About the Splunk Phantom App for Splunk
Splunk Phantom and Splunk SOAR can use the Splunk platform as a source of data by ingesting events. The Splunk Phantom App for Splunk is required to configure Splunk Enterprise or Splunk Cloud Platform as a data source for getting data into Splunk Phantom or Splunk SOAR.
What does the Splunk Phantom App for Splunk do?
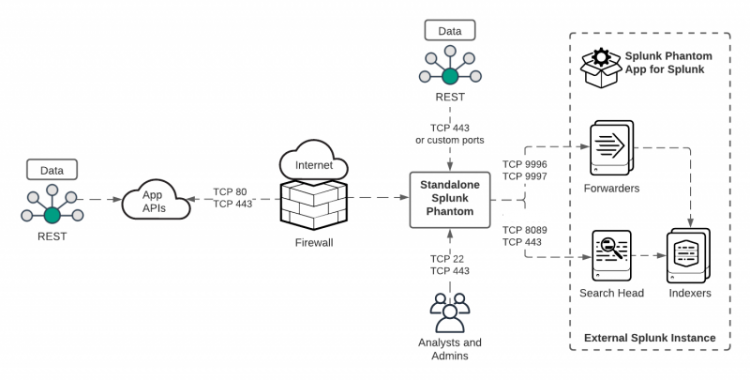
The following image shows an example of how a standalone Splunk Phantom instance is integrated with a Splunk platform environment.
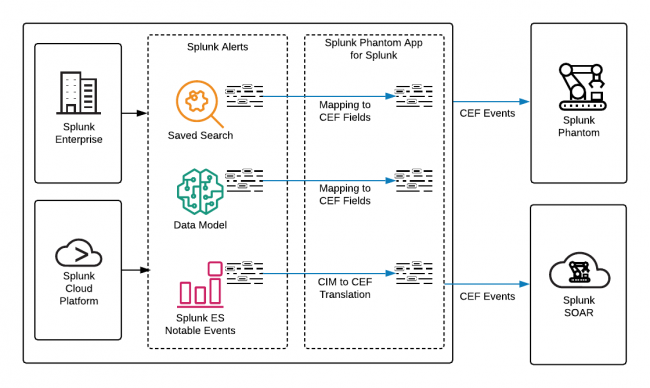
The Splunk Phantom App for Splunk is installed as an app on the Splunk platform and forwards events to Splunk Phantom or Splunk SOAR. The Splunk platform environment consists of raw events or Common Information Model (CIM) data, while Splunk Phantom and Splunk SOAR use the Common Event Format (CEF). The Splunk Phantom App for Splunk acts as a translation service between the Splunk platform and Splunk Phantom or Splunk SOAR by performing the following tasks:
- Mapping fields from Splunk platform alerts, such as saved searches and data models, to CEF fields.
- Translating CIM fields from Splunk Enterprise Security (ES) notable events to CEF fields.
- Forwarding events in CEF format to Splunk Phantom or Splunk SOAR, which are stored as artifacts.
How Splunk Phantom integrates with the Splunk platform
The following image shows how Splunk Phantom is integrated into a Splunk environment.
Before you install the Splunk Phantom App for Splunk, make sure you review the requirements.
- If you are using Splunk Enterprise, see What you need to install the Splunk Phantom App for Splunk on Splunk Enterprise.
- If you are using Splunk Cloud Platform, see What you need to install the Splunk Phantom App for Splunk on Splunk Cloud Platform.
| Welcome to the Splunk Phantom App for Splunk release 4.1.73 | What you need to install the Splunk Phantom App for Splunk on Splunk Enterprise |
This documentation applies to the following versions of Splunk® Phantom App for Splunk: 4.1.73
 Download manual
Download manual
Feedback submitted, thanks!