Services. See About clusters in Install and Upgrade .
This table lists the inbound ports required by nodes for inter-node communication and access to services on the cluster.
| Port | Description |
|---|---|
| TCP 22 | SSH port. Used for administering the operating system of the cluster node. Also used by SSHD for GlusterFS. |
| TCP 80 | Port for requests sent over HTTP. redirects all HTTP requests to HTTPS. |
| TCP 443 | HTTPS port for the web interface and REST API. This port is for HTTPS traffic if you use the --port-forward option or answer "yes" to the port forwarding question when you install . This port must be exposed to access services without specifying the custom HTTPS port in the URL.
|
| TCP 8443 | HTTPS ports for the web interface and REST API. This port must be exposed to access services. You specify a custom HTTPS port during installation. It must be a port greater than 1023. During upgrades from privileged deployments, Splunk SOAR (On-premises) will set firewalld rules to forward TCP 443 to TCP 8443. AMI-based deployments do not need to open this port. |
| TCP 9999 | HTTPS ports for the web interface and REST API. This port must be exposed to access services. For all AMI-based deployments, port 9999 is set as the custom HTTPS port. |
| TCP 4369 | RabbitMQ port mapper. All cluster nodes must be able to communicate with each other on this port. |
| TCP 5100 - TCP 5120 | Daemon inter-process communication ports. |
| TCP 5671 | RabbitMQ service. All cluster nodes must be able to communicate with each other on this port. |
| TCP 8300 | Consul RPC services. All cluster nodes must be able to communicate with each other on this port. |
| TCP 8301 | Consul internode communication. All cluster nodes must be able to communicate with each other on this port. |
| TCP 8302 | Consul internode communication. All cluster nodes must be able to communicate with each other on this port. |
| TCP 8888 | Used for local communications between the WebSocket server and other components. Port must be available, but does not have to be open for external ingress or egress. |
| TCP 15672 | RabbitMQ admin UI and HTTP API service.
The RabbitMQ admin UI is disabled by default. Unless you want to use the admin UI, you can block this port. If you choose to activate the RabbitMQ HTTP API and web UI, all cluster nodes must be able to communicate with each other on this port. |
| TCP 25672 | RabbitMQ internode communications. All cluster nodes must be able to communicate with each other on this port. |
For information on RabbitMQ ports, see "Networking" on the RabbitMQ documentation. For more information on Consul's required ports, see "Ports" in the Consul documentation on the HashiCorp website.
Example: Default firewalld settings for an unprivileged cluster
Here is an example of the default settings for firewalld when is deployed as an unprivileged cluster. Splunk Connected experiences apps access is not enabled in this example.
[phantom@phantom ~]$ sudo firewall-cmd --list-all public (active) target: default icmp-block-inversion: no interfaces: ens160 sources: services: dhcpv6-client http https ssh ports: 8443/tcp 27100-27200/tcp 5121/tcp 8300/tcp 8301/tcp 8302/tcp 4369/tcp 5671/tcp 25672/tcp 15672/tcp 443/tcp protocols: masquerade: no forward-ports: port=443:proto=tcp:toport=8443:toaddr= source-ports: icmp-blocks: rich rules:
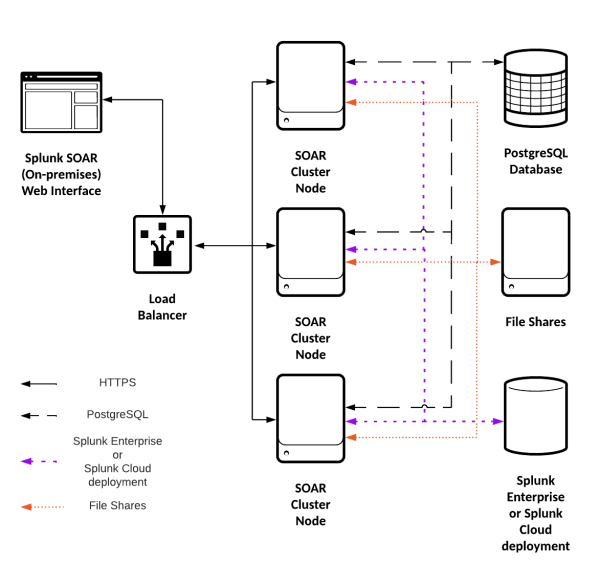
Example: cluster
A cluster consists of a load balancer, three or more nodes, a PostgreSQL database, file shares, and either a Splunk Enterprise or Splunk Cloud deployment.
This diagram shows an example of a cluster, with the connections marked.
| System requirements for production use | FIPS compliance |
This documentation applies to the following versions of Splunk® SOAR (On-premises): 6.2.1
 Download manual
Download manual
Feedback submitted, thanks!