What you need to install the Splunk Phantom App for Splunk
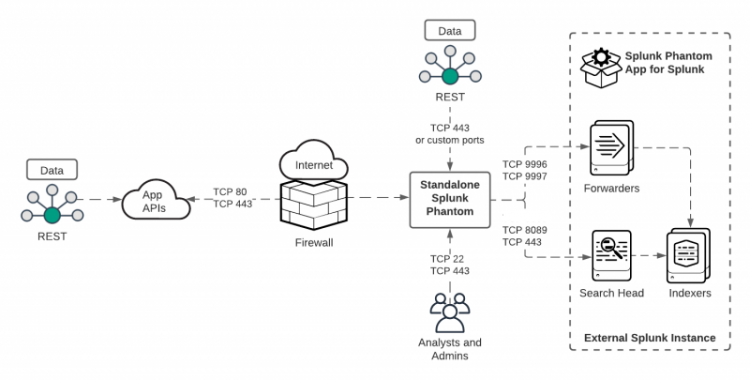
Verify that your environment is ready to use the Splunk Phantom App for Splunk to integrate Splunk Phantom or Splunk SOAR with your Splunk deployment. The following image shows how Splunk Phantom is integrated into a Splunk environment.
Required user privileges and ports
Verify the following user privileges and ports:
- The Splunk Phantom App for Splunk requires that a user with administrative privileges installs both the Splunk Phantom App for Splunk and Splunk software. In situations where events can't be sent from the Splunk platform to Splunk Phantom or Splunk SOAR using alert actions, adaptive response actions, or event forwarding, the events are stored in the phantom_retry KV Store collection. The Splunk Phantom App for Splunk requires the admin user to run the
phantom_retry.pyscript every 60 seconds to try to send any events that could not be sent earlier. In Splunk Cloud environments, you must file a support ticket to modify thelocal/inputs.conffile in order to make sure the retry script can be run. See Splunk Cloud requirements. - Splunk Phantom must have TCP ports 443, 8088, and 8089 open to and from Splunk Enterprise Security (ES) search heads. Splunk Cloud requires some custom port definitions. See Splunk Cloud requirements.
- In your on-premises deployment, verify that you have the necessary network availability among all devices.
Splunk platform requirements
The Splunk Phantom App for Splunk requires specific Splunk platform combinations. For example, Splunk ES versions 6.5.1, 6.5.x means that Splunk ES version 6.5.1 or any 6.5.x release later than 6.5.1 is required.
Product compatibility matrix with Splunk Cloud
Verify that you are using the following product version combinations if you installing the Splunk Phantom App for Splunk on Splunk Cloud:
| Splunk Phantom App for Splunk Version | Splunk Cloud Version | Splunk ES Version | Splunk Phantom Version | Splunk SOAR Version |
|---|---|---|---|---|
| 4.1.3 (CIM version 4.18.0) |
8.2.2105 | 6.5.1, 6.5.x | 4.10.5.586400, 4.10.x | 4.12.0.56071, 4.12.x |
| 8.2.2104.1 | 6.5.1, 6.5.x | 4.10.4, 4.10.x | 4.12.0.56045, 4.12.x | |
| 8.1.2103 | 6.5.1, 6.5.x | 4.10.4, 4.10.x | 4.12.0.56045, 4.12.x | |
| 4.0.35 (CIM version 4.18.0) |
8.2.2104 | 6.5.1, 6.5.x | 4.10.3.51283, 4.10.x | N/A |
| 8.1.2103 | 6.5.x | 4.10.3.51283, 4.10.x | N/A | |
| 8.1.2101 | 6.2.x | 4.10.1.45070, 4.10.x | N/A | |
| 8.1.2101 | 6.4.1, 6.4.x | 4.10.0.40025, 4.10.x | N/A | |
| 8.1.2012 | 6.2.0, 6.2.x | 4.10.0.40961, 4.10.x | N/A | |
| 8.1.2012 | 6.4.1, 6.4.x | 4.10.0.40025, 4.10.x | N/A | |
| 8.1.2011 | 6.2.0, 6.2.x | 4.10.0.40961, 4.10.x | N/A | |
| 8.1.2011 | 6.4.1, 6.4.x | 4.10.0.40025, 4.10.x | N/A | |
| 8.1.2009 | 6.2.0, 6.2.x | 4.10.0.40961, 4.10.x | N/A | |
| 8.0 | 6.1.1, 6.1.x | 4.10.0.40961, 4.10.x | N/A | |
| 7.3 | 5.3.1, 5.3.2 | 4.10.0.40961, 4.10.x | N/A | |
| 4.0.10 (CIM version 4.18.0) |
8.0.3 | 6.1.1, 6.1.x, 6.2.0, 6.2.x | 4.8.24304, 4.8.x, 4.9.39220, 4.9.x | N/A |
| 7.3.5 | 5.3.1, 5.3.x | 4.8.24304, 4.8.x, 4.9.39220, 4.9.x | N/A | |
| 7.2.10.2 | 5.3.1, 5.3.x | 4.8.24304, 4.8.x, 4.9.39220, 4.9.x | N/A |
Product compatibility matrix with Splunk Enterprise
Verify that you are using the following product version combinations if you installing the Splunk Phantom App for Splunk on Splunk Enterprise:
| Splunk Phantom App for Splunk Version | Splunk Enterprise Version | Splunk ES Version | Splunk Phantom Version | Splunk SOAR Version |
|---|---|---|---|---|
| 4.1.3 (CIM version 4.18.0) |
8.2 | 6.6.0, 6.6.x | 4.10.4, 4.10.x | 4.12.0.56045, 4.12.x |
| 8.1 | 6.6.0, 6.6.x | 4.10.4, 4.10.x | 4.12.0.56045, 4.12.x | |
| 4.0.35 (CIM version 4.18.0) |
8.2, 8.2.x | 6.5.0, 6.5.x | 4.10.1.45070, 4.10.x | N/A |
| 8.1, 8.1.x | 6.2.0, 6.2.x | 4.10.0.40025, 4.10.x | N/A | |
| 8.1, 8.1.x | 6.4.1, 6.4.x | 4.10.0.40025, 4.10.x | N/A | |
| 8.0 | 6.1.1, 6.1.x | 4.10.0.40025, 4.10.x | N/A | |
| 8.0 | 6.4.1, 6.4.x | 4.10.0.40025, 4.10.x | N/A | |
| 7.3 | 5.3.1, 5.3.x | 4.10.0.40025, 4.10.x | N/A | |
| 4.0.10 (CIM version 4.18.0) |
8.0.3 | 6.1.1, 6.1.x, 6.2.0, 6.2.x | 4.8.24304, 4.8.x, 4.9.39220, 4.9.x | N/A |
| 7.3.5 | 5.3.1, 5.3.x | 4.8.24304, 4.8.x, 4.9.39220, 4.9.x | N/A | |
| 7.2.10.2 | 5.3.1, 5.3.x | 4.8.24304, 4.8.x, 4.9.39220, 4.9.x | N/A | |
| 3.0.5 (CIM version 4.8.0) |
8.0 | 6.0.0, 6.0.x | 4.6.19142, 4.6.x | N/A |
| 7.3.3 | 5.3.1, 5.3.x | 4.6.19142, 4.6.x | N/A |
Required apps
Make sure you have the following apps installed on your Splunk platform:
| App | Description |
|---|---|
| Splunk Phantom App for Splunk (this app) | Download the Splunk Phantom App for Splunk from Splunkbase. This app is required to map event fields to CEF format, then forward those events to Splunk Phantom. |
| Common Information Model | Download the Splunk Common Information Model (CIM) from Splunkbase. If you have Splunk Enterprise Security (ES) installed, you don't need to download this library as it is already included with Splunk ES.
|
Splunk Cloud requirements
Verify the following tasks are done before proceeding with your Splunk Phantom or Splunk SOAR integration with Splunk Cloud:
- Splunk Cloud requires static IP addresses and fixed ports to connect to Splunk Phantom or Splunk SOAR.
- Your Splunk Phantom instance must be running in the DMZ or perimeter network with the appropriate firewalls or reverse proxies to support internal connectivity.
- Submit a support request to the Splunk Cloud team to assist you with TLS certificate configuration.
- Splunk Phantom requires a publicly valid certificate chain. The cacerts.pem file must be configured into a single PEM certificate file with the server, intermediate, and root certificates.
- If the user invoking the
phantom_retry.pyscript is not the admin user, submit a support request to to the Splunk Cloud team to modify thelocal/inputs.conffile to contain:[script://$SPLUNK_HOME/etc/apps/phantom/bin/scripts/phantom_retry.py] passAuth = <username>
Also make sure thelocal/inputs.conffile does not change ownership or permission.
| About the Splunk Phantom App for Splunk | Install the Splunk Phantom App for Splunk |
This documentation applies to the following versions of Splunk® Phantom App for Splunk: 4.1.3
 Download manual
Download manual
Feedback submitted, thanks!