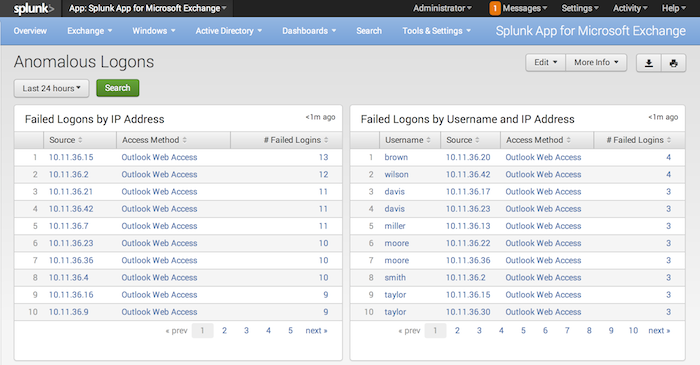
Anomalous Logons
This page displays anomalous logons into the Exchange network, including:
- Failed logons by IP address.
- Failed logons by username.
- A list of users who log in from multiple countries or regions.
- A list of the top 10 server accesses by locked out users over the last 24 hours.
- The event codes that Exchange logged when those users attempted to connect to the system.
How to use this page
- Set the desired time range by choosing the time range picker.
- Click "Search' to see anomalous logons and other activities that have occurred in the time range you specified.
- In any of the panels, click a link to see the base search that returned the result you clicked.
| Administrator Audit | Distribution Lists |
This documentation applies to the following versions of Splunk® App for Microsoft Exchange (EOL): 3.4.2, 3.4.3, 3.4.4, 3.5.0, 3.5.1, 3.5.2, 4.0.0, 4.0.1, 4.0.2, 4.0.3
 Download manual
Download manual
Feedback submitted, thanks!