erex
Description
Use the erex command to extract data from a field when you do not know the regular expression to use. The command automatically extracts field values that are similar to the example values you specify.
If you specify a field argument, the values extracted from the fromfield argument are saved to the field. Otherwise, the search returns a regular expression that you can then use with the rex command to extract the field.
Syntax
erex [<field>] examples=<string> [counterexamples=<string>] [fromfield=<field>] [maxtrainers=<int>]
Required arguments
- examples
- Syntax: examples=<string>,<string>...
- Description: A comma separated list of example values for the information to extract and save into a new field. Use quotation marks around the list if the list contains spaces. For example:
"port 3351, port 3768".
Optional arguments
- counterexamples
- Syntax: counterexamples=<string>,<string>,...
- Description: A comma-separated list of example values that represent information not to be extracted.
- field
- Syntax: <string>
- Description: A name for a new field that will take the values extracted from
fromfield. If field is not specified, values are not extracted, but the resulting regular expression is generated and placed as a message under the Jobs menu in Splunk Web. That regular expression can then be used with therexcommand for more efficient extraction.
- fromfield
- Syntax: fromfield=<field>
- Description: The name of the existing field to extract the information from and save into a new field.
- Default:
_raw
- maxtrainers
- Syntax: maxtrainers=<int>
- Description: The maximum number values to learn from. Must be between 1 and 1000.
- Default: 100
Usage
The values specified in the examples and counterexample arguments must exist in the events that are piped into the erex command. If the values do not exist, the command fails.
To make sure that the erex command works against your events, first run the search that returns the events you want without the erex command. Then copy the field values that you want to extract and use those for the example values with the erex command.
Examples
1. Extract values based on an example
The following search extracts out month and day values like 7/01 and puts the values into the monthday attribute.
... | erex monthday examples="7/01"
2. Extract values based on examples and counter examples
The following search extracts out month and day values like 7/01 and 7/02, but not patterns like 99/2. The extracted values are put into the monthday attribute.
... | erex monthday examples="7/01, 07/02" counterexamples="99/2"
3. Extract values based on examples and return the most common values
| This example uses the sample data from the Search Tutorial. To try this example on your own Splunk instance, you must download the sample data and follow the instructions to get the tutorial data into Splunk. Use the time range All time when you run the search. |
- Display a list of ports for potential attackers. First, run the search for these potential attackers to find example port values.
sourcetype=secure* port "failed password" - Then use the
erexcommand to extract the port field. Use thetopcommand to return the most common port values.
sourcetype=secure* port "failed password" | erex port examples="port 3351, port 3768" | top port
This search returns a table with the count of top ports that match the search.
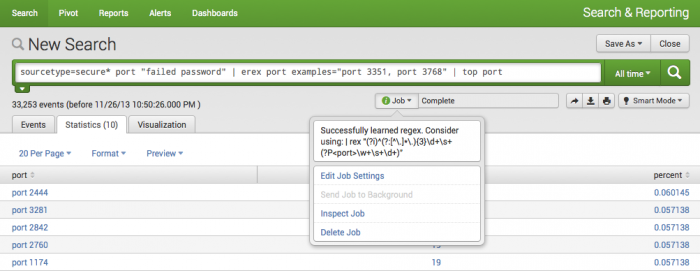
- Click the Jobs menu to see the generated regular expression based on your examples. You can use the
rexcommand with the regular expression instead of using theerexcommand.
See also
extract, kvform, multikv, regex, rex, xmlkv
Answers
Have questions? Visit Splunk Answers and see what questions and answers the Splunk community has using the erex command.
| diff | eval |
This documentation applies to the following versions of Splunk® Enterprise: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.7, 7.0.8, 7.0.9, 7.0.10, 7.0.11, 7.0.13
 Download manual
Download manual
Feedback submitted, thanks!