Splunk App for SOAR Export release notes
Welcome to release 4.2.3
This release of Splunk App for SOAR Export, released on May 31, 2023, includes the following enhancements:
| Feature | Description |
|---|---|
| Self-service install | You can now install Splunk App for SOAR Export from Splunkbase on your own. For details, see Install Splunk App for SOAR Export on Splunk Enterprise and Install Splunk App for SOAR Export on Splunk Cloud Platform. |
| Global field mapping | Added a new button on the Global Field Mapping page, so you can add field mappings from that page. For details, see Configure global field mappings. |
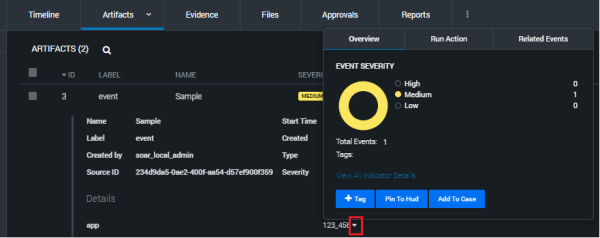
| Artifacts in Splunk SOAR display expanding option | Regardless of whether you specify a Contains field in Splunk App for SOAR Export global field mapping, related artifacts in Splunk SOAR display the small triangle, enabling access to additional information. |
| Custom severity synchronization | You can use any custom severity values you created in your SOAR instance within Splunk App for SOAR Export. For details, see Run adaptive response actions in Splunk ES to send notable events to Splunk SOAR and Connect Splunk App for SOAR Export and the Splunk Platform to a Splunk SOAR server or Splunk SOAR. |
| Custom container name for notables | When setting up a saved search to forward notables, you now have a choice in naming the container created in Splunk SOAR. By default, the new container name has the same name as the alert or adaptive response action. This has been the automatic naming in past releases. With this release, you can now choose to have the container name be the source of the event that triggered the alert or adaptive response action. This is new functionality and does not break any existing adaptive response actions or alerts. For additional details, see Run adaptive response actions in Splunk ES to send notable events to Splunk SOAR. |
| Notable ID sent to Splunk SOAR | If you create a correlation search for an adaptive response action that creates a notable, along with your Send to SOAR or Run Playbook in SOAR request, the event_id of the notable is also sent to Splunk SOAR as a CEF value in the artifact. |
| Updated props.conf | Updated several aspects of props.conf, including the following: ingesting logs is now more performant log_level is now available for viewing and parsing sourcetype for the following logs no longer have numbers or "small" appended to the end of their names: phantom_forwarding, phantom_configuration, phantom_retry |
| New sc_admin role | The new sc_admin role now has Splunk App for SOAR Export capabilities, specified in the authorize.conf file. A user with the sc_admin role can now assign Splunk App for SOAR Export roles, along with the phantom_read and phantom_write capabilities to other users in Splunk Cloud.
This role is also imported during installation for Splunk Enterprise, but has no effect on, and no administrative capabilities within, the Splunk Enterprise installation. |
Fixed issues in this release
This version of Splunk App for SOAR Export fixes the following issues:
| Date resolved | Issue number | Description |
|---|---|---|
| 2023-03-20 | PAPP-27021 | ES Adaptive Response Action Recorded Success Twice |
| 2022-10-19 | PAPP-27172 | Updating forwarding rule results in error "A saved search with that name already exists" |
| 2022-09-29 | PAPP-26850 | ITSI - Event forwarding configurations were not being updated to either enabled or disabled. (SOAR EXPORT) |
Known issues in this release
This version of Splunk App for SOAR Export has the following known issues:
| Date filed | Issue number | Description |
|---|---|---|
| 2024-02-28 | PAPP-33280 | Adaptive Response Action needs more time to send data |
| 2023-12-07 | PAPP-32614 | If field names mapped, Artifacts tab only needs to display custom mapped field names and not original field names Workaround: no workaround found |
| 2023-11-21 | PAPP-32468 | Failed adaptive response action statuses erroneously display as successful Workaround: To see the accurate status, refresh the page after about 30 minutes. |
| 2023-08-08 | PAPP-31554 | Artifact title missing in SOAR when posting via scheduled alert actions |
| 2023-08-03 | PAPP-31536 | Red sensitivity auto populated |
| 2023-07-19 | PAPP-31340 | ES Notable multiline comments are not exported to SOAR Workaround: No workaround is available. |
| 2023-07-18 | PAPP-31327 | Default severities not retrieved for servers without Observer role |
| 2023-05-25 | PAPP-30740 | Alert action 'sensitivity' field appears to already select 'Red'; requires making a selection Workaround: Select a sensitivity setting, although it looks like 'Red' is already selected. |
| 2021-05-19 | PAPP-17108 | Adaptive Response Relay produces error message in Cloud Workaround: Create a saved search report to invoke Send to SOAR or Run SOAR Playbook actions, as described in these steps:
If the key word | eval _phantom_workaround_description = [| rest /services/saved/searches/Test%20Alert%20Title | eval desc="\"".description."\"" |return $desc] |
| About Splunk App for SOAR Export |
This documentation applies to the following versions of Splunk® App for SOAR Export: 4.2.3
 Download manual
Download manual
Feedback submitted, thanks!