Enable behavioral analytics service on Splunk Enterprise Security
This topic applies only to customers on the Splunk Cloud platform.
Enable behavioral analytics service on Splunk Enterprise Security to leverage threat detections so that you can monitor cyber threats and enhance your security operations. Enabling behavioral analytics service on Splunk Enterprise Security allows you to ingest raw data from various supported source types and provision tenants automatically. Additionally, you can also forward notables, risk events, assets, and identity data from Splunk Enterprise Security to the behavioral analytics service.
Prerequisites to enable behavioral analytics service
Following is a list of prerequisites to enable behavioral analytics service with Splunk Enterprise Security:
- Splunk Cloud stack on 9.0.2209 or later in the US East (Virginia) region
- Splunk Enterprise Security version 7.1 or later
- You are a Splunk Enterprise Security customer from the US East (Virginia) AWS region
- You are a non-FedRamp customer
- Your data ingestion volume is less than 4 TB
The behavioral analytics service for Splunk Enterprise Security is not available to on-prem users.
Enable behavioral analytics service from Splunk Enterprise Security
Follow these steps to enable behavioral analytics service on Splunk Enterprise Security:
- Log in to the Splunk Enterprise Security app to display the option to enable the service.
- Select the checkbox to allow Splunk to enable token authentication, generate a token, and send data from Splunk Enterprise Security to behavioral analytics service.
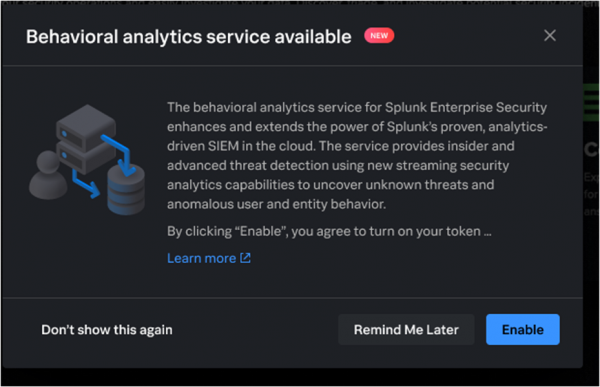
You must select the checkbox and allow Splunk to enable token authentication to proceed with enabling the service. If you choose to disable token authentication later, the behavioral analytics service is not disabled, and you can continue to use the service.
- Click Enable to enable the service.
Enabling the service might take 1-2 hours. The following notification is sent when the service is enabled.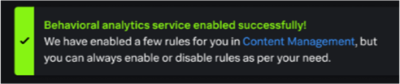
For more information on token authentication, see Enable or disable token authentication.
Alternatively, you can also enable the behavioral analytics service by following these steps:
- Navigate to Configure > General > General Settings.
- Scroll to the panel for Behavioral analytics service.
- Select the checkbox to allow Splunk to enable token authentication, generate a token, and send date from Splunk Enterprise Security to behavioral analytics service.
You must select the checkbox and allow Splunk to enable token authentication to proceed with enabling the service. Enabling tokens allow users with
sc_adminrole to make API calls to the Administrator Configuration Service (ACS) and use behavioral analytics with Splunk Enterprise Security. If you choose to disable token authentication later, the behavioral analytics service is not disabled, and you can continue to use the service. - Click Enable to enable the service.
Enabling the service might take 1-2 hours. The following notification is sent when the service is enabled.Behavioral analytics service enabled successfully.
Contact *Splunk Support Portal or your account team if you want to disable the behavioral analytics service. If you see errors while enabling the behavioral analytics service, retry enabling the service again. If you see errors while enabling behavioral analytics detection, retry enabling the detections. Contact Splunk Support if the errors persist.
Enable or disable behavioral analytics detections in Splunk Enterprise Security
If you are an eligible user, you can view all behavioral analytics detections on the Content Management page in Splunk Enterprise Security. You can also enable or disable individual detections, if required. You also have the option to manage behavioral analytics detections by forwarding notables to a test index without impacting the risk environment. For more information on using test index for detections, see Manage Behavioral Analytics Service detections in Splunk Enterprise Security.
Follow these steps to enable or disable detections:
- Navigate to the Content Management page (Configure > Content > Content management) in Splunk Enterprise Security to view all content.
- Filter the security content by Type Detection.
- Select the detections that you want to enable or disable from the list on the Content Management page.
- Click Enable or Disable.
You can also select detections in bulk and enable or disable them.
| Use behavioral analytics service with Splunk Enterprise Security 7.1.0 or higher | Overview of Incident Review in |
This documentation applies to the following versions of Splunk® Enterprise Security: 7.1.0, 7.1.1, 7.1.2
 Download manual
Download manual
Feedback submitted, thanks!