Use the risk notable playbook pack to investigate a risk notable in Splunk SOAR
This collection of playbooks and workbooks guides an analyst through an investigation of a risk notable within Splunk SOAR. Risk notables are an aggregate of risk anomalies within Splunk Enterprise Security (ES). See Analyze risk in Splunk Enterprise Security in the Use Splunk Enterprise Security manual. Learn how to utilize the workbooks as an analyst, understand the playbooks, and explore customizing the playbooks.
What you need before you can use the playbook pack
Verify the following dependencies are in place before using the playbook pack:
- Splunk SOAR (Cloud) or Splunk SOAR (On-premises)
- Splunk ES with assets and identities. See Manage assets and identities in Splunk Enterprise Security in the Administer Splunk Enterprise Security manual.
- Splunk ES with the risk analysis framework producing risk notables. See Analyze risk in Splunk Enterprise Security in the User Splunk Enterprise Security manual.
- You must produce notable events from Splunk ES with the following fields:
- risk_object
- event_id
- info_min_time
- info_max_time
- urgency
-
Use one of the following apps on Splunkbase to get Splunk ES notable events into Splunk SOAR:
- Phantom App for Splunk.
Configure the multi-value field settings of the Phantom App for Splunk to consolidate events into a single artifact. See About the Phantom App for Splunk and Configure how Splunk Phantom and Splunk SOAR handle multivalue fields in Splunk ES notable events in Use the Splunk Phantom App for Splunk to Forward Events manual. -
Splunk App for SOAR.
The following example query can be used in the "on poll" settings to find notable events with the correct fields:`notable` | search eventtype=risk_notables | fields _time, event_hash, event_id, host, info_min_time, info_max_time, risk_object, risk_object_type, risk_score, rule_description, rule_id, rule_name, search_name, source, splunk_server, urgency
- Phantom App for Splunk.
Deployment steps for using the playbook pack
Verify the following deployments steps are done before using the playbook pack:
- This playbook pack follows a five-point scale for severity based on Splunk ES. A Splunk SOAR administrator must add Critical and Informational to the default severities of High, Medium, and Low. See Create custom severity names in the Administer Splunk SOAR (Cloud) manual.
- This playbook pack uses the risk_notable label based on the notable event type of the same name within Splunk ES. A Splunk SOAR administrator must add this new label. See Create a label in the Administer Splunk SOAR (Cloud) manual.
- Customize the playbooks as needed, then click Save as in the local repository. Be sure to update the matching sub-playbook calls to reference the correct repository, and update the workbooks to reference the correct repository for manually initiated playbooks.
- If your Splunk asset on SOAR is not called splunk, change the asset name in the playbook to match the name of your Splunk asset.
- If Splunk Web is configured on an alternative port other than 443 (such as 8000), then include the specified port (such as :8000) directly after the hostname in these items:
- the block "format es url" in the risk_notable_preprocess playbook.
- the block "format summary note" in the risk_notable_import_data playbook.
How to find the playbooks in Splunk SOAR
To locate the playbooks in the playbook pack in Splunk SOAR, perform the following steps:
- In Splunk SOAR (Cloud) or Splunk SOAR (On-premises) main menu, select Playbooks.
- Click Update from Source Control, select community, and then click Update.
- (Optional) Copy the playbooks to the local repository so that you can customize them.
Workbooks and playbooks in this playbook pack
Workbooks are a guided analyst workflow with Phases and Tasks that can recommend actions and playbooks. This pack includes two workbooks.
| Workbook | Description | Phase | Tasks | Workbook playbooks | Task playbooks |
|---|---|---|---|---|---|
| Risk Investigation | Guide the analyst from ownership of the investigation through rendering a verdict and selecting a response plan. | Initial Triage | Preprocess Investigate Render Verdict |
risk_notable_investigate | risk_notable_preprocess risk_notable_import_data |
| Risk Response | A sample response plan that guides the analyst through reviewing suspect indicators and selecting which assets or users need protecting. | Mitigate | Block Indicators Protect Assets and Users |
risk_notable_mitigate | risk_notable_review_indicators risk_notable_block_indicators |
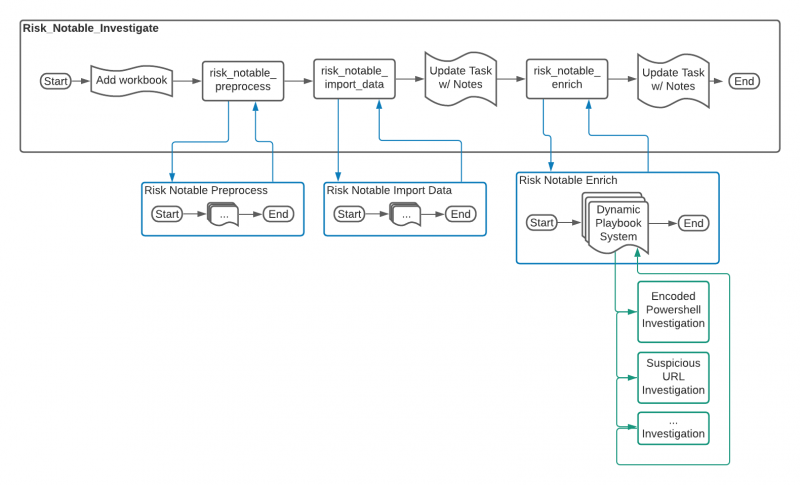
Flow of the risk_notable_investigate playbook
The following image shows the workflow of the risk_notable_investigate playbook.
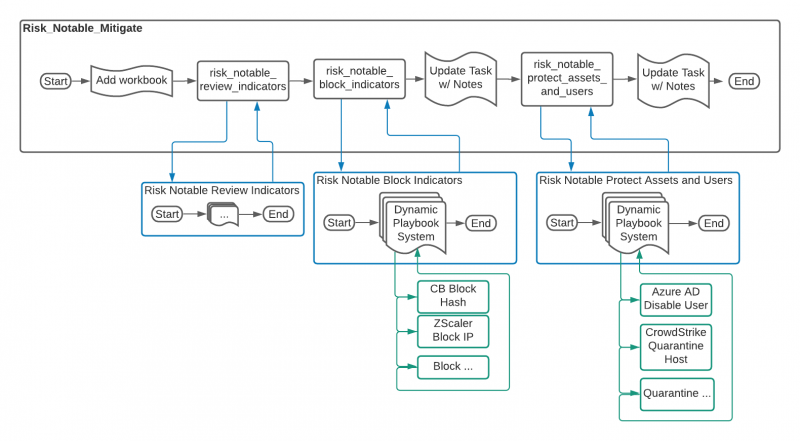
Flow of the risk_notable_mitigate playbook
The following image shows the workflow of the risk_notable_mitigate playbook.
Playbook descriptions
The playbooks included in this playbook pack are described in the following table.
| Playbook | Description | How to implement |
|---|---|---|
| risk_investigate | This playbook checks for the presence of the Risk Investigation workbook and updates tasks or leaves generic notes. | Set this playbook to run in Active mode on the Risk Notable label in Splunk SOAR.
|
| risk_mitigate | This playbook checks for the presence of the Risk Response workbook and updates tasks or leaves generic notes. The risk_notable_verdict playbooks recommends this playbook as a second phase of the investigation. Additionally, this playbook can be used in ad-hoc investigations or incorporated into custom workbooks. | You can configure this playbook to automatically add notes. See Playbook outputs. |
| risk_notable_preprocess | This playbook prepares a risk notable for investigation by performing the following tasks:
|
See Deployment steps for using the playbook pack. |
| risk_notable_import_data | This playbook gathers all of the events associated with the risk notable and imports them as artifacts. It also generates a custom markdown formatted note. | The Splunk search used to locate contributing events requires three fields in the notable artifact: risk_object, info_min_time, and info_max_time. The query also performs some deduplication on contributing events and may need to be adjusted based on individual Enterprise Security environments. Mitre Tactics and Techniques appear if using the annotation framework in Splunk ES. See Use security framework annotations in correlation searches in the Administer Splunk Enterprise Security manual.
A custom code block sorts the returned event data and produces a markdown formatted note into the note_content output field. This field is then available for use in downstream playbooks. |
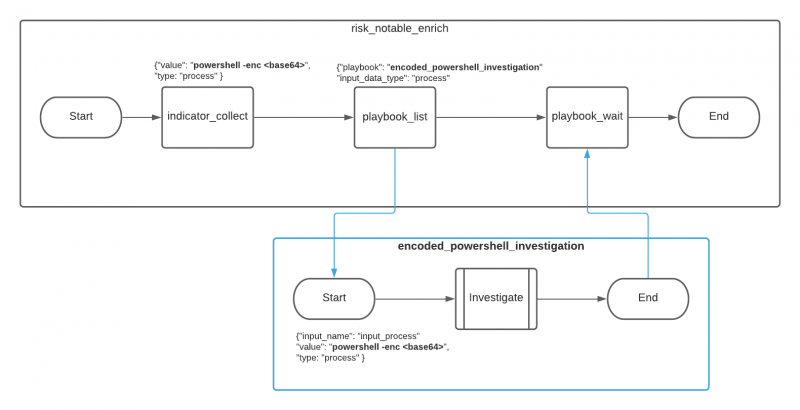
| risk_notable_enrich | This playbook collects the available Indicator data types within the event as well as available investigative playbooks. It will launch any playbooks that meet the filtered criteria. | See Call child playbooks with the dynamic playbook system for more information on building or customizing a playbook for inclusion with risk_notable_enrich. |
| risk_notable_merge_events | This playbook finds related events based on key fields in a risk notable and allows the user to process the results and decide which events to merge into the current investigation. | Combining the list_merge utility within the playbook with the find_related_containers utility allows for fine-tuning of related event criteria. For example, the default filtering criteria uses description, risk_object, and threat_object as the important fields and requires at least three matches before an event is considered related. There are several options to customize the associated criteria, including adding more fields in list_merge, reducing or increasing the minimum match count, or utilizing the wildcard feature of find_related_containers. |
| risk_notable_verdict | This playbook locates available playbooks with the response tag and presents them to the analyst. Based on the analyst selection, it will launch its chosen playbook. | See Call child playbooks with the dynamic playbook system for more information on building or customizing a playbook for inclusion with risk_notable_verdict. |
| risk_notable_review_indicators | This playbook was designed to be called by a user to process indicators that are marked as suspicious within the SOAR platform. Analysts will review indicators in a prompt and mark them as blocked or safe. | See Indicator tagging system for more information about the blocking workflow. |
| risk_notable_block_indicators | This playbook handles locating indicators marked for blocking and determining if any blocking playbooks exist. If there is a match to the appropriate tags in the playbook, a filter block routes the name of the playbook to launch to a code block. |
|
| risk_notable_protect_assets_and_users | This playbook attempts to find assets and users from the notable event and match those with assets and identities from Splunk ES. If a match was found and the user has playbooks available to contain entities, the analyst decides which entities to disable or quarantine. | See Call child playbooks with the dynamic playbook system for more information on building or customizing a playbook for inclusion with risk_notable_protect_assets_and_users. |
Call child playbooks with the dynamic playbook system
The dynamic playbook system allows several of the playbooks in this pack to call child playbooks without requiring a SOAR automation engineer to make any changes to their existing playbooks or to the risk notable playbook pack. To make sure that unwanted playbook calls are not executed, the following safeguards exist:
- Only playbooks in the specified repository can be launched. By default, the playbook_list defines that only playbooks in the local repository can be launched.
- Only playbooks with the required tags can be launched.
Each playbook in the content pack that calls content within the Splunk SOAR environment contains the playbook_list utility to enforce these safeguards. A Splunk SOAR automation engineer can adjust the playbook_list utility as needed to match any specific needs.
The decide and launch playbooks custom code block calls the appropriate child playbook based on the circumstances.
The following table correlates each playbook with the matching criteria to call a child playbook. For more information on playbook types, see Create a new playbook in Splunk SOAR (Cloud) in the Build Playbooks with the Playbook Editor manual.
| Playbook | Matching criteria |
|---|---|
| risk_notable_enrich |
|
| risk_notable_verdict |
|
| risk_notable_block_indicators |
|
| risk_notable_protect_assets_and_users |
|
Playbook outputs
Child playbooks must produce standard outputs in order to forward data to risk notable playbooks. The End block of the playbook must have a field for note_title and a second field for note_content in order for the playbook to be used in the dynamic playbook system. Both automation and input playbook types support outputs in the End block. See Add outputs to Automation and Input playbooks in the Build Playbooks with the Playbook Editor manual.
Indicator tagging system
The risk_notable_review_indicators and risk_notable_block_indicators playbooks use the indicator_get_by_tag utility to fetch indicators with specific tags. To include an indicator with the risk notable playbook pack, the playbook that investigates that indicator type must tag that indicator using the indicator_tag utility.
The following table lists the indicator tags and how the tags are used.
| Tags | Where the tag is used by the playbook pack | How user-created playbooks should use the tag |
|---|---|---|
| suspicious malicious |
Risk_notable_review_indicators prompts the user with any indicators that contain this tag. | When building an investigation playbook, tag an indicator with one of these values. See Example child playbook deployment for an example of how to deploy a child playbook. |
| safe | Risk_notable_review_indicators and risk_notable_block_indicators skip this tag. | When building an investigation playbook tag, known good indicators should be tagged with this value. |
| marked_for_block |
|
risk_notable_review_indicators risk_notable_block_indicators |
| blocked |
|
When building a blocking playbook, tag an indicator with this value after a successful block has occurred. |
Example child playbook deployment
To demonstrate the dynamic playbook system we will walk through the addition of an investigation playbook for URLs. We will use Phishtank to investigate the URLs because it is available in all Splunk SOAR environments.
- Create a new playbook called risk_notable_url_investigation.
- Choose Input Playbook for the playbook type, because this playbook will have URLs as input.
- Add the tags investigate and risk_notable to the playbook in the Settings tab so that the playbook will be executed by risk_notable_enrich.
- Build the playbook logic. In this example, create a single url reputation action using Phishtank and pass in the playbook input URLs.
- Filter the results with the following logic:
["url_reputation_1:action_result.summary.In Database", "==", True], ["url_reputation_1:action_result.summary.Valid", "==", True], ["url_reputation_1:action_result.summary.Verified", "==", True]
- Pass the filtered URLs to the indicator_tag custom function to tag them as suspicious. This will be read by the risk_notable_review_indicators playbook and shown to the analyst to make a decision about a response action.
- Use a format block to create a playbook output to summarize the investigation of the URLs.
- Output the format block to the End block in a field called note_content. Give your note a title by creating a field called note_title in the same End block.
| Configure Splunk Enterprise Security to use the Machine Learning Toolkit |
This documentation applies to the following versions of Splunk® Security Content: 3.29.0, 3.30.0, 3.31.0, 3.32.0, 3.33.0, 3.34.0, 3.35.0, 3.36.0, 3.37.0, 3.38.0, 3.39.0, 3.40.0, 3.41.0, 3.42.0
 Download manual
Download manual
Feedback submitted, thanks!