Distributed Forwarder Management
Distributed Forwarder Management lets you create groups of stream forwarders with different stream capture configurations. You can use this feature to apply a specific configuration to multiple stream forwarders that have the same roles. Examples of this include streams with the same server types (such as Linux or Windows OS) or network connection points.
Distributed Forwarder Management is useful in a large scale enterprise deployments that can include hundreds or thousands of stream forwarders.
Create a stream forwarder group
To create a Stream forwarder group you:
- Specify a regex rule that matches host servers
- Define HTTP event collector endpoints (URLs)
- Select stream protocol capture for the group
You can group stream forwarders using the default Forwarder IDs, which are the hostname by default, or you can specify custom Forwarder IDs to create new logical groups.
- Click Distributed Forwarder Management.
The Distributed Forwarder Management page displays your existing Stream forwarder groups. If you have not defined a Stream forwarder group, this page displays the default group, which is configured to capture all Stream protocols. - Click Create New Group.
- Enter a name and description for the group.
- Click Yes if you want the group to Include Ephemeral Streams in addition to selected permanent streams.
- Click On to enable HTTP Event Collector AutoConfig. This provides automated configuration of indexer endpoint URLs for any deployment architecture.
- Click Next.
- When HTTP Event Collector Autoconfig is on,
splunk_app_streamautomatically sends all configuration data to Stream forwarders, including endpoint URLs for all indexers (8 max). You do not need to configure data forwarding to indexers fromstreamfwd. - When HTTP Event Collector Autoconfig is off, manually enter the endpoint URL of each indexer for each forwarder group definition. The matching forwarder group receives the configuration from
Splunk_app_ streamand then sends the captured data to the specified indexers. - Enter a regex rule. For example:
sr-centos*.* - Click Next.
- In the Select/De-select Stream in Forwarder Group dialog, select the protocols that you want this group of Stream forwarders to capture.
- Click Finish.
Your new stream forwarder group appears on the Distributed Forwarder Management page.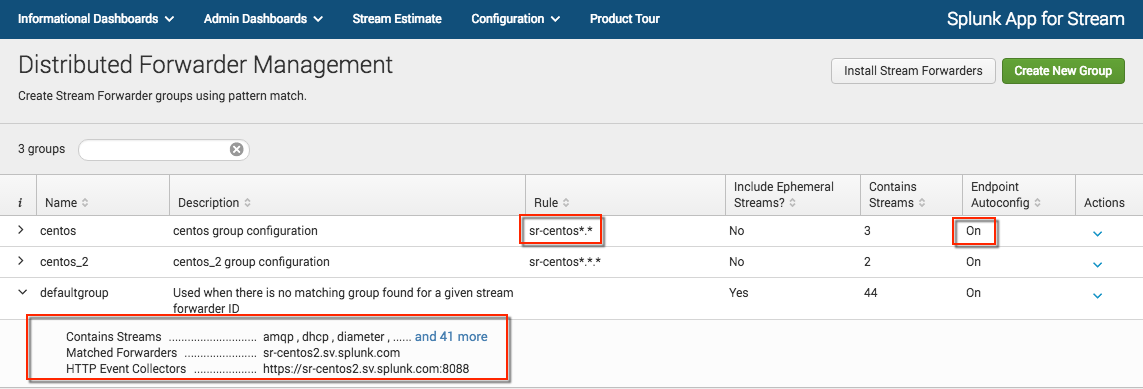
You can change the default Forwarder ID, which is the hostname by default, to create a new Forwarder ID. This lets you organize your stream forwarders into new logical groupings based on the Forwarder ID.
A list of Forwarder IDs that match the regex rule appears in the dialog.
Enable HTTP event collector to send data to indexers
- Go to Configuration > Distributed Forwarder Management.
- Click Install Stream Forwarders.
- If the Install Stream Forwarders modal shows that HTTP Event Collector streamfwd token configuration is disabled, click View Configuration.
- Click Global Settings.
- Click Enabled to enable streamfwd.
- Make sure HTTP Port Number is set to 8088.
- Click Save.
To learn how to configure HTTP Event Collector in an indexer cluster environment, see Propagate HTTP Event Cluster configuration to indexer cluster in the Splunk Stream Installation and Configuration Manual.
Distributed Forwarder Management examples
The following examples describe the different ways you can manage your streams using the Distributed Forwarder
Manage by hostname
If the existing hosts on which you install the Stream forwarder: Splunk_TA_stream, use a naming convention. You can then create a regex rule that matches the naming convention to define a Stream forwarder group.
For example, if your hosts use the naming convention my.server.01, my.server.02, my.server.03, and so on, you could use the regex *.server.* to define your Stream forwarder group.
Manage by Forwarder ID
Each Stream forwarder instance has its own Forwarder ID. You can change the Forwarder ID from its default hostname value and specify a new Forwarder ID. This lets you create your own naming conventions and organize your stream forwarders into new logical groupings based on Forwarder ID.
You can specify the Forwarder ID using Splunk Web or from the command line using configuration files.
Specify a Forwarder ID using Splunk Web
- In Splunk Web, go to Settings > Data Input > Wire Data.
- Click on the name of the input for the Stream forwarder.
- In the Stream Forward Identifier field, enter a string for the Forwarder ID.
- Click Save.
The string that you specify becomes the new Forwarder ID for the Stream forwarder.
Note: When you specify the Forwarder ID using Splunk Web, perform the configuration on the search head that hosts Splunk Stream. The new Forwarder ID is propagated to the corresponding Stream forwarder.
Specify a forwarder ID using configuration files
- Navigate to
$SPLUNK_HOME/etc/apps/Splunk_TA_stream/local/inputs.conf - In the
[streamfwd://streamfwd]stanza, enter a new value forstream_forwarder_id:[streamfwd://streamfwd] splunk_stream_app_location = https://localhost:8000/en-us/custom/splunk_app_stream/ stream_forwarder_id = <Forwarder_ID> disabled = 0
Note: When you specify the Forwarder ID using configuration files, you must perform the configuration on the forwarder that hosts Splunk_TA_stream.
| Use Global IP filters | Use Stream Estimate to preview index volume |
This documentation applies to the following versions of Splunk Stream™: 7.3.0, 7.4.0, 8.0.0
 Download manual
Download manual
Feedback submitted, thanks!