Change default values
Before you begin configuring Splunk Enterprise for your environment, check through the following default settings.
Set or change environment variables
You can change how Splunk Enterprise starts by setting environment variables on your operating system.
On *nix, use the setenv or export commands to set a particular variable. For example:
# export SPLUNK_HOME = /opt/splunk02/splunk
To set the environment permanently, edit the appropriate shell initialization file. Add entries for the variables you want Splunk Enterprise to use when it starts up.
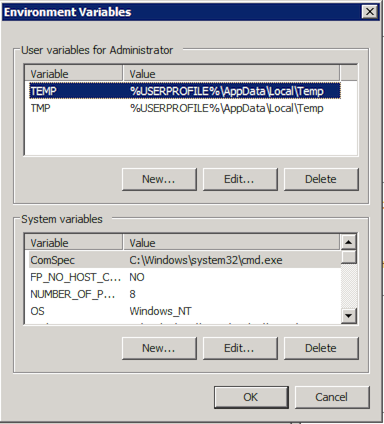
On Windows, use the set environment variable in either a command prompt or PowerShell window:
C:\> set SPLUNK_HOME = "C:\Program Files\Splunk"
To set the environment permanently, use the "Environment Variables" window to add the entry to the "User variables" list.
There are several environment variables that are available:
| Environment variable | Purpose |
|---|---|
SPLUNK_HOME
|
The fully qualified path to the Splunk Enterprise installation directory. |
SPLUNK_DB
|
The fully qualified path to the directory that contains the Splunk Enterprise index directories. |
SPLUNK_BINDIP
|
The IP address on the system that Splunk Enterprise should bind to on startup to accept connections. Useful for when a host has more than one live IP address. |
SPLUNK_IGNORE_SELINUX
|
Tells Splunk Enterprise to attempt to start when running in Linux host with SELinux enabled. By default, Splunk Enterprise quits immediately when it detects that SELinux is active. This variable defeats that check and can be used in scenarios where you have configured SELinux to allow Splunk Enterprise to work. |
SPLUNK_OS_USER
|
Tells Splunk Enterprise to assume the credentials of the user you specify, regardless of what user you started it as. For example, if you specify the user 'splunk' on your system and start Splunk Enterprise as root, it adopts the privileges of the 'splunk' user and any files written by those processes will be owned by the 'splunk' user. |
SPLUNK_SERVER_NAME
|
The name of the splunkd service (on Windows) or process (on *nix). Do not set this variable unless you know what you are doing. |
SPLUNK_WEB_NAME
|
The name of the splunkweb service (on Windows) or process (on *nix). Do not set this variable unless you know what you are doing. |
You can also edit these environment variables for each instance by editing splunk-launch.conf or, in some cases, web.conf. This is handy when you run more than one Splunk software instance on a host. See "splunk-launch.conf".
Change the admin default password
Splunk Enterprise has a default administration account and password, admin/changeme. Splunk recommends strongly that you change the default in order to keep your system secure. Your password should be complex and follow general password best practices:
- Use a combination of words, numbers, symbols, and both upper- and lower-case letters.
- Complexity is important, but length is vital. We recommend a minimum of 10 characters.
- Do not choose passwords based upon details that might not be confidential, such as your birth date, your Social Security or phone number, or names of family members.
- Do not use words that can be found in the dictionary.
- Do not use a password you use or have used elsewhere.
Change the password using Splunk Web
To change the admin default password:
- Log into Splunk Web as the admin user.
- Click Settings in the top-right of the interface.
- Click Access controls in the Users and Authentication section of the screen.
- Click Users.
- Click the admin user.
- Update the password, and click Save.
Change the password using the CLI
The Splunk CLI command is:
splunk edit user
Important: You must authenticate with the existing password before you can change it. Log into Splunk Enterprise via the CLI or use the -auth parameter. For example, this command changes the admin password from changeme to foo:
splunk edit user admin -password foo -role admin -auth admin:changeme
Note: On *nix operating systems, the shell interprets some special characters as command directives. You must either escape these characters by preceding them with \ individually, or enclose the password in single quotes ('). For example:
splunk edit user admin -password 'FFL14io!23ur$' -role admin -auth admin:changeme
or
splunk edit user admin -password FFL14io!23ur\$ -role admin -auth admin:changeme
On Windows, use the caret (^) to escape reserved shell characters, or enclose the password in double-quotes ("). For example:
splunk edit user admin -password "FFL14io!23ur>" -role admin -auth admin:changeme
or
splunk edit user admin -password FFL14io!23ur^> -role admin -auth admin:changeme
Note: You can also reset all of your passwords across servers at once. See "Deploy secure passwords across multiple servers for the procedure.
Change network ports
Splunk Enterprise configures a few ports at installation time:
- The HTTP/HTTPS port. This port provides the socket for Splunk Web. It defaults to 8000.
- The appserver port. 8065 by default.
- The management port. This port is used to communicate with the
splunkddaemon. Splunk Web talks tosplunkdon this port, as does the command line interface and any distributed connections from other servers. This port defaults to 8089. - The KV store port. 8191 by default.
Important: During installation, you might have set these ports to values other than the defaults.
Note: Splunk instances receiving data from forwarders must be configured with an additional port, the receiver port. They use this port to listen for incoming data from forwarders. This configuration does not occur during installation. The default receiver port is 9997. For more information, see "Enable a receiver" in the Forwarding Data Manual.
Use Splunk Web
To change the ports from their installation settings:
- Log into Splunk Web as the admin user.
- Click Settings in the top-right of the interface.
- Click the Server settings link in the System section of the screen.
- Click General settings.
- Change the value for either Management port or Web port, and click Save.
Use Splunk CLI
To change the port settings via the Splunk CLI, use the CLI command set. For example, this command sets the Splunk Web port to 9000:
splunk set web-port 9000
This command sets the splunkd port to 9089:
splunk set splunkd-port 9089
Change the default Splunk server name
The Splunk server name setting controls both the name displayed within Splunk Web and the name sent to other Splunk Servers in a distributed setting.
The default name is taken from either the DNS or IP address of the Splunk Server host.
Use Splunk Web
To change the Splunk server name:
- Log into Splunk Web as the admin user.
- Click Settings in the top-right of the interface.
- Click the Server settings link in the System section of the screen.
- Click General settings.
- Change the value for Splunk server name, and click Save.
Use Splunk CLI
To change the server name via the CLI, use the set servername command. For example, this command sets the server name to foo:
splunk set servername foo
Changing the datastore location
The datastore is the top-level directory where the Splunk Server stores all indexed data.
Note: If you change this directory, the server does not migrate old datastore files. Instead, it starts over again at the new location.
To migrate your data to another directory follow the instructions in "Move an index".
Use Splunk Web
To change the datastore location:
- Log into Splunk Web as the admin user.
- Click Settings in the top-right of the interface.
- Click the System settings link in the System section of the screen.
- Click General settings.
- Change the path in Path to indexes, and click Save.
- Use the CLI to restart Splunk Enterprise. Navigate to
$SPLUNK_HOME/bin/(*nix) or%SPLUNK_HOME%\bin(Windows) and run this command:
splunk restart
Important: Do not use the restart function inside Settings. This will not have the intended effect of causing the index directory to change. You must restart from the CLI.
Use Splunk CLI
To change the datastore directory via the CLI, use the set datastore-dir command. For example, this command sets the datastore directory to /var/splunk/:
splunk set datastore-dir /var/splunk/
Set minimum free disk space
The minimum free disk space setting controls how low disk space in the datastore location can fall before Splunk software stops indexing.
Splunk software resumes indexing when more space becomes available.
Use Splunk Web
To set minimum free disk space:
- Log into Splunk Web as the admin user.
- Click Settings in the top-right of the interface.
- Click the System settings link in the System section of the screen.
- Click General settings.
- Change the value for Pause indexing if free disk space falls below, and click Save.
Use Splunk CLI
To change the minimum free space value via the CLI, use the set minfreemb command. For example, this command sets the minimum free space to 2000 MB:
splunk set minfreemb 2000
Set the default time range
The default time range for ad hoc searches in the Search & Reporting App is set to Last 24 hours. An administrator can set the default time range globally, across all apps. The setting is stored in SPLUNK_HOME/etc/apps/user-prefs/local/user-prefs.conf file in the [general_default] stanza.
This setting applies to all Search pages in Splunk Apps, not just the Search & Reporting App. This setting applies to all user roles.
Note: This setting does not apply to dashboards.
Use Splunk Web
1. Log into Splunk Web as the admin user.
2. Click Settings.
3. In the System section, click Server settings.
4. Click Search Preferences.
5. From the Default search time range drop-down, select the time that you want to use and click Save.
Time range settings in the ui_prefs.conf file
You might already have a time range setting in the ui-prefs.conf file for a specific application or user. The settings in the ui-prefs.conf file take precedence over any settings that you make to the global default time range using Splunk Web.
However, if you want to use the global default time range for all users and applications, consider removing the settings you have in the ui-prefs.conf file.
Other default settings
The Splunk Web Settings General Settings screen has a few other default settings that you might want to change. Explore the screen to see the range of options.
See also
| Install your license | Bind Splunk to an IP |
This documentation applies to the following versions of Splunk® Enterprise: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.7, 7.0.8, 7.0.9, 7.0.10, 7.0.11, 7.0.13
 Download manual
Download manual
Feedback submitted, thanks!