Solution architecture
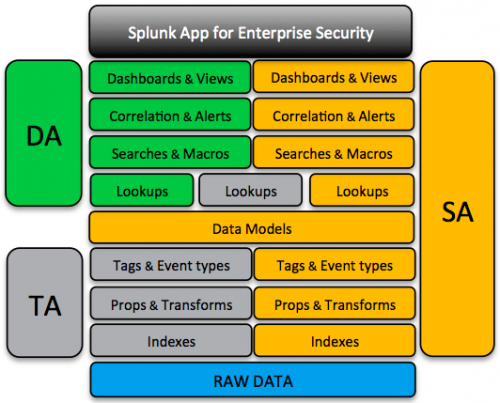
The Splunk App for Enterprise Security is comprised of a group of apps that combine to provide dashboards, searches, and tools to summarize the security status of the enterprise.
- Domain Add-on (DA) provide views into the security domain. The DA contains search knowledge for investigation and summarization of security-relevant data.
- Supporting Add-on (SA) provide an intermediary knowledge and normalization layer used by the DA. The SA provides the Common Information Model (CIM) normalization and uses the data collected there.
- Technology Add-on (TA, or just add-ons) are responsible for formatting incoming data for use in ES and the CIM.
You must install and configure all add-on layers for the Enterprise Security app to function.
Splunk App for Enterprise Security
The Splunk App for Enterprise Security provides high-level aggregate views for all security domains and functionality that summarizes the information into a single visual reference. The Enterprise Security app inherits the knowledge objects provided through the DA, SA, and TA layers during the setup process.
Domain add-on
A DA provide dashboards, views, and searches that provide visibility into the primary domains of security:
- Access protection
- Endpoint protection
- Network protection
- Threat Intelligence
Each domain includes summary dashboards that give an overview of security metrics, along with search views to drill down to more detailed information. These views act as interactive starting points to investigate and explore the data to discover abnormal behavior.
Supporting add-on
An SA provide the intermediary knowledge and normalization layer used by the DA. The SA layer is responsible for the schemas used to map data sources into the Common Information Model for analysis through data models. They also host the information about assets and identities along with the searches to correlate that data and provide alerts and other events to the domains.
- Access Protection
- Audit and Data protection
- Endpoint Protection
- Identity Management
- Network Protection
Technology add-on
A TA provides a layer of abstraction that forms the link between data from specific technologies such as McAfee data or Juniper firewall logs and the higher-level configurations in the Enterprise Security app. They also contain search-time knowledge mappings that assign fields and tags to the data to be used by the higher-level search layer.
The TA layer is critical during the planning and installation phase of the Enterprise Security app.
- Test TA's against the source data to confirm that the extraction are functioning properly.
- You might need to deploy the TA's to indexers if index-time modifications are required.
- You can deploy the TA's to forwarders, depending on the data source and network architecture.
For a list of the add-ons included with the Enterprise Secuirty app, see "Add-ons provided with Enterprise Security" in this manual.
Knowledge objects
The Splunk App for Enterprise Security uses the knowledge objects layers provided in Splunk Enterprise.
| Knowledge object | Description | Used in the Enterprise Security app |
|---|---|---|
| Tags | A tag is an abstraction of one or more field values. Use with event types. | The combination of tags and event types is used in add-ons to facilitate data mappings. |
| Event types | A type of search to categorize and label a group of matching events. Use with tags. | The combination of tags and event types is used in add-ons to facilitate data mappings. |
| Data Models | A hierarchically structured collection of fields. | Required for CIM. Use data models for searching and populating dashboards. |
| KV Store | A structured data source that stores data as key-value pairs in collections | Used to store notable event statuses. |
| Lookups | A tabular structured data source. | Use with assets and identities, and to normalize common data fields. |
| Macros | A type of search that is designed for reuse. | Macros allow for fast search modification through the reuse of common search strings. |
| Swim lane search | A search output with a specific visualization | A visual indicator that displays event density over time. |
| Key security indicator | A search output with a specific visualization | A visual indicator that relays information about a security performance metric. |
| Correlation searches | A type of search that looks across one or more data sources for defined patterns, and if a match is found creates an alert. | Use to generate notable events and risk scores. |
| Notable event | An alert type used to create an audited, tracked event. | Creates a stored event to be assigned, tracked, updated, and audited. |
| Risk score | An alert type used to create an risk modifier. | Creates a stored event that increments the risk score of an object. |
| Plan your data inputs | Install Add-ons |
This documentation applies to the following versions of Splunk® Enterprise Security: 3.3.0, 3.3.1, 3.3.2, 3.3.3
 Download manual
Download manual
Feedback submitted, thanks!