Manage Analytic Stories through the use case library in Splunk Enterprise Security
The Splunk Security Research team writes Analytic Stories that provide actionable guidance for detecting, analyzing, and addressing security threats. An Analytic Story contains the searches you need to implement the story in your own Splunk Enterprise Security (ES) environment. It also provides an explanation of what the search achieves and how to convert a search into adaptive response actions, where appropriate.
The Splunk Enterprise Security Content Update (ESCU) delivers Analytic Stories to customers as part of a content service through splunkbase. Analytic Stories give you advice on how to use Splunk ES to investigate and take action on new threats that Splunk ES detects in your environment.
The ESCU Analytic Story content is available directly in Splunk ES through the use case library. If you do not have ESCU installed, you will see some Analytic Stories by default as well as a message prompting you to download and install the ESCU add-on for access to common security Analytic Stories. When new Analytic Stories are published in newer versions of ESCU, you need to upgrade the ESCU add-on to get the new content.
Prerequisites for using the use case library include the following:
- Data is ingested via your forwarders and technical add-ons.
- The CIM add-on is installed.
- (Optional) The ESCU add-on is installed so you can access more Analytic Stories.
You can explore, activate, bookmark, and configure common searches in the use case library.
Determine which Analytic Stories to configure
You can use common industry use cases to determine which Analytic Stories and searches are useful to you. There are a variety of ways to determine if an Analytic Story contains the searches you need:
- by industry use case
- by framework
- by data
In the following scenario, you know that you're interested in common AWS-related security issues, so you start by filtering on known use cases for cloud security.
- From the Splunk ES menu bar, select Configure > Content > Use Case Library.
- From the use cases filters on the left, click Cloud Security.
- From an Analytic Story, such as Suspicious AWS EC2 Activities, click the greater than ( >) symbol to expand the display.
- You see the detection searches that are related to this use case.
- You also see your data sources, data models, and lookups that these searches use.
Data Sources Description Recommended Data Sources The type of data sources that are likely to provide valuable data. Sourcetypes Your sourcetypes that are in use by the detection searches for this Analytic Story. If the status icon shows a red exclamation mark, hover over the icon to see the reason. Data Models Your data that is in use by the detection searches for this Analytic Story as mapped to the Splunk data models via the CIM add-on. If the status icon shows a red exclamation mark, hover over the icon to see the reason. Lookups Your lookups that are in use by the detection searches for this Analytic Story. If the status icon shows a red exclamation mark, hover over the icon to see the reason. - Click the name of the Analytic Story. In this case, click Suspicious AWS EC2 Activities.
The Analytic Story Details page opens for the story. - You see the searches related to the stages of detecting, investigating, assessing, and mitigating issues.
- From the Detection section, select a search, such as ESCU - EC2 Instance Started In Previously Unseen Region.
- From the Search section, click the greater than (>) symbol to expand the display.
- Revise the time picker and click Search.
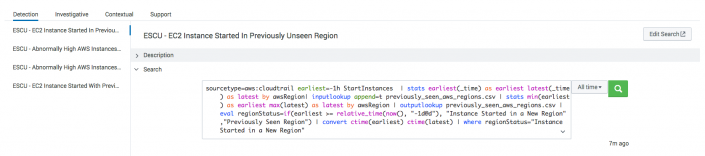
- From the How to Implement section, click the greater than (>) symbol to expand the display for tips on implementation.
- From the Known False Positives section, click the greater than (>) symbol to expand the display for tips on when the results might not indicate a problem.
If you want to run this search automatically on a regular basis, see Enable and schedule the Analytic Story.
Enable and schedule the Analytic Story
Once you determine that an Analytic Story will help you detect, investigate, assess, or mitigate an issue, you can enable and schedule it. An Analytic Story is considered "in use" when at least one search is enabled and scheduled. By default, all stories are disabled. If a search is enabled but not scheduled, or if it is run manually, then it is not considered in use.
- From the Splunk ES menu bar, select Configure > Content > Use Case Library.
- From the event information column on the Analytic Story of interest, click the greater than ( >) symbol to expand the display.
- Under Detection Searches, copy the name of an ESCU detection search that you want to enable.
- From the Splunk ES menu bar, select Configure > Content > Content Management.
- In the search filter, paste the name of the ESCU detection search that you previously copied and search for it.
- From the Actions column, click Enable.
- To edit the correlation search schedule, click the name of the search.
- Edit the schedule and click Save.
To modify correlation searches in your environment, see Create correlation searches in Splunk Enterprise Security.
Configure the library
You can revise how the preconfigured use case library displays your most frequently used Analytic Stories and searches.
The use case library does not require any special capability to view Analytic Stories, but it does require the edit_analyticstories capability to edit and add them. By default, ES assigns the edit_analyticstories capability to the ess_admin and ess_analyst roles. An admin can assign other roles from the Permissions setting.
Edit or add Analytic Story details
To edit the displayed descriptions, narratives, references, or searches:
- From the Splunk ES menu bar, select Configure > Content > Use Case Library.
- From the use case library, click the name of an Analytic Story to see the Analytic Story Details page, which contains all the default information that is provided by the ESCU content.
- From the top-right of the Analytic Story Details page, click Edit.
- A new browser window opens so you can change the story descriptions, narratives, or references to fit your specific usage. These changes are global, not per user, so everyone sees the same updates.
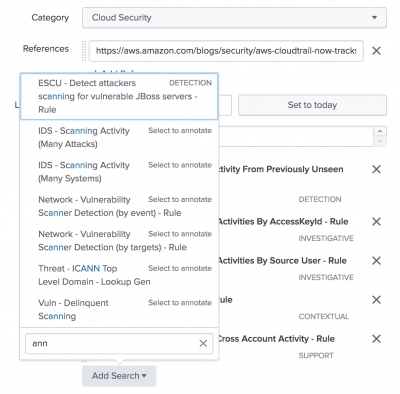
- You can also add existing searches that do not display by default in this Analytic Story.
- Scroll to the Searches section.
- Click Add Search.
- Select the search to include in this story.
- Click Save.
Search types
When you add a search in the Edit Analytic Stories window, the type of search appears to the right of the search name. By default you will see detection, investigative, contextual, support, or select to annotate.
Only annotated searches are associated with an Analytic Story. When you add an annotated search, the search is immediately added to the Analytic Story. In those added searches, you can click Edit Search to revise the annotations of that search.
If the search is not annotated, do the following to annotate it:
- From the right side of the search name, click Select to annotate.
- In the annotation editor, type the name of an existing search type or type the name a new search type in the Type field. This is the only mandatory field.
- (Optional) If you want analysts to see information when deciding which stories and searches to use, fill in information for Description, How to Implement, Known False Positives, Providing Technologies (also known as data sources or technology add-ons).
- (Optional) In the Annotations field, click Add row to add Framework names and their Mapping categories. These are free-form fields. You can use them for either industry-standard frameworks, such as National Institute of Standards and Technology issues for detecting and continuous monitoring of vulnerabilities (NIST + DE.CM), or you can use them for frameworks of your own.
You can find these later from the Framework Mapping filter.- From the Splunk ES menu bar, select Configure > Content > Use Case Library.
- From the drop-down filters, click Framework Mapping.
- Type the name of a Framework or scroll to find it.
- Click the check box to select a Framework. The filter is using OR logic, so the more check boxes you select, the more results you will see.
The savedsearches.conf file is used to annotate existing saved searches.
Create an Analytic Story
You can create your own Analytic Story and map it to the searches of your choice.
The use case library does not require any special capability to view Analytic Stories, but requires the edit_analyticstories capability to edit and create new ones. By default, ES assigns the edit_analyticstories capability to the ess_admin and ess_analyst roles. An admin can assign it to other roles from the Permissions setting.
- From the Splunk ES menu bar, select Configure > Content > Content Management.
- Click Create New Content > Analytic Story.
- Fill in the required fields to create your analytics story.
- Scroll down to the Searches field.
- From the Add Search drop-down menu, you can select any of the searches that have been annotated.
- Click Save.
Install Analytic Stories from other apps
While ESCU content is imported automatically, you can also import Analytic Stories from apps other than ESCU into the use case library.
Install the app to see the Analytic Stories in the use case library.
- Install the app onto the same search head as Splunk ES.
- Export the app to other apps or globally.
- Review the new knowledge objects. If the Analytic Stories are visible in the use case library, the export is successful.
- Use the new Analytic Stories.
If you do not see the new Analytic Stories in the use case library, it's because of one of the following reasons:
- Make sure that the app is being exported globally. See Make Splunk knowledge objects globally available in the Splunk Enterprise Admin Manual.
- If the app does not contain compatible use cases, it does not contain an
analyticstories.conffile.
See also
Use Analytic Stories for actionable guidance in Splunk Enterprise Security in the Use Splunk Enterprise Security manual.
| Expand Content Management searches to view dependency and usage information in Splunk Enterprise Security | Configure general settings for Splunk Enterprise Security |
This documentation applies to the following versions of Splunk® Enterprise Security: 6.0.0, 6.0.1, 6.0.2, 6.1.0, 6.1.1, 6.2.0, 6.3.0 Cloud only, 6.4.0, 6.4.1, 6.5.0 Cloud only, 6.5.1 Cloud only, 6.6.0, 6.6.2
 Download manual
Download manual
Feedback submitted, thanks!