Key indicators in Splunk Enterprise Security
Splunk Enterprise Security includes predefined key indicators that identify key security metrics for the security domains covered by Splunk Enterprise Security. You can view the key indicators on dashboards in Splunk Enterprise Security.
Key indicators provide a visual reference for several security metrics. Key indicator searches populate the security metrics of key indicators.The key indicator searches run against the data models defined in Enterprise Security, or the data models defined in the Common Information Model app. Some key indicator searches run against the count of notable events.
Interpreting key indicators on dashboards
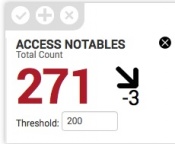
On dashboards, each key indicator includes a value indicator, a trend amount, a trend indicator, and a threshold value used to indicate the importance or priority of the indicator. The key indicator searches default to running over a relative time span of 48 hours.
| Field | Description |
|---|---|
| Description | Brief description of the security-related metrics:
|
| Value indicator | Current count of events. If a threshold is set, the numbers will change color as they cross thresholds. Click the value indicator to drill down into the key indicator search and view the raw events. If the value indicator is wrong, such as a percentage value greater than 100%, there could be missing or wrong data in the data model dataset used by the key indicator search to calculate a value. |
| Trend amount | Displays the change in event count over the time period defined in the key indicator search. |
| Trend indicator | Displays a directional arrow to indicate the direction of the trend. The arrow changes color and direction over time. |
Edit key indicators on dashboards
Enterprise Security includes preconfigured key indicators. Each dashboard key indicator row includes an editor that allows simple, visual changes to be made directly to the key indicators without leaving the dashboard. You can make changes to the search generating the key indicator on the Content Management dashboard. See Edit a key indicator search in Administer Splunk Enterprise Security.
- Click the Edit pencil icon to the top left of the indicator bar. The editing tools display above the indicators.
- Drag and drop the indicators to rearrange them. There can be 5 indicators per row, and multiple indicator rows.
- Click the checkmark icon to save.
Remove key indicators from a dashboard
Remove a key indicator from a dashboard.
- Click the Edit pencil icon to the top left of the indicator bar. The editing tools display above the indicators.

- Click the X to the top right of the indicator.
- Click the checkmark icon to save.
Removing the indicator from a dashboard does not remove the key indicator from Enterprise Security.
Add key indicators to a dashboard
Add key indicators to a dashboard.
- Click the Edit pencil icon to the top left of the indicator bar. The editing tools display above the indicators.

- Click the plus icon to open the Add indicators panel.
- Click the checkmark icon to save.
Set a threshold for a key indicator on a dashboard
You can set a threshold for a key indicator on a dashboard to change the color of the key indicator. A threshold defines an acceptable value for the event count of an indicator. An event count above the threshold causes the key indicator to display as red, while an event count below the threshold causes the key indicator to display as green. If the threshold is undefined, the event count remains black.
| Customize Splunk Enterprise Security dashboards to fit your use case | Security Posture dashboard |
This documentation applies to the following versions of Splunk® Enterprise Security: 6.6.0, 6.6.2
 Download manual
Download manual
Feedback submitted, thanks!