Assign risk scores to assets and identities
This is the first step in the Isolate threats with risk-based alerting scenario.
Using Splunk Enterprise Security, Ram assigns risk scores to the assets and identities in the network environment. The risk scores show the relative risk of a device or user in the network environment over time and creates an extra layer of security-enriched data. The risk scores help to exponentially increase the number of detections because they let Ram calculate the risk within the environment posed by small events over time.
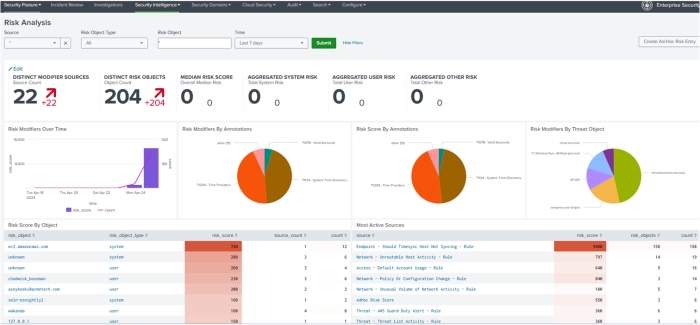
Ram now creates more meaningful and higher fidelity alerts, called risk notables, which increase visibility and reduce overall risk. The Risk Analysis dashboard displays these risk scores and other risk-related information. Enterprise Security indexes all risks as events in the risk index.
Ram can add risk scores to a user, a system, or an object in multiple ways:
- Using a custom correlation search
- Specifying risk as an adaptive response action from the Incident Review page
- Adding an ad hoc risk entry from the Risk Analysis dashboard
- Assigning risk through a search
Next step
Generate risk notables using risk incident rules
See also
For more information on assigning risk, see the product documentation:
Modify a risk score with a risk modifier
Configure adaptive response actions
Risk Analysis in the Use Splunk Enterprise Security manual.
| Isolate threats using risk-based alerting | Generate risk notables using risk incident rules |
This documentation applies to the following versions of Splunk® Enterprise Security: 7.3.2, 7.3.3
 Download manual
Download manual
Feedback submitted, thanks!