Validate data sources that feed the InfoSec app for Splunk data models
Validate the data sources for each of the data models that are listed on the Health dashboard of the Splunk InfoSec app, even if the Health dashboard reports that data is fed into the data model.
If only partial data is fed into the data models, you might need to adjust your configuration to ensure full coverage of your Splunk Platform. Additionally, your data sources might feed more than one data model.
The following diagram shows some of the data sources that feed into the data models for the InfoSec app, including firewall, LDAP, and antivirus data:
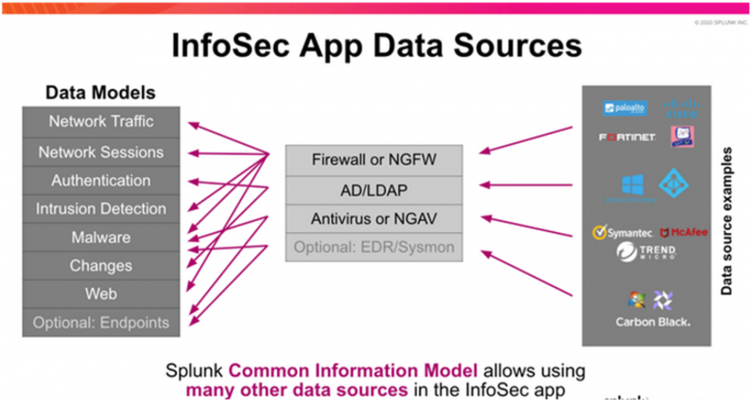
Validate data model configuration
Follow these steps to validate data model configurations and to check that the data sources feed the data models as expected:
- Use the following search to identify the indexes and source types that feed each of the InfoSec data models:
| makeresults | eval datamodels = "Authentication:Change:Endpoint:Intrusion_Detection:Network_Sessions:Network_Traffic:Malware:Endpoint.Processes:Web" | makemv delim=":" datamodels | mvexpand datamodels | map search="| makeresults | eval notfound=\"*** NO DATA FOUND ***\" | append [| tstats count from datamodel=$datamodels$ by index, sourcetype] | eventstats count as events |eval datamodel=\"$datamodels$\", index=coalesce(index,notfound)| search NOT notfound=* OR events=1 | table datamodel, index, sourcetype,count" | sort datamodel, index, sourcetypeIf the results of the search indicate that each of the required data models for the InfoSec app is populated with data, you can accelerate the data models. See Accelerate data models to build InfoSec app dashboards.
If the results of the search indicate that all the required data models for the InfoSec app are not populated with data, proceed to the next step.
- Identify the tagged events to configure the data models that are required by the InfoSec app within your Splunk Platform environment. To identify the tagged events and configure your data models, see Identify tagged events to configure data models.
- Repeat the process for each data model.
Identify tagged events to configure data models
Follow these steps to identify tagged events and to configure the data models. This example uses the Authentication data model, but you can follow these steps to identify tagged events for any data model.:
- On the Splunk Platform menu bar, select Configure > Settings > Data models.
- Select the Authentication data model from the list of data models.
- Use the search bar to identify the events that must feed the Authentication data model.
(`cim_Authentication_indexes`) tag=authentication NOT (action=success user=*$)The first part of the search contains a macro called
cim_Authentication_indexes. This macro constrains the search to certain indexes.You must restrict a data model to only the indexes that feed it with data.
The next part of the search
tag=authenticationconstrains the search to return events that are tagged as authentication events.The last part of the search
NOT (action=success user=*$)excludes any event that contains a field with the labelactionthat has the valuesuccessAND the fielduserthat has a value that ends with the$character. - Identify the data sources in Splunk that might fit your search. For more information on identifying data sources, see Identify data sources that feed data models.
Identify data sources that feed data models
Follow these steps to identify the data sources that feed the data models:
- Open a new Splunk Platform search window in another tab of your browser.
- Click Search & Reporting.
- Select Open Link in New Tab.
Before switching to the new browser tab, highlight and copy the search from the tab you are in and paste it into the search bar in the new browser window. - Run the search in the new tab.
- Modify the search to include all the indexes within your Splunk environment.
- Run the following search to see if any results are returned:
index=* tag=authentication NOT (action=success user=*$) | stats count by index, sourcetype - Modify the search macro for the data model if your search results show indexes and data sources. For more information on modifying the search macro, see Modify the search macro for the data model.
Modify the search macro for the data model
Prerequisite
Take note of the name of the indexes returned by the search in Identify the data sources that feed the data models so that you can update the macro.
Follow these steps to modify the search macro for the data model. This example uses the Authentication data model which is fed by the demo_oracle and demo_wineventlog indexes, but you can follow these steps to modify the search macro for any data model.:
- On the Splunk platform menu bar, select Configure > Settings.
- Open Advanced Search under the Settings menu.
- Open Search Macros.
- Search for the
cim_Authentication_indexesmacro. You might need to adjust the filter to find the macro. - Set the app context to All and type cim_authentication_indexes into the search filter.
If the definition is set toindex=main, the Authentication data model was not fed data. - Click on the macro name to edit the macro.
- Change the Indexes Allowlist to include the indexes that were identified in the previous step.
- Click Save.
- Rerun the following original data model search to verify that the change to the search macro was successful.
(`cim_Authentication_indexes`) tag=authentication NOT (action=success user=*$) - Repeat this process for all of the following InfoSec data models:
- Authentication
- Change (for app version 1.6.x and higher) or Change Analysis (for app version 1.5.3 and lower)
- Intrusion_Detection
- Malware
- Network_Sessions
- Network_Traffic
- Endpoint
- Web
Examples searches for InfoSec app data models
The following table lists the default constraining search and search macro for each of the required data models for the Infosec app. There is no search macro defined for the data models listed. If the search macros is not defined for the data model, the data model relies on the data that resides in the indexes that are searched by default.
| Data model | Base search | Search macro |
|---|---|---|
| Authentication |
|
No search macro defined |
| Change |
|
No search macro defined |
| Intrusion Detection |
|
No search macro defined |
| Malware |
|
No search macro defined |
| Network Sessions |
|
No search macro defined |
| Network Traffic |
|
No search macro defined |
| Endpoint |
|
No search macro defined |
| Web |
|
No search macro defined |
| Confirm the health of the InfoSec app for Splunk | Accelerate data models to build InfoSec app for Splunk dashboards |
This documentation applies to the following versions of Splunk® InfoSec App: 1.6.4, 1.7.0
 Download manual
Download manual
Feedback submitted, thanks!