Deploy Cisco Talos Intelligence for Splunk Enterprise Security (Cloud Only)
Deploy Cisco Talos Intelligence for Splunk Enterprise Security to leverage Cisco Talos' premium threat intelligence to enrich your findings for easier triage and detect threats.
Cisco Talos Intelligence helps to examine URLs, IP addresses, domain names and so on for security threat classifications and related threat intelligence. Cisco Talos Intelligence provides intelligence on the potential for malware, Command and Control (C2C) usage, phishing, or other malicious URL usage, and other threat classifications such as IP address reputation, acceptable use policy (AUP), threat level, or other descriptions. Intelligence enrichment of this type quickly speeds up triage and investigation of findings in the security operations center.
Cisco Talos Intelligence identifies threats in Splunk Enterprise Security automatically as a Talos Intelligence API lookup or as an adaptive response action.
Download and install Cisco Talos Intelligence for Enterprise Security from Splunkbase. Cisco Talos Intelligence for Enterprise Security is supported only on Splunk Enterprise Security Cloud deployments in AWS, GCP, or Azure, running Enterprise Security app versions 7.3.2 and higher. Cisco Talos Intelligence for Enterprise Security is not FedRAMP-certified.
Configure Cisco Talos Intelligence for Splunk Enterprise Security
Configuring Cisco Talos Intelligence for Splunk Enterprise Security is an automated process. After you install Cisco Talos Intelligence for Splunk Enterprise Security, a Talos certificate is deployed by the Cloud stack provisioning process. The certificate provisioning process might take up to an hour to complete. No user configuration is needed.
Run Cisco Talos Intelligence for Splunk Enterprise Security as an ad-hoc enrichment adaptive response action
You can run Cisco Talos Intelligence for Enterprise Security as an ad-hoc enrichment adaptive response action on observable fields to enrich findings as required.
Prerequisites
The app for Cisco Talos Intelligence for Enterprise Security is installed from Splunkbase.
Steps
- In Splunk Enterprise Security, go to the analyst queue on the Mission Control page.
- Select a finding.
- Under Actions, select the ellipses to open the drop-down menu and select Run adaptive response action.
- Select +Add new response action.
- Select Intelligence Enrichment with Talos.
- In the Observable field, select the field that contains the observable that must be enriched by Talos intelligence. For example, URL.
- In the Observable type field, select URL, IP, or Domain.
If the observable field does not contain a value of the observable type that is selected for enrichment, the Cisco Talos Intelligence adaptive response action fails.
- Select Run to run the Cisco Talos Intelligence for Enterprise Security on the selected observable.
If no matches are identified when Cisco Talos Intelligence for Enterprise Security is run, an empty Note field is not returned. However, you can view the enrichment data in the UI and the logs that are available in the Configuration page for the app.
The following figure displays the logs for the Talos adaptive response actions:
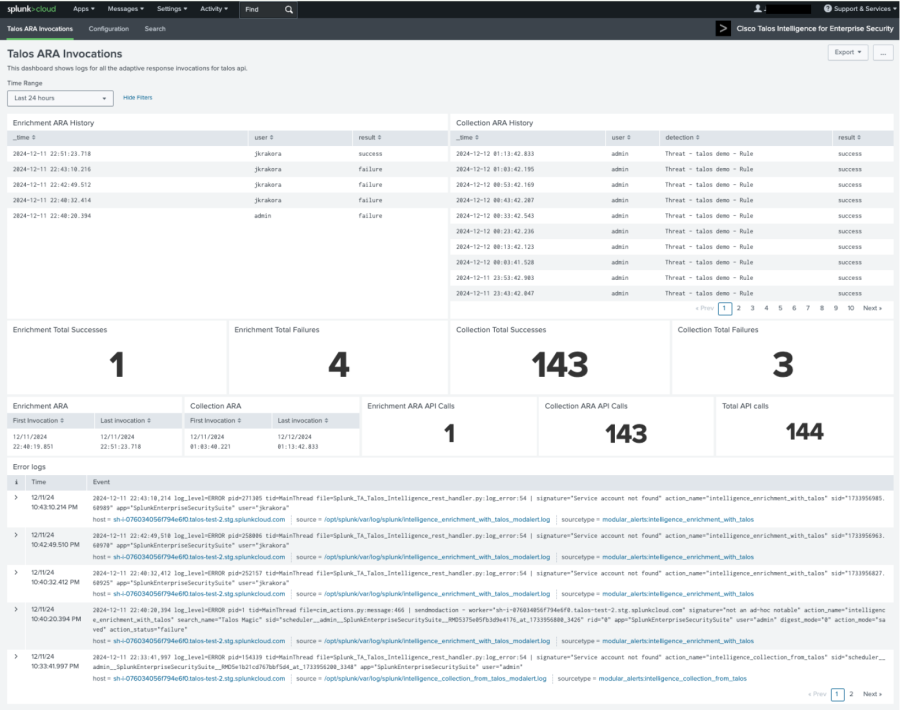
- Reload the finding or investigation on the analyst queue in the Mission Control page by refreshing your browser.
Refresh the analyst queue on the Mission Control page in Splunk Enterprise Security using the Refresh button on the page.
- Review the Notes section for enrichment data.
The following figure is a screenshot of how the enrichment data is displayed in the Notes section for the finding.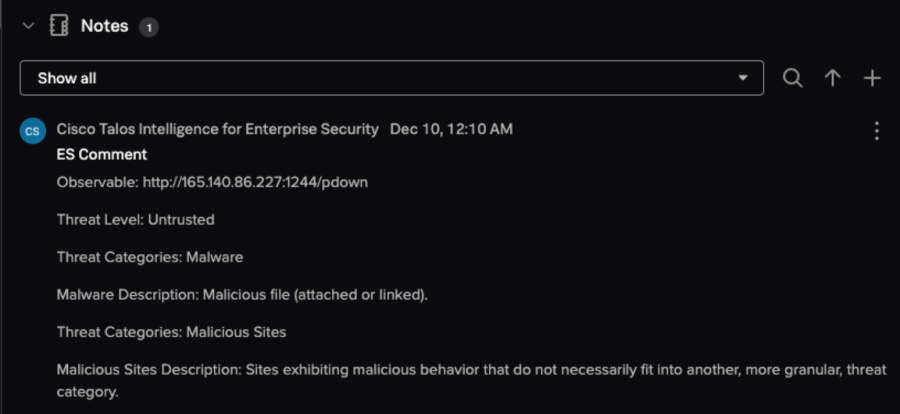
Run Cisco Talos Intelligence for Enterprise Security as a collection adaptive response action
You can run Cisco Talos Intelligence for Enterprise Security as a collection adaptive response action to add enrichment data to a detection using a specified index.
Running Cisco Talos Intelligence for Enterprise Security as a collection adaptive response action does not enrich findings automatically because a finding cannot be enriched using its unique identifier (ID) until it is created and associated with an ID.
Steps
- In Splunk Enterprise Security, go to the detection editor to create an event-based detection.
- Go to Adaptive response actions.
- Select +Add new adaptive response action.
- Select the Intelligence Collection from Talos adaptive response action that you want to add.
- In the Observable field, select the field that contains the observable that must be enriched by Talos intelligence. For example, URL.
- In the Observable type field, select URL, IP, or Domain.
- In the Index field, select the index to which you want to add the enrichment data from Talos. For example, main.
- Select Run to run the Cisco Talos Intelligence for Enterprise Security on the selected observable.
- In Splunk Enterprise Security, select the Search tab and enter index = main in the search bar to view the enrichment data in the main index. Running the collection adaptive response action might take a few minutes.
You can now build dashboards using the enrichment data in the main index or you can enrich findings created by the detection automatically.
Troubleshoot the failure of enrichment adaptive response actions
Issue
Adding the Cisco Talos Intelligence for Splunk Enterprise Security as an ad-hoc or automated enrichment adaptive response action on a detection that creates findings can cause the enrichment action to fail.
Cause
A race condition develops between the creation of the finding and the running of the adaptive response action because both the actions are run in parallel. When the Cisco Talos adaptive response action is run, the finding is not created completely. The finding must be created and available in the notable index before it can be enriched.
Solution
Set up an additional search that searches for existing findings and run the enrichment action on those events.
| UI field | Value |
|---|---|
| Query | `notable` |
| Time range | 60 minutes |
| Cron schedule | */60 * * * * |
| Trigger | For each result |
| Trigger action | Add: Intelligence Enrichment with Talos |
| Action setup: |
|
This search runs every hour and pulls findings for the past 1 hour.
Manually create a saved search for the enrichment adaptive response action
Create a saved search using Cisco Talos enrichment adaptive response action to automatically enrich findings with Cisco Talos data.
When a detection runs, you cannot automatically enrich the findings using the Talos enrichment adaptive response action. This occurs because the enrichment occurs in a separate lookup called the Incident Review lookup that requires the ID of the finding, which is not available before a finding is created. Therefore, the adaptive response action cannot be used to enrich the finding.
Follow these steps to manually run the adaptive response action and add enrichment notes to a finding:
- In the Splunk menu bar, go to Settings, select Searches, reports, and alerts and create an alert to include all findings that have the URL field and set the alert to trigger every 2 minutes. For more information, see Create alerts in the Splunk Cloud Platform™ Alerting Manual.
- Alternatively, create a saved search to include all the findings that have the URL field and configure it to run every 2 minutes.
or|saved search "Incident Review - Main" time_filter = **event_id_filter** source_filter = **security_domain_filter** status_filter = **owner_filter** urgency_filter = **tag_filter** disposition_filter = **investigation_guid_filter** investigation_filter = ** | search is_investigation **false" | search | eval_position = 1 | accum_position | eval_offset = position - 1 | search url**`notable` | search url ** - Use the Cisco Talos intelligence enrichment ARA to automatically enrich the finding. For more information, see Run the Cisco talos enrichment ARA. The saved search or alert runs every 2 minutes, and the Cisco Talos enrichment ARA turns on to automatically enrich all findings, every time a finding is created by the search.
See also
| Use Federated Analytics with Splunk Enterprise Security for threat detection in Amazon Security Lake (ASL) datasets | Overview of Mission Control in Splunk Enterprise Security |
This documentation applies to the following versions of Splunk® Enterprise Security: 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.31, 8.0.40
 Download manual
Download manual
Feedback submitted, thanks!