Data requirements for Splunk Service Intelligence for SAP Solutions
Service Intelligence for SAP Solutions depends on SAP data available in your Splunk instance through PowerConnect for SAP data collector. Prior to monitoring your SAP systems using Service Intelligence for SAP Solutions and Splunk IT Service Intelligence, install SAP PowerConnect for Splunk on the target SAP systems, and ensure SAP data is being ingested into Splunk.
1. Install the SAP PowerConnect for Splunk app
Download and install SAP PowerConnect for Splunk from Splunkbase. For installation steps, see PowerConnect Splunk App Installation.
2. Take a full ITSI backup
Take a full backup of ITSI. For instructions, see Create a full backup of ITSI in the ITSI Administration Manual.
3. Validate your SAP data
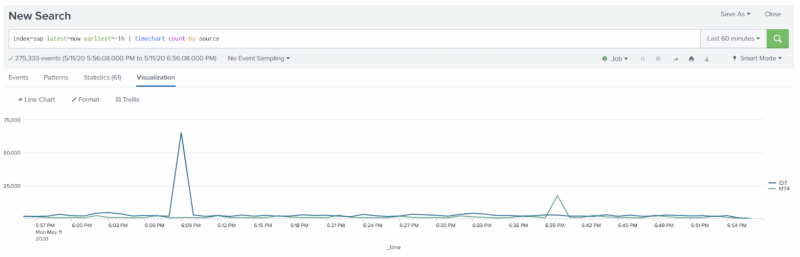
Make sure SAP data is flowing into Splunk before you start the setup process, otherwise ITSI doesn't recognize any systems when you try to import them. To verify that SAP data is flowing into your Splunk instance, run the following search and replace the index name with the name of the index you're using:
index=<name> latest=now earliest=-1h | timechart count by source
When you run the search, make sure you see data similar to the following:
4. (Optional) Use a valid SSL certificate
If you install Service Intelligence for SAP Solutions on premises and your ITSI search head does not have a fully trusted SSL certificate, perform the following tasks:
- Open the folder
<splunk install>/etc/apps/ServiceIntelligenceForSAPSolutions/bin - Open
installpc.pyand edit line 1181 to:r = requests.post(url, files=multiple_files, headers=headers, verify=False)
- Save your changes.
- Restart the ITSI search head.
5. Verify events are being sent
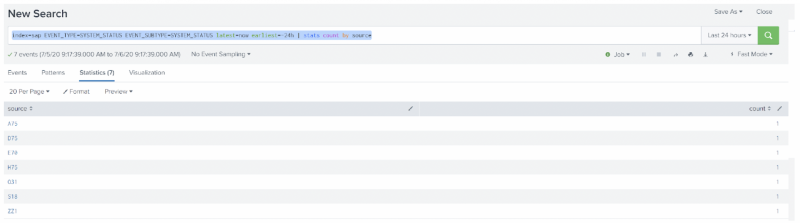
Run the following Splunk search to verify the correct event types are being sent to your Splunk deployment. Replace the index name with name of the index you're using:
index=<name> EVENT_TYPE=SYSTEM_STATUS EVENT_SUBTYPE=SYSTEM_STATUS latest=now earliest=-24h | stats count by source
Make sure you see data similar to the following. The SAP system SID should be listed in the source column:
6. Set macro permissions
Change the permissions of the PowerConnect for Splunk App macros to Global.
- Within Splunk, go to Settings > Advanced search > Search macros.
- Search for the following macros:
- sap-abap(1)
- sap-java
- sap-index
- If the Sharing column doesn't say Global for either of the macros, click Permissions and select All apps (system) to share the macro globally.
- Click Save.
7. Configure lookup table files
- Within Splunk, go to Settings > Lookups > Lookup table files and locate the following lookups:
- sensitive_tcodes.csv
- security_parameters_names.csv
- wide_open_auth_objects.csv
- Change their permissions to Global.
- Within Splunk, go to Settings > Lookups > Lookup definitions and locate the following definitions:
- sensitive_tcodes
- security_parameters_names
- wide_open_auth_objects
- Change their permissions to Global.
As the configure step instructions specify, both lookup definitions and lookup tables need global permissions.
| Release notes for Splunk Service Intelligence for SAP Solutions | Install Splunk Service Intelligence for SAP Solutions |
This documentation applies to the following versions of Splunk® Service Intelligence for SAP® Solutions: 1.0.0, 1.3.2, 2.0.0, 2.1.0, 2.1.1, 2.1.2, 2.1.3, 2.2.0
 Download manual
Download manual
Feedback submitted, thanks!