Manage source types
The "Source Types" page lets you create, edit, and delete source types. It loads when you select "Source types" from the Settings menu. While this page and the "Set Sourcetypes" page have similar names, it is different from that page.
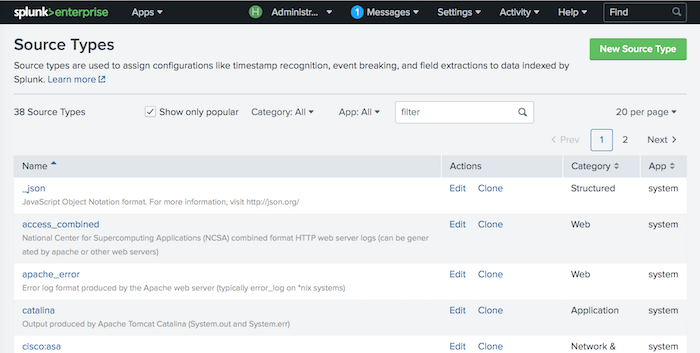
The Source Types page displays all source types that have been configured on the instance. It shows the default source types provided by your Splunk deployment and any source types that you have added.
Sort source types
By default, the Source Types management page sorts source types alphabetically. You can change how the page sorts by clicking the header bar for the "Name", "Category", and "App" columns.
Each header bar (except for "Actions") acts as a toggle. Click once to sort in ascending order and click again to sort in descending order.
Filter source types
You can filter the number of source types you see n the Source Type management page.
- To see only the most common source types, click the Show only popular checkbox along the top of the page. Popular source types are the most common source types that customers use. They have a
pulldown_typesource type field value of 1. When the "Show only popular" checkbox is not selected, the page shows all source types that have been defined on the instance.
- To see only source types that belong to a certain category, click the Category drop-down and select the category you want. Only source types that belong to that category will display. To see all source types again, select "All" from the "Category" drop-down.
- To see only source types that belong in a certain application context, click the App drop-down and select the application context that the source type applies to. Only source types that apply to that application context will display. To see all source types again, select "All" from the "App" drop-down.
- To see only source types whose names contain a certain string, type that string in the Filter text box next to the "App" drop-down, then press Enter. Only source types whose names or descriptions match what you have typed in the "Filter" box display. To se all source types again, click the "x" button on the right side of the "Filter" text box.
By default, the Source Types management page shows up to 20 source types on a page. If you want to see more or less, click the 20 per page link on the right side of the page and select the number of source types you want to see. Choices are 10, 20, 50, or 100 listings on a page.
Modify source types
To modify a source type, click its name in the list, or click its Edit link in the Actions column. The "Edit Source type" page appears.
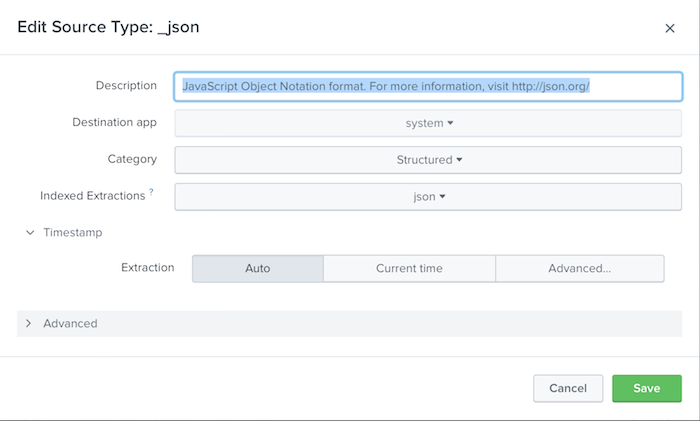
The Edit Source Type dialog box lets you change the configuration of a source type. You can change the following:
Description: Type in the description of the source type in the "Description" field.
Destination app: The application context that the source type applies to.
Note: You cannot change the app destination for source types that come with Splunk software.
Category: The category that the source type is a member of. Click the button to select from the list of categories and choose the one you want. When you save, the source type appears in the category you selected.
Indexed Extractions: A format for extracting fields at index time from files with structured data. Select the type of indexed extraction that best represents the contents of the file:
- none: The file does not contain structured data.
- json: The file is in JavaScript Object Notation (json) format.
- csv: The file has comma-separated values.
- tsv: The file has tab-separated values.
- psv: The file has pipe (|) separated values.
- w3c: The file conforms to the World Wide Web Consortium (W3C) logging format.
Timestamp:
The Timestamp section of the dialog controls how timestamps are determined for events from the source file.
- Auto: Use default logic to extract timestamp from event.
- Current Time: Use current system time
- Advanced: Use advanced internal logic to extract timestamp from event.
Advanced time stamp extraction configurations
The following advanced configurations are available when you select Advanced in the "Timestamp Extraction" section:
- Time zone: Specify the time zone to be assigned to the timestamps.
- Timestamp format: Specify the format of the time stamp in the source event. The available formats come from the properties of the
strptime()programming function. For example, if the source file contains logs with timestamps in this format:
6 Jun 2015 18:35:05
...specify the following in the "Timestamp format" field:
%d %b %Y %H:%M:%S
Another example:
Tue Jun 4 2:55:18 PM 2015
maps to
%a %b %d %I:%M:%S %p %Y
For a list of the strings that you can use to define the time stamp format, see strptime(3) (http://linux.die.net/man/3/strptime) on the die.net Linux man page site.
Timestamp prefix: A regular expression that represents the characters that come before a time stamp. When Splunk software sees this set of characters in an event, it expects a time stamp to occur after that.
Lookahead: Specifies the maximum number of characters to scan into an event for the time stamp. If you specified a regular expression in the "Timestamp prefix" field, it looks no more than the number of characters specified past the string that the regular expression represents for the time stamp.
Advanced
The Advanced section of the dialog shows you all of the configurations for the source type, in key/value format. This represents what is in the props.conf file that defines the source type. You can edit each setting directly, or add and delete settings. To delete settings, click the "x" on the right side of each setting. To add an entry, click the "New setting" link at the bottom of the dialog. This exposes a key/value pair of fields. Enter the key name in the "Name" field and its value in the "Value" field.
Caution: Use the "Advanced" section with care. Adding or changing values here can cause data to be incorrectly indexed.
Add Source Type
To create a new source type, click the New Source Type button at the top right of the screen. The Create Source Type dialog box opens.
This dialog is exactly the same as the "Edit Source Type" dialog. See "Managesourcetypes for information on the controls in the dialog.
When you have finished configuring the source type, click "Save."
Delete Source Type
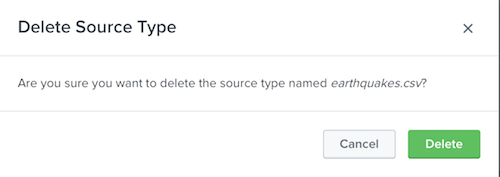
To delete a source type, click the Delete link in the "Actions" column for the source type that you want to delete. You cannot delete built-in source types, only source types that you create or that come with apps.
When you delete a source type, the following dialog appears:
Caution: Deleting a source type has significant consequences, especially if the source type is already in use:
- Data can be indexed incorrectly after you delete the source type. Making the data searchable in the way you want later can take a lot of effort. Many apps and add ons use source types to look for data, and data indexed under a missing source type is data those apps and add-ons do not see.
- Any configurations that the source type uses, such as field extractions, index time filtering, and time stamp formats, are irretrievably lost.
- You cannot undo a source type deletion. The only options available in this case are to restore the
props.conffile that defines the source type from a backup, or recreate the source type manually.
If you are sure you want to delete the source type, click "Delete". The dialog closes and Splunk Web returns you to the Source Types management page.
| Create source types | Rename source types at search time |
This documentation applies to the following versions of Splunk® Enterprise: 7.1.0, 7.1.1, 7.1.2, 7.1.3, 7.1.4, 7.1.5, 7.1.6, 7.1.7, 7.1.8, 7.1.9, 7.1.10
 Download manual
Download manual
Feedback submitted, thanks!