Connect to a distributed Splunk platform deployment
Follow the steps listed to connect your Splunk Phantom instance or cluster to a distributed Splunk Enterprise or Splunk Cloud deployment.
- Set up the HTTP Event Collector on the Splunk platform.
- Create the required user accounts on the Splunk platform for Splunk Phantom.
- Configure Splunk Phantom to use a distributed Splunk platform deployment.
Set up the HTTP Event Collector on the distributed Splunk platform deployment
Enable the HTTP Event Collector (HEC) on the Splunk platform and create a new token so you can use the HEC. Repeat these tasks on other indexers if those other indexers require separate HEC tokens. See Scale HTTP Event Collector with distributed deployments in the Splunk Enterprise Getting Data In manual for more information.
Follow the instructions for your Splunk Enterprise or Splunk Cloud deployment:
| Deployment Type | Documentation |
|---|---|
| Distributed Splunk Enterprise | See Configure HTTP Event Collector on Splunk Enterprise for instructions. |
| Splunk Cloud | Configure HTTP Event Collector on Splunk Cloud for instructions. |
| Splunk Cloud free trial | Configure HTTP Event Collector on Splunk Cloud free trial for instructions. |
During the procedure, do not click the Enable indexer acknowledgment checkbox when creating an Event Collector token. HTTP Event Collector indexer acknowledgement is not supported. See About HTTP Event Collector Indexer Acknowledgement for information about how to disable indexer acknowledgement if you have enabled it.
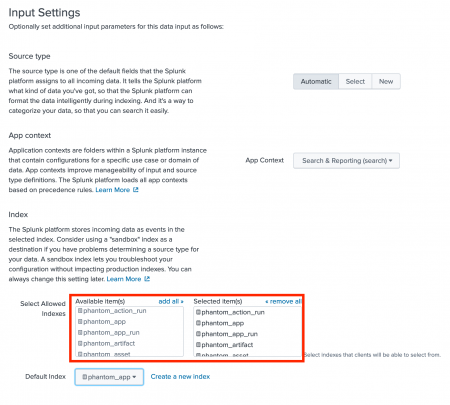
When you are creating the new token, you must select all of the phantom_ indexes and move them to the Selected item(s) list. Then, select the index you want to use as the default index, such as phantom_app. The screenshot shows an example:
On the HTTP Event Collector page, copy the token value for the new token. You will need this value when you configure Splunk Phantom. If you don't copy it now, you can return to the HTTP Event Collector page to obtain the value later when you need it.
Create the required user accounts on the distributed Splunk platform deployment for Splunk Phantom
Splunk Phantom requires two user accounts with roles added by the Phantom Remote Search app. The roles are phantomsearch and phantomdelete. You can use any user names you like for these accounts. These instructions use phantomsearchuser and phantomdeleteuser as examples.
Create these accounts on a search head. These users will be replicated to the rest of the cluster automatically. See Add users to the search head cluster in Distributed Search.
- In Splunk Web, select Settings > Access Controls.
- Create the user account with the
phantomsearchrole:- Click Users.
- Click New User.
- Type phantomsearchuser in the Name field.
- Set and confirm a password for this user which complies with your organization's security policies.
- Under Assigned role(s), in the Selected item(s) box, select user to remove that role.
- Under Assigned role(s), in the Available item(s) box, select phantomsearch to add that role.
- Deselect the Require password change on first login check box.
- Click Save.
- Create the user account with the
phantomdeleterole:- Click New User.
- Type phantomdeleteuser in the Name field.
- Set and confirm a password for this user which complies with your organization's security policies.
- Under Assigned role(s), in the Selected item(s) box, select user to remove that role.
- Under Assigned role(s), in the Available item(s) box, select phantomdelete to add that role.
- Deselect the Require password change on first login check box.
- Click Save.
Configure Splunk Phantom to use a distributed Splunk platform deployment
After the Splunk Phantom Remote Search app is installed and the required user accounts are created, configure Splunk Phantom to use a distributed Splunk platform deployment.
Required search head information
Verify that you have the following search head information:
- The host names for each search head. For Splunk Cloud, use the name of your search head stack, which looks like
<deployment name>.splunkcloud.com. - The user names and passwords for the user accounts with the
phantomsearchandphantomdeleteroles. - The REST API port numbers for each search head.
When using the Input Data Manager, the HEC token must be generated from the main search head which is the ad-hoc search head in in Splunk Cloud deployments.
Managed Splunk Cloud users must open a support case to open the REST API port for Splunk Cloud. Include a range of IP addresses to authorize access to the REST API from your organization. See How do I file a Splunk Support Case/contact Splunk Support? on Splunk Answers.
Required indexer informattion
Verify that you have the following indexer information:
- Host names for each indexer. For Splunk Cloud, use the
http-inputsprefix for your deployment, which looks likehttp-inputs-<deployment name>.splunkcloud.com. - The HTTP Event Collector port number. The default port is 8088 for HTTP traffic or 443 for HTTPS traffic. Splunk Cloud requires HTTPS.
- The HTTP Event Collector token.
If your indexers are configured behind a load balancer, use the load balancer URL for the indexer host name.
Add search head and indexers
You can add up to 10 search heads and 10 indexers.
- Log in to Splunk Phantom as an administrative user.
- From the main menu, select Administration.
- Select Administration Settings.
- Select Search Settings.
- In the Search Endpoint field, select the radio button for Distributed Splunk Enterprise Deployment.
- Click Search Heads.
- Click Host to expand the Search Heads configuration.
- In the Search Heads section, configure the first search head.
- Type the search head host name in the Host field.
- In the User with Search Privileges section, type the user name and password for the user account with the
phantomsearch role in the Username and Password fields. - In the User with Delete Privileges section, type the user name and password for the user account with the
phantomdeleterole in the Username and Password fields. - Type the port number that the Splunk platform uses to listen for REST API calls in the REST Port field.
- Select the Use SSL for REST check box to enable SSL.
- Select the Verify Certificate for REST checkbox to enable SSL certificate verification.
- Click Add Search Head to configure additional search heads. Each time you add a new search head, the user names and passwords for the user accounts with the
phantomsearchandphantomdeleteroles are prepopulated using the values from the previous search head. - Once all the search heads have been added, click Indexers.
- Click Host to expand the Indexers configuration.
- In the Indexers section, configure the first indexer.
- Type the indexer host name in the Host field.
- Type the HTTP Event Collector port in the HTTP Event Collector Port field.
- Paste the HTTP Event Collector token in the HTTP Event Collector Token field.
- Select the Use SSL for HTTP Event Collector checkbox to enable SSL.
- Select the Verify Certificate for HTTP Event Collector checkbox to enable SSL certificate verification.
- Click Add Indexer to configure additional indexers.
- Once all search heads and indexers have been added, test the connections to your distributed Splunk platform deployment by clicking Test Connection.
- Click Save Changes.
| Connect to a standalone Splunk instance | Modify the srchDiskQuota if you are seeing partial search results |
This documentation applies to the following versions of Splunk® Phantom Remote Search: 1.0.14
 Download manual
Download manual
Feedback submitted, thanks!