Search modes
You can use the Search Mode selector to provide a search experience that fits your needs.
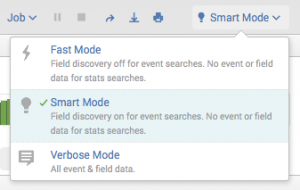
The search mode selector is on the right side of the Search bar. The modes are Smart (default), Fast, and Verbose:
Depending on the mode you set, you can see all the data available for your search but at the expense of longer search times, or you can speed up and streamline your search in certain ways.
The Fast and Verbose modes represent the two ends of the search mode spectrum. The default Smart mode switches between the Fast and Verbose modes depending on the type of search that you are running. When you first run a saved search, it runs in the Smart mode.
Using the Fast mode
The Fast mode prioritizes the performance of the search and does not return nonessential field or event data. This means that the search returns what is essential and required.
- Disables field discovery. Field discovery is the process Splunk software uses to extract fields aside from default fields such as
host,source, andsourcetype. The Splunk software only returns information on default fields and fields that are required to fulfill your search. If you are searching on specific fields, those fields are extracted. - Only depicts search results as report result tables or visualizations when you run a reporting search. A reporting search is a search that includes transforming commands. Under the Fast mode you will see only event lists and event timelines for searches that do not include transforming commands.
For more information about what the Splunk software does when field discovery is enabled or disabled, see "When extracts fields" in the Knowledge Manager Manual.
Using the Verbose mode
The Verbose mode returns all of the field and event data it possibly can, even if it means the search takes longer to complete, and even if the search includes reporting commands.
- Discovers all of the fields it can. This includes default fields, automatic search-time field extractions, and all user-defined index-time and search-time field extractions. Discovered fields are displayed in the left-hand fields sidebar in the Events results tab.
- Returns an event list view of results and generates the search timeline. It also generates report tables and visualizations if your search includes reporting commands.
You may want to use the Verbose mode if you are putting together a transforming search but are not exactly sure what fields you need to report on, or if you need to verify that you are summarizing the correct events.
Note: Reports cannot benefit from report acceleration when you run them in Verbose mode. If you enable report acceleration for a report and it has been running faster as a result, be aware that if you switch the mode of the search to Verbose it will run at a slower, non-accelerated pace.
Report acceleration is designed to be used with slow-completing searches that have over 100k events and which utilize transforming commands. For more information see "Accelerate reports," in the Reporting Manual.
Using the Smart mode
All reports run in Smart mode, the default search mode, after they are first created. By design, Smart mode returns the best results for whatever search or report you run. If you search on events, you get all the event information you need. If your run a transforming search, the Splunk software favors speed over thoroughness and brings you straight to the report result table or visualization.
When you run a Smart mode search that does not include transforming commands, the search behaves as if it were in Verbose mode.
- Discovers all the fields it can.
- Generates the full event list and event timeline. No event table or visualization will appear because you need transforming commands to make those happen.
When you run a Smart mode search that includes transforming commands, the search behaves as if it were in Fast mode.
- Disables field discovery.
- Does not waste time generating the event list and event timeline and jumps you straight to the report result table or visualization.
For more information about transforming commands and transforming searches, see "About reporting commands" in the Search Manual.
| Search actions | Search history |
This documentation applies to the following versions of Splunk® Enterprise: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.7, 7.0.8, 7.0.9, 7.0.10, 7.0.11, 7.0.13
 Download manual
Download manual
Feedback submitted, thanks!