Implement security use cases using the Use Case Library in Splunk Enterprise Security
Use the Use Case Library in Splunk Enterprise Security to identify and implement relevant security monitoring use cases. The Use Case Library provides a structured collection of pre-built use cases that align with various security frameworks, such as the MITRE ATT&CK framework. These use cases are specifically tailored to address common security challenges.
Key features of the Use Case Library
Following are some key features of the Use Case Library in Splunk Enterprise Security:
- Pre-built use cases: The Use Case Library includes a wide range of pre-defined security use cases that address specific threats, vulnerabilities, and compliance requirements. Each use case typically includes relevant searches, dashboards, and reports that can be directly used or customized within Splunk Enterprise Security.
- Framework alignment: Use cases are often aligned with security frameworks such as MITRE ATT&CK, NIST, or ISO, thereby making it easier for you to map your security monitoring activities to industry standards and best practices.
- Ease of implementation: Security teams can quickly deploy these use cases to monitor their environments for specific threats or compliance requirements without needing to start from scratch.
- Continuous updates: The Use Case Library is regularly updated to include new use cases that reflect emerging threats and attack vectors. This ensures that you stay ahead of evolving cyber threats.
- Customization and expansion: Although the Use Case Library provides out-of-the-box functionality, it is highly customizable. You can modify the use cases to fit your specific environment or create new use cases based on the templates provided.
Identify the appropriate Analytic Stories and searches
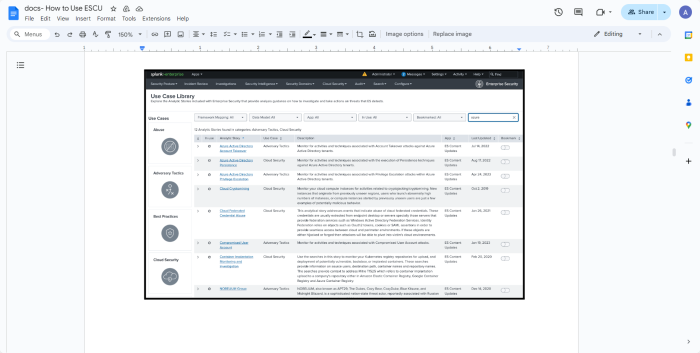
To identify the Analytic Stories and searches that are relevant to your specific needs, you can leverage common industry use cases and apply filters within the Content Library of your application. These filtering options help to streamline the process of identifying the most relevant and effective searches for your security operations and ensure that you utilize the capabilities of the Analytic Stories to the maximum extent. Following are some methods that you can use to filter and find the appropriate Analytic Stories and searches:
- Framework mappings: Filter by security frameworks such as MITRE ATT&CK TTPs, NIST guidelines, and CIS controls to align searches with specific compliance or security standards.
- Data models: Use data models to find searches that correlate with the structured data formats that you use in your environment.
- Names of Analytic Stories: Search directly by the names of Analytic Stories to find specific content.
- Categories of use cases: Filter searches by use case categories such as Abuse, Adversary Tactics, Best Practices, and Cloud Security, depending on the focus area of your security operations.
- Keyword Search: Enter a keyword related to a specific use case that you are interested in such as Malware or Vulnerability to find relevant Analytic Stories and searches.
These filtering options help streamline the process of identifying the most relevant and effective searches for your security operations, ensuring you utilize the capabilities of the Analytic Stories to their fullest extent.
| Exploring security content with Splunk Enterprise Security | Components of a detection analytic |
This documentation applies to the following versions of Splunk® Enterprise Security Content Update: 3.22.0, 3.23.0, 3.24.0, 3.25.0, 3.26.0, 3.27.0, 3.28.0, 3.29.0, 3.30.0, 3.31.0, 3.32.0, 3.33.0, 3.34.0, 3.35.0, 3.36.0, 3.37.0, 3.38.0, 3.39.0, 3.40.0, 3.41.0, 3.42.0, 3.43.0, 3.44.0, 3.45.0, 3.46.0, 3.47.0, 3.48.0, 3.49.0, 3.50.0, 3.51.0, 3.52.0, 3.53.0, 3.54.0, 3.55.0, 3.56.0, 3.57.0, 3.58.0, 3.59.0, 3.60.0, 3.61.0, 3.62.0, 3.63.0, 3.64.0, 4.0.0, 4.0.1, 4.1.0, 4.2.0, 4.3.0, 4.4.0, 4.5.0, 4.6.0, 4.7.0, 4.8.0, 4.9.0, 4.10.0, 4.11.1, 4.12.0, 4.13.0, 4.14.0, 4.15.0, 4.16.0, 4.17.0, 4.18.0, 4.19.0, 4.20.0, 4.21.0, 4.22.0, 4.23.0, 4.24.0, 4.25.0, 4.26.0, 4.27.0, 4.28.0, 4.29.0, 4.30.0, 4.31.0, 4.31.1, 4.32.0, 4.33.0, 4.34.0, 4.35.0, 4.36.0, 4.37.0, 4.38.0, 4.39.0, 4.40.0, 4.41.0, 4.42.0
 Download manual
Download manual
Feedback submitted, thanks!