Add dispositions to risk notables
This is the first step in the Reduce alert volumes by triaging notables scenario.
Ram adds dispositions to the risk notables using the Incident Review dashboard to identify the threat level associated with the notable accurately. Adding a disposition helps to classify the notables, separate the false positives, and drill down on the notables that pose the highest threat. Taking this step helps Ram to accelerate the triage of notables during an investigation and respond to security threats faster.
- From the Splunk Enterprise Security menu bar, Ram selects the Incident Review page and reviews the table that lists the notables.
- Ram sorts the table to show only the risk notables and selects the check box beside the risk notables for which Ram wants to add a disposition.
- Ram selects Edit Selected to edit the notable that they selected.
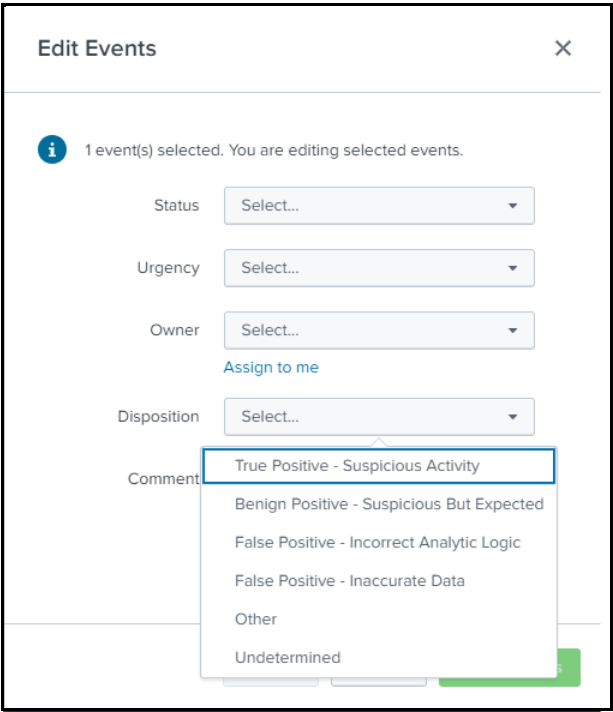
- For each risk notable, Ram selects one of the options from the Disposition list as shown in the following image and then saves the changes.
Now Ram needs to investigate only risk notables that get tagged as True Positive - Suspicious Activity.
Next step
See also
For more information on triaging notables using dispositions, see the product documentation:
Triage notables on Incident Review in Splunk Enterprise Security in the Use Splunk Enterprise Security manual.
| Reduce alert volumes by triaging notables | Sort notables by disposition |
This documentation applies to the following versions of Splunk® Enterprise Security: 7.3.2, 7.3.3
 Download manual
Download manual
Feedback submitted, thanks!