Asset and Identity Investigator dashboards
The Asset and Identity Investigator dashboards visually aggregate security-related events over time using category-defined swim lanes. Each swim lane represents an event category, such as authentication, malware, or notable events. The swim lane uses a heat map to display periods of high and low activity. The color saturation on the swim lane corresponds to the event density for a given time. For example, high activity periods display a darker color. An analyst can visually link activity across the event categories and form a complete view of a host or user's interactions in the environment.
Asset Investigator
The Asset Investigator dashboard displays information about known or unknown assets across a pre-defined set of event categories, such as malware and notable events.
Use the Asset Investigator dashboard
You can use the Asset Investigator dashboard to triage an asset's interactions with the environment.
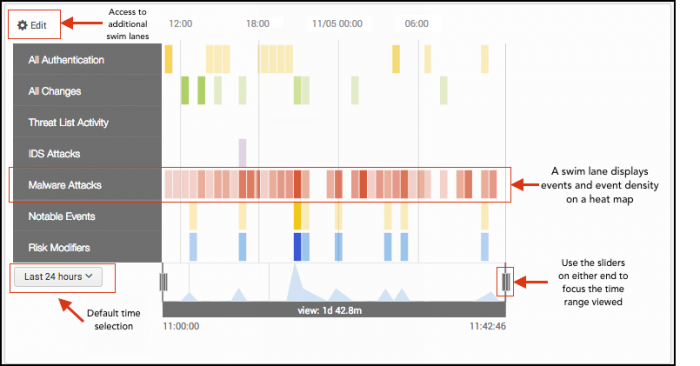
The dashboard contains multiple event categories, with each one represented by its own swim lane. Each event category contains relevant events that correspond to a data model. For example, the Malware Attacks swim lane displays events from an anti-virus management or other malware data source, limited to the asset searched. Multiple swim lanes are displayed at once to make it easier for you to track the actions of an asset across event categories.
Additionally, you can use this dashboard for ad hoc searching.
- Browse to Security Intelligence > User Intelligence > Asset Investigator.
- Type the host name or IP address in the search bar with an optional wildcard.
- Set a time range and click Search.
A workflow for asset investigation
To initiate the asset investigation workflow, perform a workflow action from any dashboard that displays events with network source or destination addresses.
- Look at the asset description at the top of the dashboard to confirm that you are viewing the asset you would like to investigate. All events displayed in the swim lanes are limited to the selected asset.
- Use the time range picker to narrow down the general time range you are interested in. Use the time sliders to isolate periods of interesting events or peak event counts.
- Add or change the swim lanes using the edit menu. For example, to display data collected on an asset from packet analysis tools, change the selected collection from Default to Protocol Intelligence, which represents packet capture data. See Edit the swim lanes.
- Review individual and grouped events. After selecting an event, you can use the Event Panel to examine common fields represented in the individual or grouped events.
- If there is an event or pattern that you want to share or investigate further, you can do this using the Event Panel.
- Click Go to Search to view a drilldown of the selected events.
- Click Share for a shortened link to the current view.
- Click Create Notable Event to open a dialog box to create an ad-hoc notable event. See Manually create a notable event in Splunk Enterprise Security in Administer Splunk Enterprise Security.
Data sources
The event categories in the Asset Investigator dashboard display events from a number of data models containing an asset or host field. In any given time selection, a selected asset may not have data to display in one or more event categories. When a data model search returns no matching events, the swim lane displays "Search returned no results." See Troubleshoot dashboards in Splunk Enterprise Security in Administer Splunk Enterprise Security.
Identity Investigator
The Identity Investigator dashboard displays information about known or unknown user identities across a predefined set of event categories, such as change analysis or malware.
Use the Identity Investigator dashboard
You can use the Identity Investigator dashboard to triage a user identity's interactions with the environment.

The dashboard contains multiple event categories, with each one represented by its own swim lane. Each event category contains relevant events that correspond to a data model. For example, the Malware Attacks swim lane displays events from an anti-virus management or other malware data source, limited to the user identity or credential searched. Multiple swim lanes are displayed at once to make it easier for you to track the actions of a user across event categories.
Additionally, you can use this dashboard for ad-hoc searching.
- Browse to Security Intelligence > User Intelligence > Identity Investigator.
- Type a user credential in the search bar. Optionally, include a wildcard.
- Set a time range and click Search.
A workflow for identity investigation
The identity investigation workflow is initiated through a workflow action from any dashboard that displays events with network source or destination address.
- Look at the identity description at the top of the dashboard to confirm that you are viewing the identity you would like to investigate. All events displayed in the swim lanes are limited to the selected identity.
- Use the time range picker to narrow down the general time range you are interested in. Use the time sliders to isolate periods of interesting events or peak event counts.
- Add or change swim lanes by using the edit menu. For example, to display identity information collected for user activity monitoring, change the selected collection from Default to User Activity. See Edit the swim lanes.
- Review individual and grouped events. After selecting an event, you can use the Event Panel to examine common fields represented in the individual or grouped events.
- If there is an event or pattern that you would like to share or investigate further, you can do this using the Event Panel.
- Click Go to Search to view a drilldown of the selected events.
- Click Share for a shortened link to the current view.
- Click Create Notable Event to open a dialog box to create an ad-hoc notable event. See Manually create a notable event in Splunk Enterprise Security in Administer Splunk Enterprise Security.
Data sources
The event categories in the Identity Investigator dashboard display events from a number of data models containing an identity or a user field. In any given time selection, an identity may not display data in one or more event categories. When a data model search returns no matching events, the swim lane displays "Search returned no results." See Troubleshoot dashboards in Splunk Enterprise Security in Administer Splunk Enterprise Security.
Edit the swim lanes
You can add or remove swim lanes from the Entity Investigator dashboards by opening the Edit Lanes customization menu. The Entity Investigator dashboards support the addition of custom swim lanes bundled with add-ons or created using ES Content Management. For more information, see Managing content in Splunk Enterprise Security in Administer Splunk Enterprise Security.
- Choose Edit at the top of the dashboard.
- Select the radio button for a Custom collection.
- Select a checkbox to add a swim lane to the dashboard.
- Deselect a checkbox to remove a swim lane from the dashboard.
- Click the color next to a swim lane to change it.
- Click the X to close the edit menu.
The order of swim lanes can be changed on the dashboard and does not require the Edit Lanes menu.
- Select a swim lane category.
- Drag and drop the swim lane where you would like it.
The Asset Investigator has additional, optional swim lanes in the collection Protocol intelligence to display data collected about an asset using packet analysis tools. The Identity Investigator has additional, optional swim lanes in the collection User Activity to display data collected about an identity for user activity monitoring.
| Swimlane Name | Asset or Identity dashboard | Description |
|---|---|---|
| All Authentication | Both | Matches events in the Authentication data model. |
| All Changes | Both | Matches events in the Change Analysis data model. |
| Threat List Activity | Both | Matches events in the Threat Lists data model. |
| IDS Attacks | Both | Matches events in the Intrusion Detection data model. |
| Malware Attacks | Both | Matches events in the Malware data model. |
| Notable Events | Both | Matches events in the Notable index. |
| Risk Modifiers | Both | Matches events in the Risk Analysis data model. |
| DNS Errors | Asset only | Matches events in the Network Resolution DNS data model. |
| Cloud Emails | Asset only | Matches events in the Email data model. |
| SSL Expired Certs | Asset only | Matches events in the Certificates data model. |
| HTTP Errors | Asset only | Matches events in the Web data model. |
| Non-corporate Emails | Identity only | Matches events in the Email data model. |
| Non-corporate Web Uploads | Identity only | Matches events in the Web data model. |
| Remote Access | Identity only | Matches events in the Authentication data model. |
| Ticket Activity | Identity only | Matches events in the Ticket Management data model. |
| Watchlisted Sites | Identity only | Matches events in the Web data model. |
Troubleshooting Asset and Identity Investigator dashboards
The Asset and Identity Investigator dashboards display events from the data model named in each swim lane. When a data model search returns no matching events, the swim lane displays "Search returned no results." See Troubleshoot dashboards in Splunk Enterprise Security in Administer Splunk Enterprise Security.
| Asset and Identity dashboards | User Activity Monitoring |
This documentation applies to the following versions of Splunk® Enterprise Security: 7.0.0
 Download manual
Download manual
Feedback submitted, thanks!