Manage Splunk Cloud Platform indexes
Splunk Cloud Platform administrators create indexes to organize data, apply role-based access permissions to indexes that contain relevant user data, fine-tune data, specify how long to retain data in indexes, and so on.
Indexes store the data you have sent to your Splunk Cloud Platform deployment. To manage indexes, Splunk Cloud Platform administrators can perform these tasks:
- Create, update, delete, and view properties of indexes.
- Monitor the size of data in the indexes to remain within the limits of a data plan or to identify a need to increase the data plan.
- Modify data retention settings for individual indexes to control when Splunk Cloud Platform automatically deletes data or moves it to storage.
- Optimize search performance by managing the number of indexes and the data sources that are stored in specific indexes.
- Delete indexes. Caution: This function deletes all data from an index and removes the index. The operation is final and can't be reversed.
- Move expired data from indexes to self storage or a Splunk-supported archive (Dynamic Data Active Archive). Data from the index is not deleted until it is successfully moved to the storage location. Archived data can be restored to Splunk Cloud Platform for searching. Data from a self storage location can no longer be searched from Splunk Cloud Platform. However, it can be restored to a Splunk Enterprise instance for searching if necessary.
Event indexes and metrics indexes
You can create two types of indexes:
- Events indexes, for event-based log data. Events indexes impose minimal structure and can accommodate any kind of data, including metrics data.
- Metrics indexes, for metric data points. Metrics indexes use a highly structured format to handle the higher volume and lower latency demands associated with metrics data. Putting metrics data into metrics indexes results in faster performance and less use of index storage, compared to putting the same data into events indexes.
Events indexes are the default index type. To create events indexes, see Create a Splunk Cloud Platform events index.
To create metrics indexes, see Create a Splunk Cloud Platform metrics index.
For more information about the metrics data format see Metrics.
Best practices for creating indexes
Consider these best practices when creating indexes:
- Create separate indexes for long-term and short-term data. For example, you might need to keep security logs for one year but web access logs for only one month. Using separate indexes, you can set different data retention times for each type of data.
- Apply logical or role-based boundaries for indexes. For example, create separate indexes for different departments.
- Devise a naming convention to easily track, navigate, and organize indexes.
- To configure your data retention settings, see the best practice listed here: Manage Data Retention Settings.
The Indexes page
To view the Indexes page, select Settings > Indexes. The Indexes page lists the indexes in a Splunk Cloud Platform deployment and lets administrators create, update, delete, and modify the properties of indexes. To modify settings for an index, click its name.
From this page you can:
- Create an index.
- View index details such as the following.
- Index name: The name specified when the index was created.
- Index type: Whether the index is an events index or a metrics index.
- App: The app to which the index belongs.
- Current size: The approximate amount of uncompressed raw data currently stored in the index.
- Max size: The maximum amount of uncompressed raw data (in TB, GB, or MB) that can be retained in the index.
- Event count: The number of events in the index.
- Earliest event: The time of the earliest event found in the index.
- Latest event: The time of the most recent event found in the index.
- Searchable Retention: The maximum age of events retained in the index.
- Storage Type: The storage settings for expired data from a given index. Can be self storage, archive, or no additional storage.
- Status: Enabled or disabled. Data in a disabled index is ignored in searches.
- Delete an index. Caution: Deletes all data from an index and removes the index. The operation is final and can't be reversed.
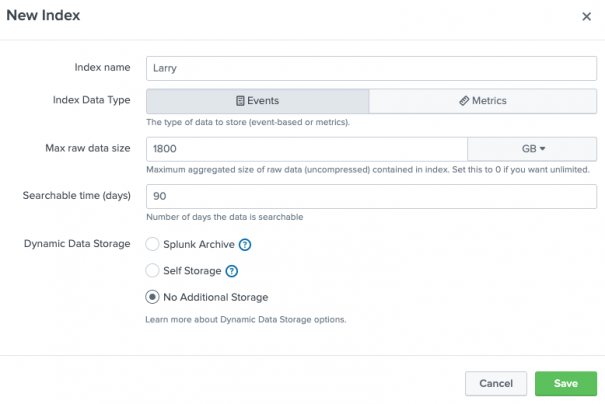
Create a Splunk Cloud Platform events index
To create an events index:
- Select Settings > Indexes.
- Click New Index
- In the Index name field, specify a unique name for the index. Index names can contain only lowercase letters, numbers, underscores, or hyphens. They must begin with a lowercase letter or number.
- Set Index Data Type to Events.
- In the Max raw data size field, specify the maximum amount of raw data allowed before data is removed from the index. Set this value to zero to specify an unlimited maximum raw data size. This is a data retention setting.
- In the Searchable time (days) field, specify the number of days before an event is removed from an index. This is a data retention setting.
- In the Dynamic Data Storage field, select Splunk Archive to send data to the Splunk Dynamic Data Active Archive, or choose Self Storage to move expired data to your own self-storage area. If you don't want to maintain expired Splunk data, leave No additional storage selected.
- If you enabled data self storage, select a location for data self storage. Or, click Edit self storage locations to add a new self storage location. For more information about data self storage and instructions for configuring a data self storage location, see Manage your Indexes and Data in Splunk Cloud.
- If you enabled Dynamic Data Active Archive, configure retention settings for the archive. For more information, see Archive expired Splunk Cloud Platform data.
- Click Save.
- Required step for Classic Experience customers: If this new index must be available to data collection apps on your IDM, contact Splunk Support and request they sync the index with your IDM. This ensures communication between the new index and any data collection apps running on the IDM. If you have a support contract, log in and file a new case using the Splunk Support Portal. Otherwise, contact Splunk Customer Support.
The events index appears after you refresh the page. Retention settings are applied to individual indexes, and data retention policy settings apply to all of the data that is stored in your Splunk Cloud deployment. Monitor and verify that the data retention settings for all indexes do not meet or exceed the values set in the data retention policy. For more information, see Data retention.
Create a Splunk Cloud Platform metrics index
To create an metrics index:
- Select Settings > Indexes.
- Click New Index
- In the Index name field, specify a unique name for the index. Names must begin with a lowercase letter or a number and can include uppercase letters, hyphens, and underscores.
- Set Index Data Type to Metrics.
- (Optional) Set Timestamp Resolution to Milliseconds if you want the metrics index to store metric data points at that increased level of granularity. Metrics indexes with millisecond timestamp resolution have decreased search performance. See Metrics indexes with millisecond timestamps.
- In the Max raw data size field, specify the maximum amount of raw data allowed before data is removed from the index. Set this value to zero to specify an unlimited maximum raw data size. This is a data retention setting.
- In the Searchable time (days) field, specify the number of days before an event is removed from an index. This is a data retention setting.
- In the Dynamic Data Storage field, select Splunk Archive to send data to the Splunk Dynamic Data Active Archive, or choose Self Storage to move expired data to your own self-storage area. If you don't want to maintain expired Splunk data, leave No additional storage selected.
- If you enabled data self storage, select a location for data self storage. Or, click Edit self storage locations to add a new self storage location. For more information about data self storage and instructions for configuring a data self storage location, see Manage your Indexes and Data in Splunk Cloud.
- If you enabled Dynamic Data Active Archive, configure retention settings for the archive. For more information, see Archive expired Splunk Cloud Platform data.
- Click Save.
- Required step for Classic Experience customers: If this new index must be available to data collection apps on your IDM, contact Splunk Support and request they sync the index with your IDM. This ensures communication between the new index and any data collection apps running on the IDM. If you have a support contract, log in and file a new case using the Splunk Support Portal. Otherwise, contact Splunk Customer Support.
The metrics index appears after you refresh the page. Retention settings are applied to individual indexes, and data retention policy settings apply to all of the data that is stored in your Splunk Cloud deployment. Monitor and verify that the data retention settings for all indexes does not meet or exceed the values set in the data retention policy. For more information, see Data retention.
Metrics indexes with millisecond timestamps
By default, metrics indexes are only searchable at a second-by-second precision. This is unlike events indexes, which can be searched with subsecond precision by default.
If you are dealing with a high volume source of metric data, such as a utility grid that has the potential to generate millions of metric data points per second, this means that the metric index is populated with sample metric data points or metric data points that are aggregated views of the raw metric data, taken at regular intervals.
If you are concerned about high index volume, this can be a good thing. Having second precision metrics indexes keeps your indexes lean and saves you from having to search through huge numbers of events over relatively short time ranges. But this also means that you cannot cannot run time-based metrics searches that have subsecond precision. Similarly, you cannot set up mstats searches that group by subsecond span values.
If you need the capability to perform metric searches with subsecond precision, give your new metric index a Timestamp Resolution of Milliseconds. Metrics indexes with millisecond timestamp resolution can have decreased search performance in comparison to metrics indexes that have the default second timestamp precision.
Metrics indexes set to millisecond precision might incur more license usage than similar metrics indexes set to second precision. The license cost per metric data point remains the same, but millisecond-precision indexes can index more data points than second-precision indexes ingesting data from the same source.
About changing timestamp resolutions of metrics indexes
You can change the timestamp resolution of a metrics index after you create it. However, if you change the timestamp resolution of a metrics index from millisecond to second, it may look like data loss to people who regularly run searches against that metrics index. This is because the index won't ingest data at millisecond resolution after the change.
When your index is at millisecond timestamp resolution, your indexed metric data points might have timestamps like this.
| _timestamp (seconds) |
|---|
| 1.000 |
| 1.001 |
| 1.002 |
| 2.000 |
| 2.435 |
| 3.123 |
| 3.651 |
| 4.000 |
After four seconds, if you change the timestamp resolution from millisecond timestamp resolution to second timestamp resolution, your index is restricted to indexing one metric data point per second:
| _timestamp (seconds) |
|---|
| 5.000 |
| 6.000 |
| 7.000 |
| 8.000 |
| 9.000 |
Some users may perceive this as a data loss when in fact they are just seeing their data with a less granular timestamp resolution.
Similarly, users of a metrics index that is switched from a second timestamp resolution to a millisecond timestamp resolution may be surprised to see their indexes ingesting more events than they did before the switch.
As an administrator of a Splunk Cloud Platform deployment it is up to you to communicate this change and its implications to your users.
Review Splunk Cloud Platform data policies
Splunk Cloud Platform administers your data according to the policies described in the following sections.
Data ingestion and daily license usage
Splunk Cloud Platform administers your data based on your subscription type. For more information, see Data policies in the "Subscription types" section of the Splunk Cloud Platform Service Description.
Data backup policy
Splunk Cloud continuously maintains and monitors your deployment. For more information, see the "Ensures Splunk Cloud Platform uptime and security" section of Splunk maintenance responsibilities in the Splunk Cloud Platform Service Description.
Data retention
When you send data to Splunk Cloud Platform, it is stored in indexes. Splunk Cloud Platform retains data based on index settings that enable you to specify when data is to be deleted or moved to self storage. To configure different data retention settings for different sources of data, store the data in separate indexes according to the desired retention policy.
You can configure the number of days for data to be searchable by configuring the Searchable time (days) setting for an individual index. For more information, see Manage data retention settings.
Index data is stored in directories called buckets. Data is deleted by deleting entire buckets, not individual events. When the maximum age or size of the Index is reached, buckets are deleted or moved starting with the oldest buckets first. Buckets are removed until the index no longer exceeds the configured limit. If you use data self storage or archiving, buckets are not deleted until the data is successfully moved to your self storage or archive location.
Data retention is based on your subscription type. For more details about data retention policies, see the Storage section of the Splunk Cloud Platform Service Description.
Manage data retention settings
Each index uses two settings on the New Index page to determine when to delete data:
- The maximum size of the raw index data (MB, GB, or TB, specified in the Max raw data size field)
- The maximum age of events in the index (specified in the Searchable time (days) field)
When the index reaches the specified maximum size or events reach the specified maximum age, the oldest data is deleted or is moved to your self-storage location (depending on your configuration).
For example, the system ingests data from a particular datasource at an approximate rate of 10 GB per day, and you want to retain and search against the last 90 days worth of data. This would cause the system to normally ingest approximately 900 GB over the configured 90 day searchable time period.
Based on your search and data retention requirements, set these values so that the Searchable time (days) value is reached before the Max raw data size threshold is reached. A best practice is to set the maximum raw data size to a significantly larger value than the normal total ingestion amount. Doing this allows for unanticipated bursts of data that might otherwise cause the system to start deleting data before reaching the desired retention limit.
Given the above parameters, you might configure the retention settings as follows:
- Max raw data size set to 1800 GB (double the example 900 GB normal total ingestion amount)
- Searchable time (days) set to 90
These values together account for both your ingestion rate and the time you want to retain the data. You need to consider these factors for each index that you create.
The new data retention settings appear after you click Save and refresh the page.
Check your data retention in the Cloud Monitoring Console to ensure you estimated your ingestion rate correctly and your storage consumption is within your entitlement. If you did not correctly estimate your ingestion rate, you might have a shorter retention period than expected.
Splunk Cloud Platform administrators can specify the settings that determine when data is removed from a specific index. For more information, see the following:
- Store expired Splunk Cloud Platform data for information about data self storage and instructions for configuring a data self storage location.
- Archive expired Splunk Cloud Platform data for information about archiving data.
Splunk Cloud Platform includes several internal indexes that are named starting with an underscore (_). The data retention period for these internal indexes cannot be modified.
Delete index data and the index from Splunk Cloud Platform
Splunk Cloud Platform administrators can delete an index.
This function deletes all data from an index and removes the index. The operation is final and can't be reversed.
- Select Settings > Indexes.
- Identify the index and click Delete from the Action column.
- Click OK to confirm that you want to delete the data and index from Splunk Cloud Platform.
The data and index are deleted from Splunk Cloud and can't be restored.
You can't delete default indexes and third-party indexes from the Indexes page.
| Optimize indexing and search processes | Store expired Splunk Cloud Platform data in your private archive |
This documentation applies to the following versions of Splunk Cloud Platform™: 8.2.2112, 8.2.2201, 8.2.2202, 8.2.2203, 9.0.2205, 9.0.2208, 9.0.2209, 9.0.2303, 9.0.2305, 9.1.2308, 9.1.2312, 9.2.2403, 9.2.2406, 9.3.2408 (latest FedRAMP release), 9.3.2411
 Download manual
Download manual
Feedback submitted, thanks!